CyberheistNews Vol 7 #44
[ALERT] This Scary New Phishing Attack Is Very Hard to Detect 
You need to know about a new phishing attack vector reported by our friends at Barkly. It utilizes a new technique that's just plain nasty.
This week, users at one of their customers began receiving emails from known contacts they had at another organization. In the screenshot below you can see that at least one of the emails appeared to be a reply to an existing email thread, where users at the two organizations had been emailing back and forth.
The new message was noticeably short — "Morning, please see attached and confirm" (you probably see where this is going) — but in the context of the email chain it was very convincing. The email appears to come from a person at a company the receiver has been emailing with, and this message appears to be a reply to a legit email chain. Yikes. Here is a picture of how it looks:
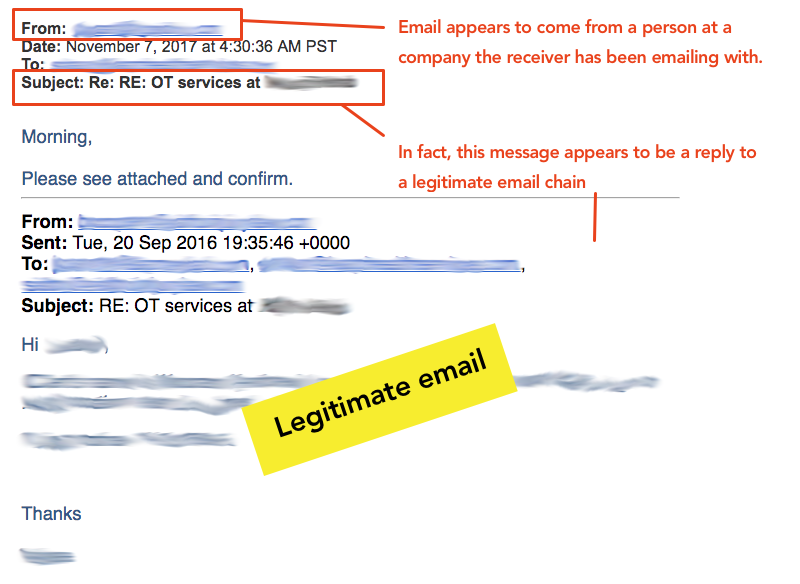
The aim was to have the user open the Word attachment, and follow instructions to enable macros.
Technical background of the attack
The user on the other end had been infected with a new variant of Ursnif, one of the most active and widespread banking Trojans in the world.
Investigation showed that the Word doc the user downloaded contained a macro that, when activated, launched PowerShell script designed to download the Ursnif payload.
Ursnif is a powerful trojan with a lot of features like stealing victim credentials in a variety of ways via man-in-the-browser attacks, keylogging, screenshot capture, etc.
It looks like the evil masterminds behind Ursnif are now taking it one step further and use the compromised email accounts of its victims to spread the infection like a worm.
It's turning infected workstations into spam factories
What makes this social engineering attack so tricky is that the email pictured above wasn't just coming from an organization the recipient knew and had been emailing with, it came as a reply to an existing email chain. That is a hard one for a user not to fall for, they really need to be on their toes to catch this one.
Ursnif isn't the only trojan we've seen hijacking victim email accounts. In July, we saw the Emotet trojan doing something similar.
Now, compromised accounts have been a thing since email has been around, so getting a infected email from a trusted source is nothing new, but if this is becoming a larger trend it is even more important to mitigate before your own network starts spewing out malicious attacks and your mail server gets on blacklists.
What You Can Do About It
Here are some suggestions how to counter attacks like this using as many layers of your defense-in-depth as possible:

You need to know about a new phishing attack vector reported by our friends at Barkly. It utilizes a new technique that's just plain nasty.
This week, users at one of their customers began receiving emails from known contacts they had at another organization. In the screenshot below you can see that at least one of the emails appeared to be a reply to an existing email thread, where users at the two organizations had been emailing back and forth.
