In IT, we are subject to help desk tickets and putting out fires. The problem with this is that most of these are short-term fixes. It is usually about last week's downtime, today's malware infection and next week's new app coming online.
In IT, we are subject to help desk tickets and putting out fires. The problem with this is that most of these are short-term fixes. It is usually about last week's downtime, today's malware infection and next week's new app coming online.
In their new Data Breach Investigation Report (DBIR), Verizon shows this short-term focus has a few drawbacks. If apart from your day-to-day coping with issues, you are also able to spend some time to organize your environment with a long-term perspective that can pay off handsomely.
Verizon took the long-term view in their 2014 DBIR with some surprising results. They wanted to produce "actionable" information you could really do something with, so they looked over a longer period to see if there were patterns. Lo and behold, there were.
There are just nine attack patterns, and only three stand out as the main culprits. The main surprise though is a comprehensive matrix of incident classifications and industries they have affected. There is an enormous difference in the kinds of attacks that different industry sectors are being subjected to. If you know how you are targeted, that makes it easier to defend yourself, so check out Figure 19 on page 15 of the PDF.
One thing to note when you look at all the statistics is that they seem somewhat skewed. This is caused by the requirement that all incidents in the public sector have to be reported as opposed to the private sector who often stonewall any data breach.
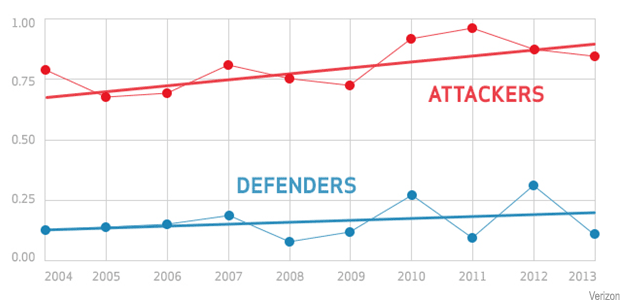
However, the main message of the new DBIR is unfortunately illustrated in a very simple graphic that compares, over 10 years, the time it has taken for an attacker to compromise an asset versus the time it takes for a defender to discover the breach. The graph shows the amount of time in days or less it took to compromise (the red line) to discovery (the
blue line). In other words, most assets were breached in a few days, where the time to discovery was much longer. The gap is widening. Yikes.