 Cyber security professionals are slowly but surely grabbing more and more military jargon. No surprises there, with a possible cyberwar brewing. The "kill chain" is a traditional warfare term most often used by the US Air Force as the command and control process for targeting and destroying enemy forces.
Cyber security professionals are slowly but surely grabbing more and more military jargon. No surprises there, with a possible cyberwar brewing. The "kill chain" is a traditional warfare term most often used by the US Air Force as the command and control process for targeting and destroying enemy forces.
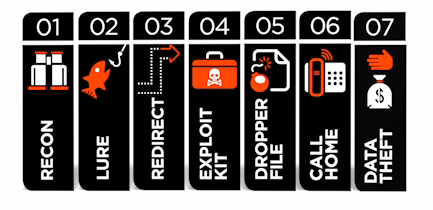
The last 12 months this "kill chain" concept has made it into cyber security marketing. Many vendors have come up with models, but Websense recently broke it out into a well-defined seven-stage model that cyber criminals utilize to get to their victims. You do not have to use all of these steps all the time, but often this is how attacks go down. Here is what it looks like:
- Initial reconnaissance
- Crafting a phishing lure to encourage the victim to click
- Redirecting victim to a compromised server
- Using an exploit kit to scan for vulnerabilities and zero-days
- Drop malware onto the victim's machine
- Call home to the command & control server
- Exfiltrate (or encrypt) data and take over the workstation
Cyber security vendors are using these steps to explain how their products will disrupt the criminal process. These steps are also useful for you as an IT pro, so you can assess your own network and see how you can best defend against cyber attacks.
Arthur Wong, HP senior vice-president and general manager of HP Enterprise Security Services (ESS) globally, told ZDNet at a media briefing last Wednesday: "The bad guys, the adversaries, they collaborate way more than governments, and way more than commercial industries do themselves. When anyone wants to even launch an attack out there on a particular company, they're going to go into chat rooms and ask, 'Hey does anybody own a computer or a system inside this company?', and someone will put up their hand, or they'll know someone else, and a deal is negotiated".
I have been talking a lot about the criminal ecosystem the last few years. It's becoming more specialized, aligned with the 7 steps in the kill chain. According to Bob Hansmann, Websense's director of product marketing, cyber criminals now provide tailored services for every step of the kill chain, and even have aggregators that pull together whole attack campaigns.
Stay careful out there.




