CyberheistNews Vol 2, #33
Editor's Corner
[caption id="attachment_1367" align="alignleft" width="150" caption="Stu"]
 [/caption]
[/caption]
Olympics Scam Roundup
The bad guys are at it again! Please forward this to all employees,
because it's rush hour with a host of Olympics-based scams.
Organizers have recorded 124 different scams so far but expect double
or more. First, there is an "Invitation FACEBOOK - Olympic Torch"
chain letter. It claims that your machine will be infected with
malware but the whole thing is a hoax. Think before you click and
do not forward.
Next, scammers prey on Olympics Mobile game players. Not long ago,
organizers of this years Olympic Games released London 2012
Official Mobile Game, a fun smartphone app for Android, iOS, and
Blackberry users. But there are a few Russian websites claiming
to be legitimate app markets and they host malware claiming to
be the official London 2012 game. Be very careful downloading
games for your smartphone.
Then, there is a blizzard of bogus Olympics-themed emails that try
to steal money and/or information. They offer fake last-minute
tickets, memorabilia, tell you that you have won an "Olympic lottery"
or that you can sign up for temp jobs online and make some extra
money. These scam emails use well known brands, or even spoof the
London Olympics. Delete all of these immediately.
Especially do not click on any emails with pictures or videos
about the Olympics, because clicking on one of these has a very
high chance to infect your workstation with malware. Even search
results on Google could be infected links so be careful.
Last but not least, be particularly wary of text messages on your
phone, that claim a golden medal win, or something else 'exciting'.
The safe way to get information about the Olympics online is to
go their official website. Here is the link to their 'stay safe
online' tips, which also list 70 websites that sell bogus tickets:
http://www.london2012.com/news/articles/www.london2012.com/about-this-website/stay-safe-online.html
No, You SHOULD Invest In Security Awareness Training
You probably read my editorial last week about Dave Aitel who took
the position that security awareness training was
not necessary.
Well, Ira Winkler at the Chief Security Officer (CSO) website makes
the case for the importance of security awareness training in his
response to Aitel's article.
I'm grabbing a few lines out of his article, and suggest you read
it, as it has great ammo to get approval for budget: "Every security
measure, technical or otherwise, has and will fail again at some point
in time. If you don't realize that, you really suck as a security
professional. The definition of "security" is literally "freedom from
risk." You will never be free from risk in the real world. What
"security" professionals are actually performing is "risk management."
"Awareness mitigates non-technical issues that technology can't, that
CISOs and other security managers are responsible for protecting
information in all forms, and that in many cases awareness programs
are not optional. The fact of the matter is that no security measure
should be measured by the standard of perfection. The real standard
is return on investment. By that standard, you will find that security
awareness is one of the most reliable security measures available."
He's saying it better than I have up to now. Here is his whole article.
Bookmark that URL and send it to your managers, it's worth it!
security-awareness-can-be-the-most-cost-effective-security-measure?">http://www.csoonline.com/article/712162/
security-awareness-can-be-the-most-cost-effective-security-measure?
Quotes of the Week
"The people can always be brought to the bidding of the leaders.
That is easy. All you have to do is tell them they are being attacked,
and denounce the pacifists for lack of patriotism, and exposing the
country to greater danger." - Nazi General Hermann Goering
"No man who ever held the office of President would congratulate a
friend on obtaining it." - John Adams
Please tell your friends about CyberheistNews! They can subscribe here:
http://www.knowbe4.com/about-us/cyberheist-news/
Released! Kevin Mitnick Security Awareness Training

Traditional once-a-year Security Awareness Training doesnt hack it
anymore. Today, employees are frequently exposed to sophisticated
phishing attacks, and your users are now the weak link in your
network security. They need to be trained by an expert, and after
the training stay on their toes, keeping security top of mind.
Click on the orange 'Get A Quote' button and find out how affordable
this is!
http://www.knowbe4.com/products/kevin-mitnick-security-awareness-training/
Busy? Just take 90 seconds and watch this brand new video about the
new Kevin Mitnick Security Awareness Training . You'll be glad you did:
http://www.knowbe4.com/video-kevin-mitnick-security-awareness-training/
Should Compliance Drive Security?
