|
CyberheistNews Vol 4, 04
Editor's Corner

Arg! The Cat O' Nine Tails For Careless Clickers!
Captain Stu "Blackbeard" Sjouwerman's wooden leg made a hollow sound as he angrily moved over the fore'deck. The second mate -again- had clicked on a link and infected his workstation. Blackbeard yelled: "Arg! The Cat O' Nine Tails For Careless Clickers!"

We had a good laugh this week after we read an article where I was interviewed by Antone Gonzalves at the CSO site. I must have sounded passionate about the topic of careless clickers (which I am by the way!), because Antone, I suspect tongue firmly in cheek, wrote his headline starting with: "Punish careless employees to reduce security breaches"... (link below)
During the interview, I explained an important reason for our excellent success rate in bringing the Phish-prone percentages down so much; employees' awareness comes up to the point they realize there are consequences when they click on a phishing link.
We did a study on 291,000 employees of 372 companies over a 12-month period. The initial average Phish-prone percentage was about 16 percent. Then we trained them all, stepping them through on-demand web-based Kevin Mitnick Security Awareness Training and continued to send Phishing security tests year-round. The Phish-prone percentage after 12 months dropped to just over 1 percent. Fantastic results, here is how the graph looks:
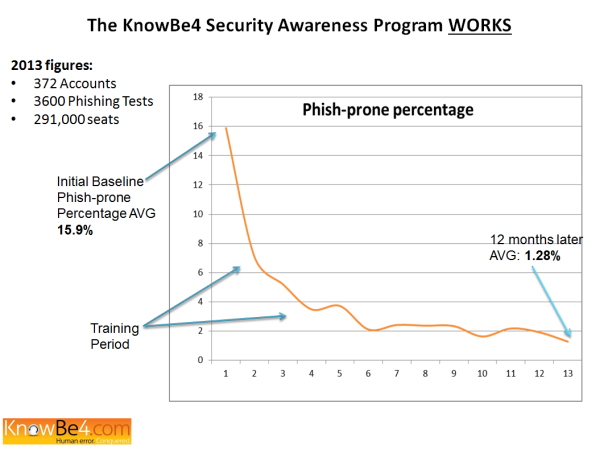
The combination of an initial baseline Phish-prone percentage, then training, followed by very regular simulated phishing attacks turns out to be an effective best practice with measurable results. Also the fact that clickers do get tracked, and the possibility that repeat offenders could be called in for a chat with their supervisor or HR and held accountable, makes for a miraculous change in employee behavior.
There are also ways to do it wrong. Only relying on what the industry calls "embedded" or "point-of-failure" training is ineffective. A brand new scientific study shows that sending one phishing attack every 90 days, with a short remedial training if they click on the link, simply does not work. Here is the GovInfoSecurity site with an audio interview and study results:
http://www.govinfosecurity.com/interviews/training-doesnt-mitigate-phishing-i-2148?
Here is the 10-page PDF with the actual study done by MITRE, I3P Dartmouth College and Vanderbilt University, which makes for interesting reading:
http://www.computer.org/cms/Computer.org/ComputingNow/pdfs/IEEESecurityPrivacy-SpearPhishing-Jan-Feb2014.pdf
And oh, if you want to have a good chuckle, here is the link to the article at CSO:
http://www.csoonline.com/article/746986/punish-careless-employees-to-reduce-security-breaches-vendor-says?
Scam Of The Week: "Customer Service Center"
Fake customer service center notifications are used to spread malware. Emails that claim to be from a "Customer Service Center" are being sent out by cybercriminals in an effort to distribute a piece of malware.
The emails say that they "have received your order and will process it in three days." The specifications of the order are attached with a link, and then they end off with their best regards. The link doesn’t point to a document though, but to a zip file which is infected with malware.
Note that there are several versions of this scam going around. Some of them are from a "Client Management Department". Warn your employees that this scam is doing the rounds and to STOP, LOOK, THINK before they click.
Quotes of the Week
"Every generation welcomes the pirates from the last." - Lawrence Lessig
"There comes a time in a man's life when he hears the call of the sea. If the man has a brain in his head, he will hang up the phone immediately." - Dave Barry
Thanks for reading CyberheistNews! Please forward to your friends. But if you want to unsubscribe,
you can do that right here
|