The new message was noticeably short — "Morning, please see attached and confirm" (you probably see where this is going) — but in the context of the email chain it was very convincing. The email appears to come from a person at a company the receiver has been emailing with, and this message appears to be a reply to a legit email chain. Yikes. Here is a picture of how it looks:

The aim was to have the user open the Word attachment, and follow instructions to enable macros.
Technical background of the attack
The user on the other end had been infected with a new variant of Ursnif, one of the most active and widespread banking Trojans in the world.
Investigation showed that the Word doc the user downloaded contained a macro that, when activated, launched PowerShell script designed to download the Ursnif payload.
Ursnif is a powerful trojan with a lot of features like stealing victim credentials in a variety of ways via man-in-the-browser attacks, keylogging, screenshot capture, etc.
It looks like the evil masterminds behind Ursnif are now taking it one step further and use the compromised email accounts of its victims to spread the infection like a worm.
It's turning infected workstations into spam factories
What makes this social engineering attack so tricky is that the email pictured above wasn't just coming from an organization the recipient knew and had been emailing with, it came as a reply to an existing email chain. That is a hard one for a user not to fall for, they really need to be on their toes to catch this one.
Ursnif isn't the only trojan we've seen hijacking victim email accounts. In July, we saw the Emotet trojan doing something similar.
Now, compromised accounts have been a thing since email has been around, so getting a infected email from a trusted source is nothing new, but if this is becoming a larger trend it is even more important to mitigate before your own network starts spewing out malicious attacks and your mail server gets on blacklists.
What You Can Do About It
Here are some suggestions how to counter attacks like this using as many layers of your defense-in-depth as possible:
- Disable MS Office macros network-wide if possible
- Check your firewall rules to make sure this type of attachment is at least flagged as potentially dangerous or quarantined
- Configure your email servers/filters to block attachments containing VBA/Macro code
- Configure the endpoint security software on the workstation to catch malicious attachments
- Install a (complimentary) Phish Alert button in Outlook, so users can simply click on that, delete the email and forward it to your Incident Response team: https://info.knowbe4.com/phish-alert-chn
Step your users through new-school security awareness training and send them simulated phishing attacks with Word docs that have Macros, to inoculate them against attacks like this when (not if) your filters do not catch them
Spy vs. Spy? Wikileaks Says CIA Impersonated Kaspersky Lab
Wow, the plot thickens. Attribution indeed is a very murky business.
According to Wikileaks, its analysis revealed that by using fake certificates, the CIA made it look like data was being exfiltrated by one of the impersonated entities – in this case Kaspersky Lab.
“We have investigated the claims made in the Vault 8 report published on November 9 and can confirm the certificates in our name are fake,” Kaspersky Lab told SecurityWeek. “Our private keys, services and customers are all safe and unaffected.”
The news that the CIA may have impersonated Kaspersky Lab in its operations has led some to believe that the U.S. may have actually used such tools to falsely pin cyberattacks on Russia. More at SecurityWeek:
http://www.securityweek.com/wikileaks-says-cia-impersonated-kaspersky-lab
Wow, the plot thickens. Attribution indeed is a very murky business.
According to Wikileaks, its analysis revealed that by using fake certificates, the CIA made it look like data was being exfiltrated by one of the impersonated entities – in this case Kaspersky Lab.
“We have investigated the claims made in the Vault 8 report published on November 9 and can confirm the certificates in our name are fake,” Kaspersky Lab told SecurityWeek. “Our private keys, services and customers are all safe and unaffected.”
The news that the CIA may have impersonated Kaspersky Lab in its operations has led some to believe that the U.S. may have actually used such tools to falsely pin cyberattacks on Russia. More at SecurityWeek:
http://www.securityweek.com/wikileaks-says-cia-impersonated-kaspersky-lab
Google: Our Hunt for Hackers Reveals Phishing Is Far Deadlier Than Data Breaches
The study finds that victims of phishing are 400 times more likely to have their account hijacked than a random Google user, a figure that falls to 10 times for victims of a data breach. The difference is due to the type of information that so-called phishing kits collect.
