A new report from Carbon Black’s Threat Analysis Unit (TAU) used their data and modeling techniques to come up with an estimate of ransomware sales transactions activity on the Dark Web.
Criminal ransomware startups—“Ransompreneurs” if you will—can make over $100,000 per year through sales of their source code along with offering advanced code tutoring, or they can just sell a kit which enables a newbie to quickly get into the business.
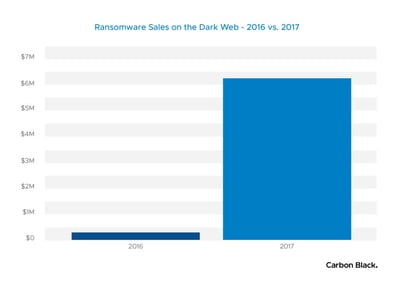
Based on their model they estimate, “In a comparison of 2016 to 2017, Carbon Black found that the Ransomware Marketplace has grown from $249,287.05 to $6,237,248.90, revealing a growth rate of 2,502%.”
These are growth rates worthy of an Inc. 500 company.
What do you get when you combine availability of do-it-yourself ransomware-as-a-service kits (RaaS), novice cybercrooks, cryptocurrency and anonymity tools? A market opportunity for newbies to cash in on the gravy train and make a quick, illegal bundle of Bitcoin by attacking businesses and/or end users.
It’s now easier than ever for Ransompreneurs to do their own thing. Some are even using the software affiliate model of distribution complete with affiliate transaction cuts down the chain.
Providing aspiring cybercrims with easy to deploy DIY ransomware solutions to collect ransom via Bitcoin spawned a rapidly growing but still relatively small illegal software cottage industry. Given the availability of tools and the tutoring effect of shared knowledge, the platform for RaaS enabled attackers has driven up the number of total Ransomware attacks.
According to Carbon Black's report: “The most notable innovations contributing to the proliferation and success of the dark web ransomware economy have been the emergence of Bitcoin for a ransom payment, and the anonymity network Tor, to mask illicit activities. Bitcoin allows money to be transferred in a way that makes it nearly impossible for law enforcement to “follow the money.” Bank transfers and credit card transactions traditionally aid in the quick takedown of scams. Bitcoin means there’s no bank to identify the account holder.”
The TAU report noted: “Unlike many other forms of cyberattacks, ransomware can be quickly and brainlessly deployed with a high probability of profit.”
2016 FBI statistics attributed losses to Ransomware were estimated at 1 billion dollars. Some security firms are estimating losses for 2017 may reach 5 billion dollars or higher.*
The low-end RaaS Kits are affordable. Carbon Black said that the (DIY) kits range from just 50 cents to 3 grand with the median price pegged at $10.50. A hard working DIY-er can earn over 100K per year, much more than many legit, gainfully employed software developers are making.
Finally, the report observes that “As a result of the maturity with these innovations, the underground ransomware economy is now an industry that resembles commercial software — complete with development, support, distribution, quality assurance and even help desks. We should also consider consumers’ willingness to pay ransoms. In a recent Carbon Black survey, we asked participants if they would personally be willing to pay ransom money if their personal computer and files were encrypted by ransomware, 52% said “yes.”
Six Key Findings from Carbon Black
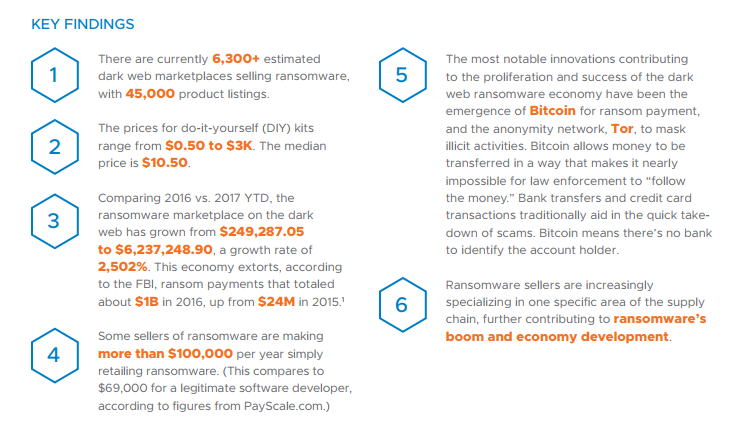
- There are currently 6,300+ estimated dark web marketplaces selling ransomware, with 45,000 product listings.
- The prices for do-it-yourself kits range from $0.50 to $3K. The median price is $10.50.
- Comparing 2016 vs. 2017 YTD, the ransomware marketplace on the dark web has grown from $249,287.05 to $6,237,248.90, a growth rate of 2,502%.
- Some sellers are making more than $100,000 per year simply retailing ransomware. This compares to $69,000 for a legitimate software developer, according to figures from PayScale.com.
- Bitcoin allows money to be transferred in a way that makes it nearly impossible for law enforcement to “follow the money.” Bank transfers and credit card transactions traditionally aid in the quick takedown of scams. Bitcoin means there’s no bank to identify the account holder.
- Ransomware sellers are increasingly specializing in one specific area of the supply chain, further contributing to ransomware’s boom and economy development.
Carbon Black Full PDF Report download here:
Find out How Vulnerable Your Network Is Against 3 NEW Ransomware Scenarios
- CitroniVariant - A specific scenario designed to simulate the distinct file encryption activity of Critroni/CBT ransomware.
- Collaborator - An advanced scenario that spawns multiple processes to carry out encryption routines.
- VirlockVariant - One of the more complex scenarios, designed to simulate a variant Virlock that uses watchdog processes to keep encryption processes restarted.
- 100% harmless simulation of a real ransomware infection
- Does not use any of your own files
- Tests 13 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!





