The biggest fundamental problem with online financial activity is that for most of us, an account name and a password is all that's needed to gain access to accounts and account controls. Sure, some banks use so-called "challenge-response" mechanisms (pre-defined questions to which users provide pre-supplied answers) but that overlooks that over time any collection of challenge-response text pairs will come to light when keylogging comes into play. Alas, the same mechanisms that permit harvesting of accounts and passwords also permit harvesting of challenge-response texts as well. Challenge-response adds somewhat to security, but not a whole lot (not surprisingly, security experts also observe that multiple authentication factors of the same type are just barely better than only a single instance of the same type).
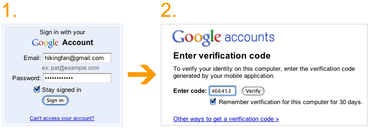
Google's about to change all that for its accounts. Users will soon be asked to opt into a 2-step sign-on procedure that retains the current username (or e-mail address) and password, but which also sends a six-digit numeric code to an associated mobile phone by voice, SMS text, or a smartphone app. Users must then enter that code to verify their identity before the login process completes. We think this is just the ticket, and hope that any and all Web sites that manage anything financially related, or with monetary values or impact, should do likewise ASAP. Here's a screenshot of this process, courtesy of the "Googling Google" blog by Sam Diaz for 2/10/2011 ("Your online deadbolt...").
Google's about to change all that for its accounts. Users will soon be asked to opt into a 2-step sign-on procedure that retains the current username (or e-mail address) and password, but which also sends a six-digit numeric code to an associated mobile phone by voice, SMS text, or a smartphone app. Users must then enter that code to verify their identity before the login process completes. We think this is just the ticket, and hope that any and all Web sites that manage anything financially related, or with monetary values or impact, should do likewise ASAP. Here's a screenshot of this process, courtesy of the "Googling Google" blog by Sam Diaz for 2/10/2011 ("Your online deadbolt...").
Security experts like to talk about three types of authentication factors — namely,
- Something you know: this includes account names, passwords, pass phrases, challenge-response text, and anything you're supposed to keep locked away between your ears
- Something you have: this includes things like security tokens, smart cards, and even cellphones or smartphones because all are equipped with unique identifiers so that even if there are lots of such things loose in the world, as user must present the one that goes with his or her identity to verify said identity
- Something you are: this is where biometrics come into play, and includes voiceprints, fingerprinters, facial recognition, iris scans, hand geometry, and anything else that might be measured on your person and compared to data obtained on the same physical features under tightly controlled conditions
Using multi-factor authentication is nearly always better than using only a single factor, where the preceding list also orders those factor types by increasing strength. For the best systems, customers combine account and password data with something they have or something they are to ensure a more reliable authentication of their identities.
Google has snapped to something nearly everybody has — namely, a mobile phone number — and will use it to provide a second and reasonably strong identification factor. Of course, thieves who kidnap their victims can easily bypass this factor by taking possession of their cellphones, but that ups the ante beyond what's feasible for cyberthieves, especially those operating offshore. We hope Google turns this into an API and makes it freely and widely available to anyone and everyone. It could be a major factor in thwarting the high rates of financial fraud that the current Internet architecture enables.
12+ Ways to Hack Multi-Factor Authentication eBook
 All multi-factor authentication (MFA) mechanisms can be compromised, and in some cases, it's as simple as sending a traditional phishing email. Want to know how to defend against MFA hacks? This eBook covers over a dozen different ways to hack various types of MFA and how to defend against those attacks.
All multi-factor authentication (MFA) mechanisms can be compromised, and in some cases, it's as simple as sending a traditional phishing email. Want to know how to defend against MFA hacks? This eBook covers over a dozen different ways to hack various types of MFA and how to defend against those attacks.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/12-way-to-hack-two-factor-authentication