Google has released the results of a year-long investigation into Gmail account hijacking, which finds that phishing is far riskier for users than data breaches.
Hardly a week goes by without a new data breach being discovered, exposing victims to account hijacking if they used the same username and password on multiple online accounts.
While data breaches are bad news for internet users, Google's study finds that phishing is a much more dangerous threat to its users in terms of account hijacking. More at the KnowBe4 blog:
https://blog.knowbe4.com/google-our-hunt-for-hackers-reveals-phishing-is-far-deadlier-than-data-breaches
The study finds that victims of phishing are 400 times more likely to have their account hijacked than a random Google user, a figure that falls to 10 times for victims of a data breach. The difference is due to the type of information that so-called phishing kits collect.
Google has released the results of a year-long investigation into Gmail account hijacking, which finds that phishing is far riskier for users than data breaches.
Hardly a week goes by without a new data breach being discovered, exposing victims to account hijacking if they used the same username and password on multiple online accounts.
While data breaches are bad news for internet users, Google's study finds that phishing is a much more dangerous threat to its users in terms of account hijacking. More at the KnowBe4 blog:
https://blog.knowbe4.com/google-our-hunt-for-hackers-reveals-phishing-is-far-deadlier-than-data-breaches
Don't Miss My Live Webinar: Phishing and Social Engineering in 2018
Here is your invite for this once-a-year Live Webinar: Phishing and Social Engineering in 2018: Is the Worst Yet to Come?
Ransomware has tipped the 1 billion mark and damages are expected to be around 5 billion before the year is out. Use of ransomware has evolved throughout the year with a 600% rise in URL emails delivering malware in just Q3 2017. CEO fraud (aka Business Email Compromise) has cost another 5 billion according to the FBI as of May 2017.
What's next and how can you protect your organization?
Join CyberheistNews Editor-in-Chief and KnowBe4 CEO Stu Sjouwerman for this 30-minute webinar:
“Phishing and Social Engineering in 2018: Is the Worst Yet to Come?” Stu will discuss some of the latest trends in cybercrime and give you an insider perspective on what to expect for 2018 and how to prepare for it.
Key topics covered in this webinar:
Register Now:
https://attendee.gotowebinar.com/register/4082941158725766914?source=CHN
Let's stay safe out there.
Here is your invite for this once-a-year Live Webinar: Phishing and Social Engineering in 2018: Is the Worst Yet to Come?
Ransomware has tipped the 1 billion mark and damages are expected to be around 5 billion before the year is out. Use of ransomware has evolved throughout the year with a 600% rise in URL emails delivering malware in just Q3 2017. CEO fraud (aka Business Email Compromise) has cost another 5 billion according to the FBI as of May 2017.
What's next and how can you protect your organization?
Join CyberheistNews Editor-in-Chief and KnowBe4 CEO Stu Sjouwerman for this 30-minute webinar:
“Phishing and Social Engineering in 2018: Is the Worst Yet to Come?” Stu will discuss some of the latest trends in cybercrime and give you an insider perspective on what to expect for 2018 and how to prepare for it.
Key topics covered in this webinar:
- Understanding the current threat landscape
- What scary new threats will be on the rise for 2018
- Next innovations of ransomware, phishing and social engineering
- What you can do to make your organization a harder target for cybercrime
- How to create your “human firewall”
Register Now:
https://attendee.gotowebinar.com/register/4082941158725766914?source=CHN
Let's stay safe out there.
Warm Regards,
Stu Sjouwerman
Founder and CEO
KnowBe4, Inc.
Quotes of the Week
"To find yourself, think for yourself." - Socrates - Philosopher (469 - 399 BC)
"This above all; to thine own self be true." - William Shakespeare (1564 - 1616)
Thanks for reading CyberheistNews
"This above all; to thine own self be true." - William Shakespeare (1564 - 1616)
Thanks for reading CyberheistNews
Security News
Scam of the Week: "Cyber Monday Is Scammer Heaven"
The majority of consumers aware of online phishing scams, but still may fall victim this cyber Monday...
