TL,DR:
A recent phishing attack posing as a PDF decoy from a Denver law firm was stealing clients' Office 365 credentials. The phishing bait was hosted in Azure blob storage and contained a Microsoft-issued domain and SSL certificate, making it particularly believable.
Detail:
A recent PDF decoy linked to an Office 365 phishing page was impersonating a law firm in Denver, CO, according to a Netskope Threat Protection press release on Wednesday. The phishing page was hosted in Azure blob storage, and the PDF decoy was hosted in Google Drive.
Since the phishing bait was hosted in Azure blob storage, it had a Microsoft-issued SSL certificate and domain, making the attack vector especially convincing and difficult to detect, said the release. And since the PDF decoys appear to be credible, users felt comfortable entering their Office 365 credentials to download the document, added the release.
Azure Blob storage is a Microsoft storage solution that can be used to store unstructured data such as images, video, or text. One of the advantages of Azure Blob storage is that it accessible using both HTTP and HTTPS, and when connecting via HTTPS, will display a signed SSL certificate from Microsoft.
The attack targeted clients of a Denver-based law practice, who received an email from the firm with a PDF decoy titled "Scanned Document...Please Review.pdf.," said the release. Victims would attempt to download the PDF, then be prompted to enter credentials for Office 365. After inputting their personal information, they would be redirected to another phishing page claiming that the email or password entered was invalid, added the release.
After many redirects, the target is eventually taken back to a Microsoft page, with no document downloaded. With no document downloaded, victims may feel compelled to try and re-enter their credentials, or enter credentials to a different account, becoming further compromised, said the release.
The attack was believable enough to trick most people. But, it was particularly deceiving since it was designed to trick users who know to check that the domain and SSL certificate of a website matches its content, said the release. Users who are savvy enough will be able to recognize it is a malicious site because of the subdomain, which shows that it's Azure blob storage instead of an official Microsoft address, added the release.
This tactic is evidence that phishing attacks are becoming more clever and tricky. In order to stay protected, companies should teach their employees how to recognize Azure, AWS, and GCP object store URLs, so they are able to recognize when a site might be malicious, said the release. Source: TechRepublic

We've got something really cool for you: the new Phishing Security Test v3.0!
Sending simulated phishing emails is a fun and an effective cybersecurity best practice to patch your last line of defense… your users.
Find out the Phish-prone percentage™ of your organization with our free updated Phishing Security Test that now includes our New Industry Benchmarking. See where you stack up! Industry Benchmarking enables you to compare your organization’s Phish-prone percentage with others in your industry.
Find out how you are doing compared to your peers and see the difference 12 months can make after using the integrated KnowBe4 Simulated Phishing and Security Awareness Training platform!
With Our Updated Phishing Security Test: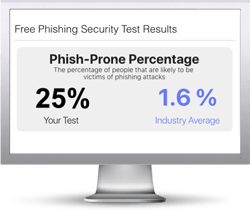
- You can customize the phishing test based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Start phishing your users now. Fill out the form, and get started immediately. There is no cost.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