Your End-Users Are The Weak Link In Your Network Security
 Today, your employees are exposed to Advanced Persistent Threats. Trend Micro reported that 91% of successful data breaches started with a spear phishing attack. IT Security specialists call it your 'phishing attack surface'. The more email addresses that are exposed, the bigger your attack footprint is, and the higher the risk. Today, your employees are exposed to Advanced Persistent Threats. Trend Micro reported that 91% of successful data breaches started with a spear phishing attack. IT Security specialists call it your 'phishing attack surface'. The more email addresses that are exposed, the bigger your attack footprint is, and the higher the risk.
It's often a surprise how many of your email addresses can be found by the bad guys. Find out now which of your email addresses are exposed. The Email Exposure Check (EEC) is a one-time free service. We often show surprising results. An example would be the credentials of one of your users on a crime site. Fill out the form and we will email you back with the list of exposed addresses and where we found them.
Sign Up For Your Free Email Exposure Check Now:
http://info.knowbe4.com/free-email-exposure-check-14-01-28

Win $500. Participate in the 2014 State of Security Survey
KnowBe4 and ITIC’s joint 2014 State of Security Survey is live! The survey polls organizations on their current security practices with respect to BYOD, the status of their security mechanisms (e.g. AV software, intrusion detection, firewalls and encryption) as well as the current and planned measures organizations are taking to safeguard their data and networks..
When you complete this survey, you will be able to enter our sweepstakes for a chance to win a $500 Amazon.com Gift Card! And there are other prizes too. The Deadline to complete the survey is: XXX
The survey should take only about 5 minutes to complete. All responses are confidential. As always, anyone who completes the survey AND leaves an essay comment with their contact information is eligible to win one of two additional prizes.
First prize for the best essay comment is a $200 Amazon gift certificate; second prize is a $100 Amazon gift certificate. To be eligible to win the prizes you must leave your email address along with your comment in the comment box of the last question. No sales people will call you and we never share your information with anyone.
Once the survey results are tabulated we will post an Executive Summary in Cyberheist News and on the ITIC Website: www.itic-corp.com. Anyone who completes the survey is eligible to receive a complimentary copy of the full Report when it’s published. All you have to do is Email ldidio@itic-corp.com or stus@knowbe4.com.
Here’s the link to the survey:
https://www.surveymonkey.com/s/XC6KL2J
Thanks in advance for your participation!

Exposed Data Records Grew Five-fold In 2013
Cybercriminals exploiting weaknesses in how users employ passwords is a significant factor behind an increase in records exposed in breaches during 2013, says Craig Spiezle of the Online Trust Alliance.
The alliance - a not-for-profit group of technology and security providers, online security and privacy advocates and government agencies that promotes online trust - this week issued its annual Data Protection and Breach Readiness Guide. The alliance claims that its research verifies that more than 740 million records were exposed in 2013 data breaches worldwide, making last year the worst ever for records exposure.
"Cybercriminals are getting very, very smart," Spiezle says in an interview with Information Security Media Group. "They're recognizing that consumer are sometimes lazy and they reuse passwords and user names. So if they're able to compromise a very large target, then they use those to compromise other accounts downstream."
Spiezle says the number of data breaches in 2013 was about the same as in 2012, but the amount of credit card numbers and Social Security numbers exposed in breaches grew five-fold in just one year.
The alliance analyzed 500 breaches and determined that 89 percent of them could have been avoided if organizations implemented basic security controls and best practices, he says. Here is the 8:46 minute audio interview at GovInfoSecurity:
http://www.govinfosecurity.com/interviews/records-exposed-hit-new-high-in-2013-i-2166?rf=2014-01-24-eg