DomainTools, a leader in domain name and DNS-based cyber threat intelligence, released the findings of their 2017 Cyber Monday Phishing Survey this week.
The survey results highlighted that two in five U.S. consumers have fallen victim to an online phishing attack, despite the fact that 91 percent are aware of the existence of these spoofed websites or emails of trusted brands.
As the holiday shopping season approaches, 92 percent of all consumers shop online and about half are planning to shop online on Cyber Monday, exposing an opportunity for malicious hackers to strike. DomainTools has illustrated its key findings in an InfoGraphic:
https://blog.domaintools.com/2017/11/cyber-monday-deal-or-phishing-scam/
"Cyber Monday has grown in popularity year over year, and unfortunately, so has phishing and online counterfeiting. A range of techniques are used to trick shoppers into visiting a fake website or clicking on a malicious link.
This can result in a shopper unintentionally sharing financial and personal information with these criminals or even downloading ransomware," said Tim Chen, CEO of DomainTools. "As shoppers search for Cyber Monday deals, it's important that they remember to look closely at links and email addresses before clicking. If something seems too good to be true, it may instead be very fake and very bad."
I suggest you send this reminder to your users. You're welcome to copy/paste/edit
"Cyber Monday Is Scammer Heaven"
"It's Holiday Season for the bad guys too! But not the way you might think. They go into scam-overdrive mode. Black Friday and Cyber Monday are the busiest on-line shopping days and they are out to get rich with your money. So what to look out for?
At the moment, there are too-good-to-be-true coupons that offer complimentary phones or tablets all over sites on the Internet. Don't fall for it. Make sure the offers are from a legitimate company. While we're at it...
Watch out for alerts via email or text that you just received a package from FedEx, UPS or the US Mail, and then asks you for some personal information. Don't enter anything. Think Before You Click!
So, especially now, the price of freedom is constant alertness and willingness to fight back. Remember to only use credit cards online, never debit cards. Be super-wary of bulk email with crazy good BUY NOW offers and anything that looks slightly "off". If you think you might have been scammed, stay calm and call your credit card company, nix that card and get a new one.
Happy Holidays!"
The majority of consumers aware of online phishing scams, but still may fall victim this cyber Monday...
DomainTools, a leader in domain name and DNS-based cyber threat intelligence, released the findings of their 2017 Cyber Monday Phishing Survey this week.
The survey results highlighted that two in five U.S. consumers have fallen victim to an online phishing attack, despite the fact that 91 percent are aware of the existence of these spoofed websites or emails of trusted brands.
As the holiday shopping season approaches, 92 percent of all consumers shop online and about half are planning to shop online on Cyber Monday, exposing an opportunity for malicious hackers to strike. DomainTools has illustrated its key findings in an InfoGraphic:
https://blog.domaintools.com/2017/11/cyber-monday-deal-or-phishing-scam/
"Cyber Monday has grown in popularity year over year, and unfortunately, so has phishing and online counterfeiting. A range of techniques are used to trick shoppers into visiting a fake website or clicking on a malicious link.
This can result in a shopper unintentionally sharing financial and personal information with these criminals or even downloading ransomware," said Tim Chen, CEO of DomainTools. "As shoppers search for Cyber Monday deals, it's important that they remember to look closely at links and email addresses before clicking. If something seems too good to be true, it may instead be very fake and very bad."
I suggest you send this reminder to your users. You're welcome to copy/paste/edit
"Cyber Monday Is Scammer Heaven"
"It's Holiday Season for the bad guys too! But not the way you might think. They go into scam-overdrive mode. Black Friday and Cyber Monday are the busiest on-line shopping days and they are out to get rich with your money. So what to look out for?
At the moment, there are too-good-to-be-true coupons that offer complimentary phones or tablets all over sites on the Internet. Don't fall for it. Make sure the offers are from a legitimate company. While we're at it...
Watch out for alerts via email or text that you just received a package from FedEx, UPS or the US Mail, and then asks you for some personal information. Don't enter anything. Think Before You Click!
