There is a new ransomware strain hitting organizations called CryptoWall. Late April, the cyber criminals who developed the CryptoDefense ransomware released a new variant called CryptoWall. This strain is for the most part the same as CryptoDefense except another brandname, and different filenames for the ransom instructions.
IT security pundits speculated that either the criminals released a new version because CryptoDefense was being blocked by endpoint protection products, or that they sold their source code to another cyber mafia. The bad news is that the earlier vulnerability of CryptoDefense has been fixed and you can no longer yourself decrypt files that are encrypted by CryptoWall.
This puppy comes with a twist though, it is no longer requires a user to open an infected attachment. Malicious advertisements on domains belonging to Disney, Facebook, The Guardian newspaper and others are leading people to sites that are CryptoDefense/Wall infected and encrypt their drives.
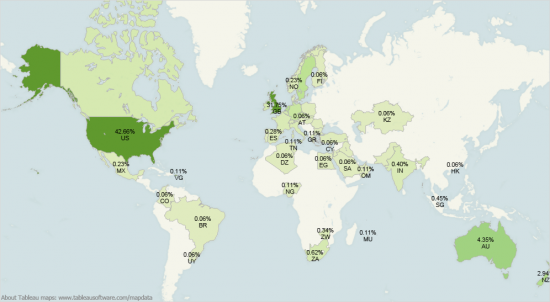
This is a massive attack reported by Cisco, on their blog and above are the countries primarily targeted. Since Cisco began blocking the attacks on April 24, its researchers said they had blocked requests to over 90 infected web domains for more than 17 percent of its cloud-security customer base. Mind you, Cisco's customer base for their cloud web security is really large, so 17% is big numbers.
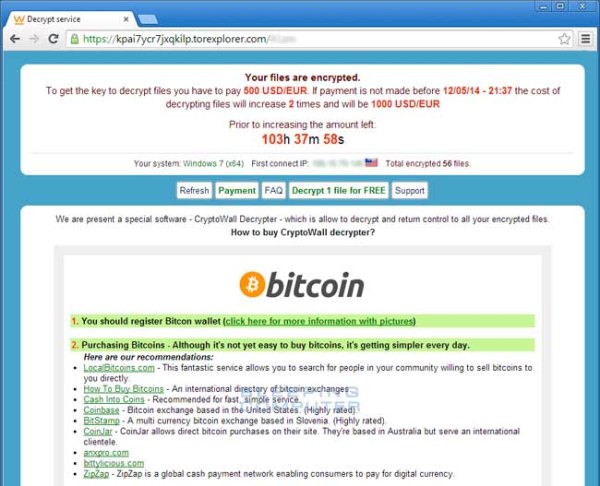
In the mean time, back at the ranch, ransomware grand-daddy CryptoLocker has improved the quality of its spear-phishing attacks with fake fax announcement messages that start to look very real. They also improved their marketing, This version provides a new feature which is a button that gives you the chance to "Decrypt 1 file for FREE" and is fully functional. Oh Joy.
It's a very good idea to step your end-users through effective Kevin Mitnick Security Awareness Training. You can get a free quote to find out how much this would be for your organization. You'll be pleasantly surprised how affordable this is.
Related Pages: Ransomware





