 Dubbed the “Cloud Hopper” campaign, victim companies such as Ericsson, HPE, IBM, and more were targets of exfiltration aimed and helping advance the Chinese economy.
Dubbed the “Cloud Hopper” campaign, victim companies such as Ericsson, HPE, IBM, and more were targets of exfiltration aimed and helping advance the Chinese economy.- Spear phishing is used to trick users into giving up their cloud credentials
- Lateral movement within the HPE network was done to find servers that could bridge them into client networks
- More lateral movement on the client network was done to identify valuable data
- Data was encrypted and exfiltrated either back through the HPE network or directly through the victim company’s network
We’ve discussed the rise in the use of island hopping in supply chain scenarios; this is very similar in nature, with the only difference being the target network is on the same cloud infrastructure.
At the end of the day, it all starts with a simple phishing email; a single “click here” and the impact extends to multiple companies costing truly untold millions, as the extent of the data theft and the resulting damage is still unknown.
Putting users through continual Security Awareness Training is an absolute must in cases like this. It was a user that was fooled. Users need to be taught what to look for and how to avoid becoming the victim of what have become very convincing scams. Even if you’re not an IBM or an HPE, it doesn’t mean you’re not a target for island hopping attacks that take you and the businesses around you for all they can.
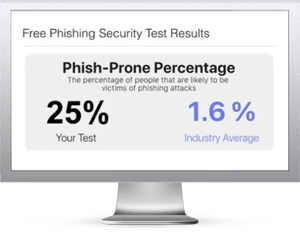
Free Phishing Security Test
Find out what percentage of your employees are Phish-prone™
Would your users fall for convincing phishing attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
 Here's how it works:
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