So, especially now, the price of freedom is constant alertness and willingness to fight back. Remember to only use credit cards online, never debit cards. Be super-wary of bulk email with crazy good BUY NOW offers and anything that looks slightly "off". If you think you might have been scammed, stay calm and call your credit card company, nix that card and get a new one.
Happy Holidays!"
[VIDEO] New Smart Groups Put Your Phishing, Training and Reporting on Autopilot
Automate the path your employees take to smarter security decisions. With KnowBe4's powerful new Smart Groups feature, you can use each employees’ behavior and user attributes to tailor phishing campaigns, training assignments, remedial learning and reporting.
Create sophisticated, targeted workflows without the headache, and make sure every employee is a strong building block of your human firewall. You can see the intersection of the criteria you specify - whether you’re building simple phishing clickers remedial training workflow or complex, multi-criteria location, behavior and timing-based workflow.
Best of all, Smart Groups is a powerful ad-hoc, real-time query tool that you use to get detailed reporting for management, so you’ll always know how your security awareness program is working.
The Incremental Phishing with Smart Groups video has been published in the Help Center. Here is the link to the 4-minute video:
https://support.knowbe4.com/hc/en-us/articles/115014939508
Automate the path your employees take to smarter security decisions. With KnowBe4's powerful new Smart Groups feature, you can use each employees’ behavior and user attributes to tailor phishing campaigns, training assignments, remedial learning and reporting.
Create sophisticated, targeted workflows without the headache, and make sure every employee is a strong building block of your human firewall. You can see the intersection of the criteria you specify - whether you’re building simple phishing clickers remedial training workflow or complex, multi-criteria location, behavior and timing-based workflow.
Best of all, Smart Groups is a powerful ad-hoc, real-time query tool that you use to get detailed reporting for management, so you’ll always know how your security awareness program is working.
The Incremental Phishing with Smart Groups video has been published in the Help Center. Here is the link to the 4-minute video:
https://support.knowbe4.com/hc/en-us/articles/115014939508
Don't Click That! How to Spot an Invoice Impersonation Attack That Pretends to Be From a Coworker
Finance workers are seeing a wave of phishing attacks that send victims a link to a fake invoice that appears to come from a trusted party, according to a new threat spotlight report from security firm Barracuda Networks.
These emails don't usually appear to be out of the ordinary, and guide the recipient to click on a link to an invoice. The sender's name is carefully chosen by the attackers to be someone the recipient knows and trusts.
If a victim clicks on the link, it typically begins downloading a doc. file for the supposed invoice. This is usually a malware download that could trigger ransomware, or steal the recipients' credentials from the browser. More at TechRepublic:
https://www.techrepublic.com/article/dont-click-that-how-to-spot-an-invoice-impersonation-attack-that-pretends-to-be-from-a-coworker/
Finance workers are seeing a wave of phishing attacks that send victims a link to a fake invoice that appears to come from a trusted party, according to a new threat spotlight report from security firm Barracuda Networks.
These emails don't usually appear to be out of the ordinary, and guide the recipient to click on a link to an invoice. The sender's name is carefully chosen by the attackers to be someone the recipient knows and trusts.
If a victim clicks on the link, it typically begins downloading a doc. file for the supposed invoice. This is usually a malware download that could trigger ransomware, or steal the recipients' credentials from the browser. More at TechRepublic:
https://www.techrepublic.com/article/dont-click-that-how-to-spot-an-invoice-impersonation-attack-that-pretends-to-be-from-a-coworker/
How I Infiltrated a Fortune 500 Company With Social Engineering
Good article at DarkReading. "Getting into the company proved surprisingly easy during a contest. Find out how to make your company better prepared for real-world attacks.
I infiltrated a Fortune 500 company with social engineering techniques (with authorization). Want to know how?
Here's the background: This fall during a security exercise at DerbyCon VII, I won the Social Engineering Capture the Flag (SECTF) contest, in which we all utilized social engineering techniques to collect information that could be used to compromise a company. It was a challenging competition against five top-notch competitors, and I am pleased to say I emerged victorious.
