Kelly Jackson Higgins at DarkReading wrote: "Advanced persistent threat (APT)-style attacks may be even more pervasive than thought: Organizations have suffered on average of nine such targeted attacks in the past 12 months, a new study finds.
Even more chilling: Nearly half of those organizations say the attackers successfully stole confidential or sensitive information from their internal networks, according to a new report by the Ponemon Institute called "The State of Advanced Persistent Threats," which was commissioned by Trusteer. Ponemon surveyed 755 IT and IT security professionals who have had firsthand experience with prevention or detection of targeted attacks on their organizations."
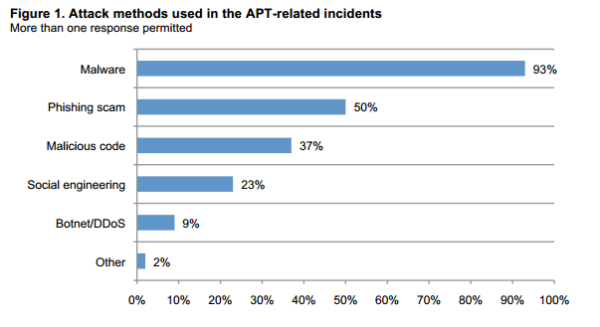
The graph above describes the way the top six attack methods the bad guys used got into the network. Very interesting to see that phishing and social engineering are well up there.
Some more highlights:
- Ponemon found that it took victim organizations painfully long periods of time to even discover they had been hit by these attacks. On average, these attacks went undiscovered for 225 days, and nearly 70 percent of them learn from a third party.
- 48 percent say targeted attacks have either rapidly increased or increased in same period.
- Current technology controls against APTs are not working. Seventy-two percent of respondents say exploits and malware have evaded their IDS and 76 percent say they have evaded their AV solutions.
- And not surprisingly, the root of much of the APT troubles in these organizations is lack of budget. Nearly 70 percent say their budgets are inadequate for fighting APTs. It would be highly beneficial to include effective security awareness training in that budget.