AIG: Cyber Insurance Sales Have Risen By 30%
Multinational insurance provider AIG today told The Financial Times that sales of cyber insurance had jumped up by 30 percent in 2013 when compared with the year before.
What we've being seeing is significant growth, said Tracie Grella, who oversees AIG's cyber insurance initiatives as the head of professional liability. She added that cyber insurance had jumped by 30 percent on a year-over-year basis in 2013.
Despite this, there are conflicting figures on how just big cyber insurance has become. For all the prominent hacks against the likes of Target, a report from Experian late last year found that just 31 percent of US companies had cyber insurance policies in place. However, another study from risk management research firm Betterley Risk Consultants found that the annual gross premium for US cyber insurance policies was USD $1.3 billion.
It is perhaps no surprise then that one information security expert believes that it is still early beginnings for the nascent cyber insurance market.
"It's an immature market," said Karl Schimmeck, VP of financial services operations at Sifma, an industry group for financial companies that last year spearheaded a simulated wide-scale cyber attack on Wall Street, when speaking to the FT.
The risks are not very well understood. There's not a lot of historical information that insurance companies can call on to quantify their risk. That's part of the problem.
Even AIG's own CEO, Peter Hancock, confessed at a recent conference that the market has plenty of growth ahead.
"This is still a very small market that gets more talk than action, but it is a growth opportunity," said Peter Hancock, executive vice president of American International Group Inc and CEO of the insurer's property/casualty unit.
Speaking shortly after the announcement, Lior Arbel, the CTO of information security firm Performanta, said that the figure was welcome news, but worries that the policies themselves may not cover enough.
"It is not surprising given the growing prevalence of cyber-attacks that insurance to protect a company's assets from the danger is also growing to match the threat," Arbel told SCMagazineUK.com.
"However, although insurance is important, it ignores that the damage from a cyber-attack goes far beyond specific infrastructure or hardware damages. The full effect of a cyber-security attack could involve not only the loss precious lost data, and a loss of trust, but also result in irreparable reputational damage with customers.
Priority for budget must therefore be in technologies and strategies to prevent the cyber-attack in the first place. Businesses need to take proactive steps to ensure its information is properly monitored and secured, from external and internal threats, with the implementation of an effective Data Loss Prevention system.
"If a company or its customer data is stolen, no amount of insurance money will win back confidence in the company." said Ashish Patel, regional director at Stonesoft, a McAfee Group Company, added that this is the latest sign that organizations are beginning to take cyber attacks seriously.
"This growth highlights the seriousness with which organizations are now taking the credibility of cyber-attacks with the digitization of business," he told SCMagazineUK.com.
Mass investment in insurance indicates that many businesses are out of their depth and are starting to realize that they now need to view cyber security as a whole package. This includes prevention techniques, mitigation, defense strategies and also compensation should the worst happen. Link to article:
http://www.scmagazineuk.com/aig-cyber-insurance-sales-have-risen-by-30/article/329623/

Cyberheist 'FAVE' LINKS:
* This Week's Links We Like. Tips, Hints And Fun Stuff.
Super Fave. It's fascinating to see how this singer is being transformed in real-time using common Photoshop techniques and enjoy listening to a great song at the same time. Wow. You really cannot trust what you see on TV:
http://www.flixxy.com/amazing-photoshop-transformation-in-music-video.htm?
Five Doritos ads made by fans, two of them are going to make it to the Superbowl!
http://www.fastcocreate.com/3024352/doritos-unveils-its-five-super-bowl-ad-finalists
What happens when a Porsche 911 and a Citroen DS make a baby?
http://www.brandpowder.com/911-ds-the-perfect-car/
An amazing 10-year-old dancer from Osaka, Japan. It seems that kids are becoming pros at a very young age now:
http://www.flixxy.com/10-year-old-dancer-in-osaka-japan.htm?
Whether you're a Spy School graduate or just a weekend spy hobbyist, these gadgets are true essentials. Destroy this message after you read it!):
http://fancy.com/giftguide/list/39399340
Inside the Ducati factory: Building the 1199 Panigale from the ground up:
http://www.gizmag.com/ducati-factory-photos-pictures/30089/
Adventurous cat 'Didga' rides on her skateboard through the streets of Coolangatta, jumping on, off, up and even over obstacles - including a Rottweiler dog:
http://www.flixxy.com/cat-skateboarding-adventure.htm?
Dilbert Strip - "I need help with my computer". LOL:
http://dilbert.com/strips/comic/2010-06-27/
|