Before the convention, we were each assigned a Fortune 500 company in the Louisville, Kentucky, area and given three weeks to compile a report about them using open source intelligence, or OSINT, which is a means of collecting information from public sources such as search engines, company websites, and social media.
At DerbyCon, we made live phone calls from a soundproof box in front of an audience to collect more information. The informational "flags" captured in the report and phone calls were then scored.
How I Did It
For the sake of the security of my target company, I will not mention it by name, because I will discuss tactics, techniques, and descriptions of the findings. Interesting reading!:
https://www.darkreading.com/endpoint/how-i-infiltrated-a-fortune-500-company-with-social-engineering/a/d-id/1330335
Good article at DarkReading. "Getting into the company proved surprisingly easy during a contest. Find out how to make your company better prepared for real-world attacks.
I infiltrated a Fortune 500 company with social engineering techniques (with authorization). Want to know how?
Here's the background: This fall during a security exercise at DerbyCon VII, I won the Social Engineering Capture the Flag (SECTF) contest, in which we all utilized social engineering techniques to collect information that could be used to compromise a company. It was a challenging competition against five top-notch competitors, and I am pleased to say I emerged victorious.
Before the convention, we were each assigned a Fortune 500 company in the Louisville, Kentucky, area and given three weeks to compile a report about them using open source intelligence, or OSINT, which is a means of collecting information from public sources such as search engines, company websites, and social media.
At DerbyCon, we made live phone calls from a soundproof box in front of an audience to collect more information. The informational "flags" captured in the report and phone calls were then scored.
How I Did It
For the sake of the security of my target company, I will not mention it by name, because I will discuss tactics, techniques, and descriptions of the findings. Interesting reading!:
https://www.darkreading.com/endpoint/how-i-infiltrated-a-fortune-500-company-with-social-engineering/a/d-id/1330335
[FUN] Somebody Wrote an Email Bot to Waste Scammers' Time.
An entertaining and possibly useful tool which appears to be legit. Worth a minute of chuckles even if we don't use it. Have a look at the YouTube.
Introducing Re:scam - an artificially intelligent email bot made to reply to scam emails. Re:scam wastes scammers time with a never-ending series of questions and anecdotes so that scammers have less time to pursue real people:
https://youtu.be/jPajqAJWiNA
An entertaining and possibly useful tool which appears to be legit. Worth a minute of chuckles even if we don't use it. Have a look at the YouTube.
Introducing Re:scam - an artificially intelligent email bot made to reply to scam emails. Re:scam wastes scammers time with a never-ending series of questions and anecdotes so that scammers have less time to pursue real people:
https://youtu.be/jPajqAJWiNA
October 2017: The Month in Ransomware
Ransomware activity didn’t skyrocket last month, but there was definitely a substantial increase compared to September.
Perhaps the most serious wake-up call was the onset of BadRabbit, a Petya-like culprit going on a rampage in Eastern Europe. A likely successor of the Cerber ransomware dubbed Magniber started making the rounds via the Magnitude exploit kit. A Halloween-themed Trick-or-Treat blackmail malware demonstrated that cybercriminals follow the traditions too – in their own way, though.
Overall, 28 new strains emerged, 18 existing ones underwent updates, and only one complimentary decryptor was released. More at Tripwire:
https://www.tripwire.com/state-of-security/featured/october-2017-the-month-in-ransomware/
Also, Cryptojacking Craze: Malwarebytes Says It Blocks 8 Million Requests per Day
The in-browser cryptojacking craze that has taken over the Internet is getting worse by the day and more and more sites are implementing such systems, intentionally or after getting hacked.
Malwarebytes, one of the first major antivirus companies that have added support for blocking such scripts has recently released a report detailing statistics from the last month.
https://go.malwarebytes.com/rs/805-USG-300/images/Drive-by_Mining_FINAL.pdf
Ransomware activity didn’t skyrocket last month, but there was definitely a substantial increase compared to September.
