
The WSJ revealed a brazen hack by Chinese state-sponsored bad actors who totally owned more than 10 global telecom networks, and had full admin access to their networks. They were able to swipe users’ whereabouts, text-messaging records and call logs.
They reported: "The multiyear campaign, which is continuing, targeted 20 military officials, dissidents, spies and law enforcement—all believed to be tied to China—and spanned Asia, Europe, Africa and the Middle East, says Cybereason Inc., a Boston-based cybersecurity firm that first identified the attacks. The tracked activity in the report occurred in 2018." Here is a graphic how these hacks went down. The source is Cybereason, which is run by former Israeli counterintelligence members:
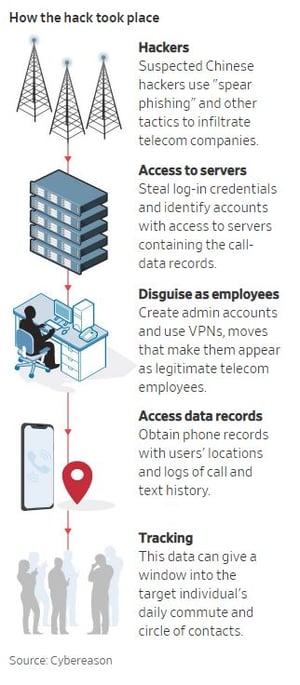
Amit Serper, Cybereason’s head of security research said that the campaign used APT 10-linked procedures and techniques, including a web shell used to steal credentials and a remote-access tool, and the hackers breached telecom companies’ networks through traditional spear phishing emails and other tactics.
The APT 10 group, also known as cloudhopper, is believed by cybersecurity experts to be backed by China’s government based on its history of going after data that is strategic and not immediately monetizable. The group has been less visibly active this year following the Justice Department indictments, though is likely still around, said Ben Read, senior manager of cyber espionage analysis at FireEye Intelligence.
Once inside, the hackers stole login credentials, identifying computers or accounts with access to the servers containing the call-data records. They cloaked themselves even more by creating admin accounts and covering their digital tracks with virtual private networks, or VPNs, which made the behavior appear as if it had come from legitimate employees.
The full article is great reading, strongly recommended for your C-suite, and again is excellent ammo for Infosec budget so that you can step your users through new-school security awareness training.
Would your users respond to spear phishing emails?
KnowBe4's new Phishing Reply Test (PRT) is a complimentary IT security tool that makes it easy for you to check to see if key users in your organization will reply to a highly targeted phishing attack without clicking on a link. PRT will give you quick insights into how many users will take the bait so you can take action to train your users and better protect your organization from these fraudulent attacks!
 Here's how the Phishing Reply Test works:
Here's how the Phishing Reply Test works:
- Immediately start your test with your choice of three phishing email reply scenarios
- Spoof a Sender’s name and email address your users know and trust
- Phishes for user replies and returns the results to you within minutes
- Get a PDF emailed to you within 24 hours with the percentage of users that replied
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://www.knowbe4.com/phishing-reply-test





