 Research from Valimail shows that at least 3.4 billion phony emails are sent every day, Help Net Security reports. Despite this staggering number, most organizations still aren’t enforcing email authentication protocols like DMARC.
Research from Valimail shows that at least 3.4 billion phony emails are sent every day, Help Net Security reports. Despite this staggering number, most organizations still aren’t enforcing email authentication protocols like DMARC.
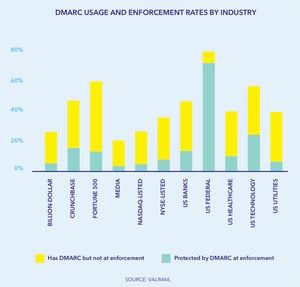
The research found that nearly 80% of all email inboxes have DMARC enabled, but only 20% of these are configured to take action against spoofed emails. The US Federal government and tech companies account for a large portion of the organizations with DMARC enforcement policies. In most industries, the enforcement rate is lower than 10%.
The reason for this gap is primarily due to the fact that DMARC can be difficult to configure properly, particularly for large organizations. DMARC is initially set up in monitoring mode, so domains receive reports about spoofed emails, but they allow the messages to continue unperturbed. This mode is meant to help administrators, but it doesn’t do anything to prevent fraudulent emails from ending up in people’s inboxes.
In order for DMARC to actually have an effect, organizations need to enact enforcement policies that determine what to do with spoofed emails. The domain can then inform mail servers to discard these emails or place them in the recipient’s spam folder. Most organizations run into difficulties at this stage, and end up leaving the protocol in monitoring mode indefinitely.
DMARC is a highly recommended layer of defense for every organization, and it’s well worth the effort to get it working properly. However, it’s not bulletproof against determined attackers. New-school security awareness training can help your employees work with DMARC, while teaching them how to spot the phishing emails that slip through the cracks. Help Net Security has the story:
https://www.helpnetsecurity.com/2019/06/12/fake-emails/
Do you know what's getting through your mail filters?
KnowBe4’s Mailserver Security Assessment (MSA) helps you assess your organization’s mailserver configuration settings and check the effectiveness of your email filtering rules. With email still the #1 attack vector used by the bad guys, you want to see what types of messages may make it through your filters from the outside.
MSA gives you a quick insight at how your mailserver handles test messages that contain a variety of different message types including email with attachments that contain password-protected, macro zipped, and .exe files or have spoofed domains.
 Here’s how MSA works:
Here’s how MSA works:
- 100% non-malicious packages sent
- Select from 30+ automated email message types to test against
- Saves you time! No more manual testing of individual email messages using MSA's automated send, test, and result status
- Validate that your current filtering rules work as expected
- Results in an hour or less!
Find out now if your mail server is configured correctly, many are not!

Don't like to click on redirected buttons? Copy & Paste this link in your browser.
https://www.knowbe4.com/mailserver-security-assessment
 Research from Valimail shows that at least 3.4 billion phony emails are sent every day, Help Net Security reports. Despite this staggering number, most organizations still aren’t enforcing email authentication protocols like DMARC.
Research from Valimail shows that at least 3.4 billion phony emails are sent every day, Help Net Security reports. Despite this staggering number, most organizations still aren’t enforcing email authentication protocols like DMARC.  Here’s how MSA works:
Here’s how MSA works:




