Why Security Awareness Training? Cryptolocker, That's Why...
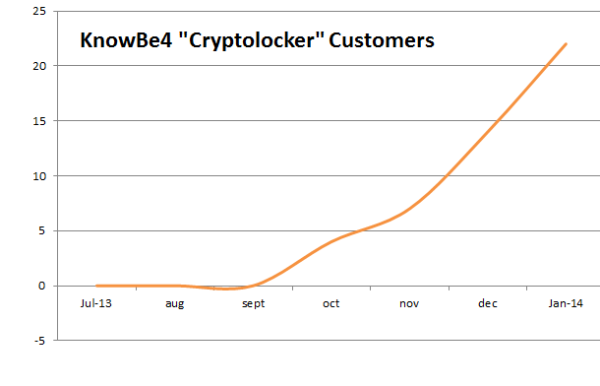
We here at KnowBe4 have been getting a lot of system admins calling us with the request for security awareness training because end users have been tricked into opening up attachments of phishing emails and infected their workstation with the cryptolocker malware. This started last September and it's not going away but actually getting worse. (See graph below)
This malicious hijacker code detects the personal files of a user and wraps them in strong encryption. This is both the local user Docs and remote shared folders. It encrypts every file with standard Office extensions, including images and PDFs!
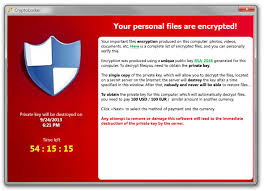
The bad guys ask $300 to "give your files back". Initially they asked for just $100 but realized they were too cheap and people would pay more so they bumped up the price.
In many cases, system admins and repair professionals come to the conclusion that the only (and fastest) way to get the files back is to pay the ransom. The problem is that you could get rid of the malware itself, but the files are still encrypted, and without the malware you cannot decrypt your files anymore.
Surprisingly enough, the bad guys do indeed live up to their criminal promise (if their payment servers are up) and decrypt the files if you pay. The decryption will start at a rate of about 5GB per hour. Note that the key that "unlocks" your files is unique; you will not be able to use anyone else's key.
Malware researchers from almost all antivirus companies are furiously working on a way to prevent this from occurring, and some are able to block it from running, but these bad guys are very sophisticated; decrypting the user's "cryptolocked" files requires access to both the public and private keys used to encrypt them. Moreover, they change their malicious code all the time, and your antivirus might not catch it tomorrow. Antivirus companies are not able to decrypt the files, only the Cryptolocker malware can do the decryption. At this point in time probably the only people that know how to solve this are the NSA and they are being silent.
And how does this malware get installed on a workstation? You guessed it, users being social engineered and opening an infected email attachment. The bad guys are pulling out all the stops and use a variety of social engineering tactics, most recently it's tracking information from either DHL, UPS, FedEx and USPS, but there are many phishing attacks including banks and government.
So what does it do after a user opens the infected attachment?
- They are presented with a cryptolocker splashscreen similar to the one above
- It will encrypt files on volumes (network, locally attached) where the user has modify permissions
- They are asked to pay ransom via GreenDot MoneyPaks, BitCoin, CashU, paysafecard, or Ukash of either $100 or $300 (depending on the older or newer version)
- Cryptolocker will set a timer to decrypt the files if the user decides to pay the ransom
- If the timer expires, the software uninstalls itself(!) and the data is lost
- Make sure you have a recent backup of the files that actually can be restored, wipe and rebuild the machine from scratch, and restore the files.
- We see an average of three hours of admin work for this.