[caption id="" align="alignleft" width="300" caption="Should Compliance Drive Security?"]
 [/caption]
[/caption]Practically all of us accept credit cards, so we need to be PCI compliant. The question though is "If we comply, are we secure enough?". It's an easy assumption to make, and a lot of us take that route. We all have firewalls, antivirus and some of us run intrusion detection code, but these products mostly are making (educated) guesses about what is going on. These products are necessary, but they are not sufficient.
When I'm looking at the general threat landscape, I think that PCI compliance should not drive your security posture, it's to some degree the cart before the horse. Many of the recent companies that were the victim of a data breach were compliant. Your security practice will fail if compliance is driving, because as an organization you will fall in the trap of performing to the test instead of performing to the task. (Remember those "Paper MCSE's'? Many were not able to actually function as a Microsoft Certified System Engineer and failed miserably.)
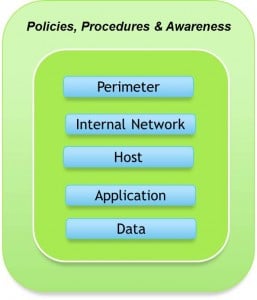
So, what to do?
Think like the attacker. Identify your key assets. Which of the data that we have is strategic IP, customer data and other sensitive / confidential information? The people that have access to this data have a target on their back, and will be exposed to sophisticated social engineering attacks. The attackers are going to go after your high-value systems and people. You need to identify these and prioritize their protection. One of the essential elements of Defense-in-Depth is the outer shell of Policies, Procedures and Awareness.
To make your organization a hard target that is resistant to Advanced Persistent Threats (APT) one of the pieces of the puzzle you need to have in place is security awareness training, and your employees need to be trained by an expert.
Chinese Hackers "Vacuuming Up" Huge Quantities of Proprietary Data
In the world of spying, you know there is a good chance you are
being observed and you take countermeasures if you can. In the case
of hacking this is more true than ever, and taking countermeasures
is hard. On July 26, 2012 Bloomberg published an in-depth article
about US intelligence who have been watching Chinese hackers for
a long time. The attacks started way in 2002, and the scope is
simply breathtaking. The data hoovered up was pertinent to the
financial crises in European, to lawyers who were filing trade claims
against Chinese exporters and more. The hackers broke into systems at
investment banks, technology companies, oil companies, and pharma.
The amount of data that has been stolen is hugely expensive in the
sense of economic damage. Here is the article. Warmly recommended:
http://www.bloomberg.com/news/2012-07-26/china-hackers-hit-eu-point-man-and-d-c-with-byzantine-candor.html
New Mac Trojan
Computerworld reported first about this new Mac Trojan which records
instant messages, Skype calls, browser use, then shoots the info to
a hacker-controller server. French security firm Intego discovered a
new Mac Trojan horse this week that is being used to target specific
individuals. The Trojan, dubbed "Crisis" by Intego -- a Mac-only
antivirus developer -- and called "Morcut" by Sophos, is espionage
malware that spies on victims using Mac instant messaging clients,
browsers and Skype, the Internet phoning software. According to Intego,
which published an initial analysis on Tuesday and has followed up
with more information since then, Crisis sports code that points to
a connection with an Italian firm that sells a $245,000 espionage
toolkit to national intelligence and law enforcement agencies. More:
New_Mac_Trojan_hints_at_ties_to_high_priced_commercial_hacking_toolkit?">http://www.computerworld.com/s/article/9229725/
New_Mac_Trojan_hints_at_ties_to_high_priced_commercial_hacking_toolkit?
One Black Hat Conference Highlight: NFC
If any of your employees have smartphones with near-field communications
(NFC), the talk by Charlie Miller should give you pause. He pointed at
one major area of failure, called 'feature-creep which is very common
in IT. It has happened with NFC on mobile devices. NFC in itself is cool
tech for payments authentication. However, there is a rub. It was
recently improved with a device-to-device (D2D) communication feature.
BZZZZZZ. Wrong Feature!