Perhaps the most serious wake-up call was the onset of BadRabbit, a Petya-like culprit going on a rampage in Eastern Europe. A likely successor of the Cerber ransomware dubbed Magniber started making the rounds via the Magnitude exploit kit. A Halloween-themed Trick-or-Treat blackmail malware demonstrated that cybercriminals follow the traditions too – in their own way, though.
Overall, 28 new strains emerged, 18 existing ones underwent updates, and only one complimentary decryptor was released. More at Tripwire:
https://www.tripwire.com/state-of-security/featured/october-2017-the-month-in-ransomware/
Also, Cryptojacking Craze: Malwarebytes Says It Blocks 8 Million Requests per Day
The in-browser cryptojacking craze that has taken over the Internet is getting worse by the day and more and more sites are implementing such systems, intentionally or after getting hacked.
Malwarebytes, one of the first major antivirus companies that have added support for blocking such scripts has recently released a report detailing statistics from the last month.
https://go.malwarebytes.com/rs/805-USG-300/images/Drive-by_Mining_FINAL.pdf
NATO to Increase Cyber Weaponry to Combat Russia
NATO members agreed Wednesday to increase the use of cyber weaponry and tactics during military operations, with the alliance also upgrading other capabilities to combat a resurgent Russia.
The changes are part of the alliance's biggest shakeup since the Cold War, with defense ministers backing the creation of two new command centers to help protect Europe.
The revamp reflects the "changed security environment" of recent years, NATO chief Jens Stoltenberg said at a meeting of defence ministers in Brussels.
The threat to the alliance's eastern flank has grown as a concern after Russia's annexation of Crimea in 2014.
"We are now integrating cyber effects into NATO missions and operations to respond to a changed and new security environment where cyber is part of the threat picture we have to respond to," Stoltenberg said.
"In any military conflict cyber will be an integral part and therefore we need to strengthen our cyber defences and our cyber capabilities," he added. More at:
http://www.securityweek.com/nato-increase-cyber-weaponry-combat-russia
Also: EU to Declare Cyber-Attacks “Act of War”. USA Likely to follow:
https://blog.knowbe4.com/eu-to-declare-cyber-attacks-act-of-war.-usa-likely-to-follow
NATO members agreed Wednesday to increase the use of cyber weaponry and tactics during military operations, with the alliance also upgrading other capabilities to combat a resurgent Russia.
The changes are part of the alliance's biggest shakeup since the Cold War, with defense ministers backing the creation of two new command centers to help protect Europe.
The revamp reflects the "changed security environment" of recent years, NATO chief Jens Stoltenberg said at a meeting of defence ministers in Brussels.
The threat to the alliance's eastern flank has grown as a concern after Russia's annexation of Crimea in 2014.
"We are now integrating cyber effects into NATO missions and operations to respond to a changed and new security environment where cyber is part of the threat picture we have to respond to," Stoltenberg said.
