 Be aware of being involved in malicious CAPTCHA solving.
Be aware of being involved in malicious CAPTCHA solving.
I do not know anyone who loves CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart). These are little online tests that supposedly tease out whether the action being performed is being done by a human or some automated bot program or script. They are needed because miscreants across the Internet would otherwise abuse the involved services to create bogus accounts used to hack others or simply abuse the system in some other way. CAPTCHAs are an unfortunate, but necessary part of life (at least right now). We are forced to interact with them when we are newly registering on websites or performing a potentially risky action.
CAPTCHA Examples
There are many different types of CAPTCHAs, ranging from extremely easy to solve to ones that require more effort and are more prone to human error. In their easiest form, they are simply a box (see example below) that we are told click.
And all we do is click the box to prove we are not a bot, resulting in the image we all see below.
Some of the CAPTCHA tests ask us to type out characters we see that have been exaggerated and changed in some way that humans can supposedly still make them out, but an automated optical character recognition (OCR) program could not. See example below.
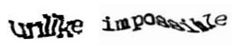
I am sure many of us really hate those sorts of tests because it can be tough for anyone to figure out what the characters or words are at times. I have even hit the ‘Send a new word’ button before and had to cycle through a few new offers before I could find one that I could figure out 100%.
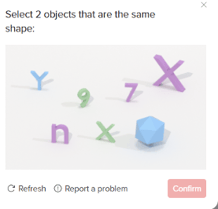
Some CAPTCHAs (like the one below), used by Tik Tok, simply ask you to pick out two similar objects.
The most complicated ones are the ones that ask you to “Click on all the squares…” that contain traffic lights, cars, traffic signs, or some other supposedly common image (like the image below).

The problem with these types is that many times, the blocks will contain a very tiny piece of the required object, often looking almost accidental or microscopic, and you’re not sure if it should be selected or not. Forget frustrating bots, CAPTCHAs frustrate humans.
If you want to a seriously funny video that pokes fun at the trials and tribulations of CAPTCHAs, watch this video here.
CAPTCHA Tricks
The reason why CAPTCHAs are not going away is because they work. They do significantly defeat automated bots and scripts. There have been many attempts by hackers to automate answering CAPTCHAs in bulk, including using machine learning, OCR, and artificial intelligence-like tools. None of them work as good as a human.
So, hackers simply outsourced CAPTCHA solving to human beings. Hackers still use bots and automation to register on websites and create accounts, but the whole process is automated. They do not use the involved website’s normal code as offered up to a normal user surfing the web. Instead, they create malicious programs that interface with the website or its application programming interface (API), which removes all the human-readable text and simply, quickly fills in the required account registration information. And when the CAPTCHA component is shown, the bot sends just the CAPTCHA part to real humans paid by the hackers to solve one CAPTCHA puzzle after the next. Somewhere in the world are teams of sweat shop workers who are working tirelessly to solve CAPTCHAs, one after the other, as fast as they can. The sweat shop workers make only a tiny amount per solved CAPTCHA, but if they can solve hundreds to thousands of them in a day, they can make a few dollars or a decent living for their skill set in their part of the world. I know of skilled IT workers who bought their less skilled parents a computer, set it up in their house, and their mom and dad solve CAPTCHAs to supplement their normal income. It’s not ethical, but in many parts of the world, it’s the way a part of the population makes their money.
Websites using CAPTCHAs understand that hackers will hire teams of sweat shop workers to solve CAPTCHAs, so they fight back in many ways, including tracking the originating IP addresses involved with solving the CAPTCHA. If too many CAPTCHAs are solved from one IP address, they cut that IP address off or no longer allow it to solve future CAPTCHAs. Hackers responded by changing up used IP addresses, so they do not get “burned”, but it significantly slowed down illegal CAPTCHA solving.
Frustrated hackers responded by sending CAPTCHAs to be solved to millions of innocent people across the Internet, each with their own individual IP addresses. The criminals compromise innocent websites around the Internet and instead of inserting a malicious JavaScript that tries to install malware or phish login credentials, it sends a CAPTCHA image, which it hopes the hapless user will fill out and respond to.
It was just such an attempt that I saw today that inspired this blog. I went to a popular news website that I visit every day, several times a day, and all of a sudden on that website, I saw a CAPTCHA pop-up that it told me I had to solve (just one of the simple click-here types). I shook my head, and thought, “What’s This?” and was just about to click it when I realized that it was probably a malicious CAPTCHA redirect. I examined the proposed CAPTCHA. It looked as normal as any CAPTCHA I had ever seen before. I would have taken a picture for this column, but it looked like any other CAPTCHA I had ever seen before…no clues of its maliciousness. It was just a CAPTCHA on a website that does not require registration and never before had asked me to fill out a CAPTCHA.
I hit the refresh button and the malicious JavaScript CAPTCHA disappeared and the regular website came up. I downloaded all the website code to see if I could figure out where the malicious JavaScript was, but my browser refresh had bought up a new instance of the website without the malicious CAPTCHA. My “evidence” was gone. More importantly, the website I was on was not asking for me to complete a CAPTCHA, proof that the one shown to me was a malicious redirect. I notified the website’s developers about the issue, but haven’t even received an automated reply.
I am not sure where the malicious CAPTCHA redirect came from. The average popular website has 50 to 150 different elements that make up the website page we see and most of those elements are from third-party sites and services, and not from the domain name you went to. Maybe the malicious JavaScript came through on a banner ad. Maybe it came through on a borrowed JavaScript element. Somewhere on that web page was a compromised element that ended up, at least for that one instance, displaying a malicious CAPTCHA redirect.
Why You Should Care About Malicious CAPTCHAs
Now in the grand scheme of things, malicious CAPTCHA redirects are very low risk to the end user. As far as I know, they cannot be used to silently install malware on a user’s device or to redirect them to a malicious web page. In that way, they are a bit like adware malware – more of a pest than outright dangerous.
But like adware, malicious CAPTCHAs, can be a stand-in for how something far more malicious is presented to us or our end users, that if they don’t realize it and click, can lead to something far more malicious. The effort needed for adware and CAPTCHA redirects to get presented to an end user is the same root exploits as the much more dangerous things that could otherwise be presented. Presence of adware on a computer means a much more malicious backdoor trojan or ransomware program could use the same hole or trick. If a user ONLY has adware, they are just lucky. It could have been far worse. And if they do not figure out that adware got on the computer, worse things could easily happen next time. Luck runs out.
The same is true with malicious CAPTCHA redirects. At the very least, none of us want to be involved in solving CAPTCHA puzzles for hackers so they can automate malicious account creation and do worldwide malicious things. But it also a teachable moment for end users. All users should be aware that potentially dangerous elements could be presented to them that they need to evaluate and handle properly, even if they go to what they think is a “safe” web page.
Educate your end users to be aware of possible dangerous website elements that get inserted into their favorite, legitimate websites; and how to recognize and respond. New-school security awareness training is all about making people aware of what can be done, what it looks like, and how to treat issues. Let your end users know about potential malicious CAPTCHA redirects, because if they can recognize and avoid those, they are going to be ahead of the game with the more malicious web elements.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