With D2D, you not only expose NFC-related apps, but if you can send a
phone to a web page without the user's knowledge or consent, the phone's
attack surface is suddenly enlarged to its web browser and everything
hooked into that browser like plugins, flash and the like. During
that Black Hat session, such an attack was shown to work, they used
a webkit exploit to do it. It would be a good idea to shut off your
phone's NFC until proven safe.
How To Spoof A MS-Exchange Server
If you use an Android or iOS device to connect to a Microsoft Exchange
server over WiFi, security researcher Peter Hannay may be able to
compromise your account and wreak havoc on your handset. At the Black Hat
security conference in Las Vegas, the researcher at Edith Cowan
University's Security Research Institute in Australia described an attack
he said works against many Exchange servers operated by smaller businesses.
Android and iOS devices that connect to servers secured with a self-signed
secure sockets layer certificate will connect to servers even when those
certificates have been falsified.
"It's really simple and that's what's disturbing to me," Hannay said. The
whole attack is just 40 lines of python and most of that is just connection
handling." Here is the whole article:
http://arstechnica.com/security/2012/07/spoofing-microsoft-exchange-server-how-to/
Need To Delete A BotNet From 532 Workstations and 32 Servers? Do It In 10 Minutes.

An end-user clicked on a phishing link and a worm infected his whole
network. How do you get rid of it?
1) Find out what the name is of the executable.
2) Create a Policy and tell it: a) Delete executable b)
Block it from running.
3) Assign the policy to all infected servers and
workstations.
Voila! 10 minutes later the malware is deleted and blocked
from even starting up. The product to use? InstantRevert! Real-time
compliance bought to you by KnowBe4. Learn more about it here:
http://www.knowbe4.com/products/instantrevert/
Cyberheist 'FAVE' LINKS:
* This Week's Links We Like. Tips, Hints And Fun Stuff.
SUPER FAVE: World's Fastest Roller-Coaster - Ferrari World Abu Dhabi:
http://www.flixxy.com/worlds-fastest-roller-coaster-ferrari-world-abu-dhabi.htm
Queen Elizabeth's Olympics Helicopter Jump with James Bond. Now this
is a -safe- Olympics video to watch!:
http://www.flixxy.com/queen-elizabeth-olympics-helicopter-jump-with-james-bond.htm
A fantastic pit stop of Sebastian Vettel where his team did their job
in just 4 seconds. Impressive isn't it? I wish my dealer was that fast:
http://www.flixxy.com/f1-sebastian-vettel-pit-stop-in-4-seconds.htm?
Wow, this guy used a 3D printer to create a working (!) AR-15 receiver:
http://www.gizmag.com/first-3d-printed-firearm/23473/?
A beautiful short film shows a frightening future filled with Google Glass-like devices:
http://www.flixxy.com/sight-systems-short-film.htm
Ever reached for something and gave up, thinking it was too hard? This
kitty cat has persistence and doesnt give up:
http://www.flixxy.com/clever-kitty-catches-hard-to-reach-balloons.htm
Five guys take same photo for 30 years every 5 years:
http://www.cnn.com/2012/07/26/travel/friends-summer-photo-tradition/index.html?
The Danish Air Force landed a Hercules C-130 transport aircraft on a
beach, turned around and took off. Here is a view from the cockpit and
from the ground:
http://www.flixxy.com/danish-c-130-hercules-lands-and-takes-off-on-a-beach.htm
A foreign tourist experiences the beauty of Crete and the warmth and
optimism of its people, in contrast to the bleak picture painted by the
news media:
http://www.flixxy.com/the-island-of-crete-greece-see-for-yourself-feel-for-yourself.htm
If you enjoyed the original 'Evian Babies', you may have fun watching them
perform to "The Rollerskate Song" by folk singer Melanie:
http://www.flixxy.com/evian-babies-and-the-rollerskate-song-by-melanie.htm
This is what a six-rotor Wankel looks and sounds like. Likely to be dropped into
a drag-racer. Wow:
http://www.autoblog.com/2012/07/27/this-is-what-a-six-rotor-wankel-looks-and-sounds-like/
Cute bear fave of the week: It is the worst nightmare of any parent, but luckily
for this bear mum, she was given a helping hand after losing her youngsters:
http://www.flixxy.com/bear-cub-rescue.htm