"In any military conflict cyber will be an integral part and therefore we need to strengthen our cyber defences and our cyber capabilities," he added. More at:
http://www.securityweek.com/nato-increase-cyber-weaponry-combat-russia
Also: EU to Declare Cyber-Attacks “Act of War”. USA Likely to follow:
https://blog.knowbe4.com/eu-to-declare-cyber-attacks-act-of-war.-usa-likely-to-follow
Interesting News Items This Week
Cognitive Mindhacks: How Attackers Spread Disinformation Campaigns:
https://www.darkreading.com/cloud/cognitive-mindhacks-how-attackers-spread-disinformation-campaigns/d/d-id/1330334
That massive data breach has cost Equifax nearly 90 million and a 25% reduction in share value:
http://business.inquirer.net/240604/massive-data-breach-cost-equifax-nearly-90-million
Wikileaks Releases Source Code of CIA Cyber-Weapon:
https://www.bleepingcomputer.com/news/government/wikileaks-releases-source-code-of-cia-cyber-weapon/
The nasty future of ransomware: Four ways the nightmare is about to get even worse:
http://www.zdnet.com/article/the-nasty-future-of-ransomware-four-ways-the-nightmare-is-about-to-get-even-worse/
Data Breach Record Exposure Up 305% from 2016:
https://www.darkreading.com/vulnerabilities---threats/data-breach-record-exposure-up-305--from-2016/d/d-id/1330359
10 Mistakes End Users Make That Drive Security Managers Crazy:
https://www.darkreading.com/endpoint/10-mistakes-end-users-make-that-drive-security-managers-crazy------/d/d-id/1330305
12 Artificial Intelligence Terms You Need to Know:
https://www.informationweek.com/big-data/ai-machine-learning/12-artificial-intelligence-terms-you-need-to-know/d/d-id/1330003
Social Engineer Spills Tricks of the Trade:
https://www.darkreading.com/endpoint/social-engineer-spills-tricks-of-the-trade-/d/d-id/1330315
Microsoft solution to mitigate the DDE exploit "turn it off". So if you use Dynamic Documents updating and you have to manually turn it off, here is how:
https://technet.microsoft.com/en-us/library/security/4053440
Cognitive Mindhacks: How Attackers Spread Disinformation Campaigns:
https://www.darkreading.com/cloud/cognitive-mindhacks-how-attackers-spread-disinformation-campaigns/d/d-id/1330334
That massive data breach has cost Equifax nearly 90 million and a 25% reduction in share value:
http://business.inquirer.net/240604/massive-data-breach-cost-equifax-nearly-90-million
Wikileaks Releases Source Code of CIA Cyber-Weapon:
https://www.bleepingcomputer.com/news/government/wikileaks-releases-source-code-of-cia-cyber-weapon/
The nasty future of ransomware: Four ways the nightmare is about to get even worse:
http://www.zdnet.com/article/the-nasty-future-of-ransomware-four-ways-the-nightmare-is-about-to-get-even-worse/
Data Breach Record Exposure Up 305% from 2016:
https://www.darkreading.com/vulnerabilities---threats/data-breach-record-exposure-up-305--from-2016/d/d-id/1330359
10 Mistakes End Users Make That Drive Security Managers Crazy:
https://www.darkreading.com/endpoint/10-mistakes-end-users-make-that-drive-security-managers-crazy------/d/d-id/1330305
12 Artificial Intelligence Terms You Need to Know:
https://www.informationweek.com/big-data/ai-machine-learning/12-artificial-intelligence-terms-you-need-to-know/d/d-id/1330003
Social Engineer Spills Tricks of the Trade:
https://www.darkreading.com/endpoint/social-engineer-spills-tricks-of-the-trade-/d/d-id/1330315
Microsoft solution to mitigate the DDE exploit "turn it off". So if you use Dynamic Documents updating and you have to manually turn it off, here is how:
https://technet.microsoft.com/en-us/library/security/4053440
Cyberheist 'Fave' Links
This Week's Links We Like, Tips, Hints and Fun Stuff
- 217 skydivers jump simultaneously from 10 planes to break a world record with three stunning formations, falling towards the ground at 120 mph:
http://www.flixxy.com/217-skydivers-break-world-record.htm?utm_source=4
- Amazing parkour, martial arts, surfing, soccer, gymnastics, diving, BMX, rock climbing, jump rope, basketball and gymnastics:
http://www.flixxy.com/people-are-awesome-best-of-the-week-39.htm?utm_source=4
- SquareTrade iPhone X Breakability video. This is pretty bad, you NEED a case:
https://www.youtube.com/watch?v=T_OT1FQSWuU&feature=youtu.be
- Lamborghini and MIT's Terzo Millennio is a self-healing future supercar:
https://www.cnet.com/roadshow/news/lamborghini-mit-terzo-millennio-self-healing-supercar/#ftag=CAD590a51e
- Star Wars Rogue One — A Phish Story. This one is cute, check it out:
https://vimeo.com/195371513 - A Compilation of Robots Falling Down at the DARPA Robotics Challenge. Riot!:
https://m.youtube.com/watch?v=g0TaYhjpOfo





