Arg! The Cat O' Nine Tails For Careless Clickers!
Captain Stu "Blackbeard" Sjouwerman's wooden leg made a hollow sound as he angrily moved over the fore'deck. The second mate -again- had clicked on a link and infected his workstation. Blackbeard yelled: "Arg! The Cat O' Nine Tails For Careless Clickers!"

We had a good laugh this week after we read an article where I was interviewed by Antone Gonzalves at the CSO site. I must have sounded passionate about the topic of careless clickers (which I am by the way!), because Antone, I suspect tongue firmly in cheek, wrote his headline starting with: 'Punish careless employees to reduce security breaches'
During the interview, I explained an important reason for our excellent success rate in bringing the Phish-prone percentages down so much; employees' awareness comes up to the point they realize there are consequences when they click on a phishing link.
We did a study on 291,000 employees of 372 companies over a 12-month period. The initial average Phish-prone percentage was about 16 percent. Then we trained them all, stepping them through on-demand web-based Kevin Mitnick Security Awareness Training and continued to send Phishing security tests year-round. The Phish-prone percentage after 12 months
dropped to just over 1 percent. Fantastic results, here is how the graph looks:
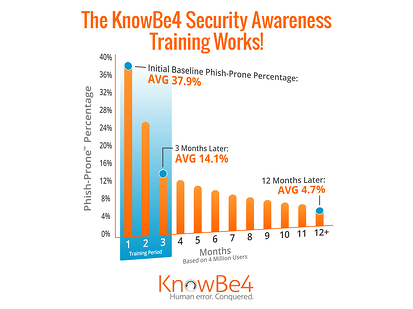
The combination of an initial baseline Phish-prone percentage, then training, followed by very regular simulated phishing attacks turns out to be an effective best practice with measurable results. Also the fact that clickers do get tracked, and the possibility that repeat offenders could be called in for a chat with their supervisor or HR and held accountable, makes for a miraculous change in employee behavior.
There are also ways to do it wrong. Only relying on what the industry calls "embedded" or "point-of-failure" training is ineffective. A brand new scientific study shows that sending one phishing attack every 90 days, with a short remedial training if they click on the link, simply does not work. Here is the GovInfoSecurity site with an audio interview and study results:
http://www.govinfosecurity.com/interviews/training-doesnt-mitigate-phishing-i-2148?
Here is the 10-page PDF with the actual study done by MITRE, I3P Dartmouth College and Vanderbilt University, which makes for interesting reading.
http://www.computer.org/cms/Computer.org/ComputingNow/pdfs/IEEESecurityPrivacy-SpearPhishing-Jan-Feb2014.pdf
And oh, if you want to have a good chuckle, here is the link to the article at CSO:
http://www.csoonline.com/article/746986/punish-careless-employees-to-reduce-security-breaches-vendor-says?




