Last Thursday, we posted a blog entitled "Phishing Primer, Part 1;" here is Part 2 in that ongoing series of brief expositions on this fascinating subject that is also a clear and present danger for Internet users of all stripes and kinds, particulary those surfing the Web or reading e-mail on the job. If you re-visit Part 1, you'll get more information about what constitutes a phishing attempt, but what counts most for Part 2 is the notion that the hidden phishermen (or ...women) package their messages (and related Web pages) to look as much like the real thing as they possibly can.
In this blog, we'd like to point out some important ways in which users can tell when they're being phished, so they will know to avoid the lure and stay out of trouble. Here's a fictional example of a phishing message from the "First Generic Bank," courtesy of phishtank.com:
In this blog, we'd like to point out some important ways in which users can tell when they're being phished, so they will know to avoid the lure and stay out of trouble. Here's a fictional example of a phishing message from the "First Generic Bank," courtesy of phishtank.com:
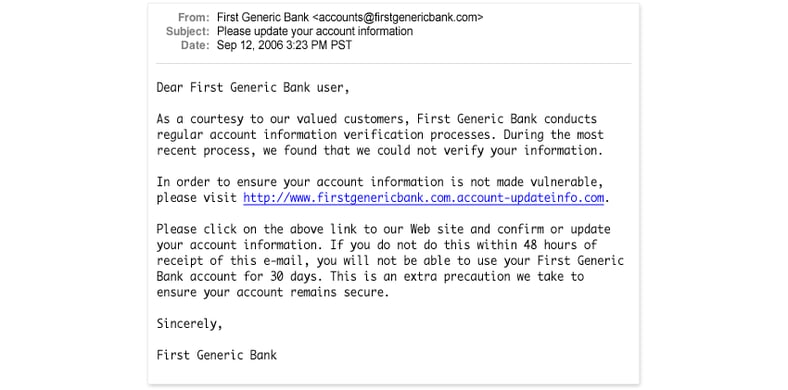
While this message does lack some tell-tale ingredients, it does display the most important features common to all phishing messages:
- It does not include a personalized greeting. When was the last time any company with which you do business actually lumped you in with all their other customers? That's right: never. This kind of greeting occurs only in phishing messages and in bulk e-mail ("Dear Recipient/Homeowner/Resident/..."), which can probably also be described as a marginally more acceptable form of trolling for customers.
- It incites the reader's interest and participation with an official sounding but completely bogus activity "regular account information verification process" and indicates further that the sender was unable to verify such information. Of course they can't verify it: they're not the bank in question (which would be in breach of its fiduciary responsibilities if it couldn't verify that info)!
- It presents the lure by suggesting that it is advisable "to ensure your account information is not made vulnerable," then presents a link, then threatens to withhold access to the account for thirty days if the link isn't clicked — and soon!
- Implicitly and explicitly the e-mail asks for your account information. When and if such requests are legitimate (and they are only seldom, if ever legitimate) they will usually come in writing by regular mail, and they will never ask you to click a link to provide such information (you may be instructed to log into the sender's web site, but will also have to option of calling in by phone instead).
The sole intent of this message is to get users to click the link that reads http://www.firstgenericbank.com.account-updateinfo.com. This is a rather unsubtle phishing attempt, because the domain name that's in use is actually account-updateinfo.com, despite the appearance of First Generic Bank's likely URL (www.firstgenericbank.com) at the beginning of the domain name portion of that URL. More sophisticated lures map genuine domain names (www.firstgenericbank.com) to IP addresses so that hovering the cursor over them turn up opaque strings of numbers like http://174.129.9.152/account-updateinfo/ (a little quick research will reveal that this is in fact the IP address for our very own server, and we hasten to point out that we don't phish, we teach others how to avoid this unpleasant fate). Far too many users do not know this is a very bad sign for a URL, and that it screams "do not click this link" to those in the know. But then "Do not click an e-mail link!" is the absolute watchword for accessing any kind of sensitive information, or visiting Web sites related to same, when it comes to responding to e-mail or visiting Web sites of dubious origin or reliability.
Other tell-tales of cruder phishing attempts you don't see in the First Generic Bank example, but which are well worth watching for include:
- Bad grammar or mis-spellings. For all kinds of good reasons, phishing attacks often originate from locations where the message writer is not a native speaker of the target language in which their messages appear. Though they might ask for forgiveness for their lack of fluency and letter-perfect correctness in that language, such elements shout "phishing attempt" to those who watch for such things regularly.
- Gibberish strings in a message, especially near or at the end: anti-spam software routinely creates message digests to detect and block phishing attempts once detected. By inserting randomly generated character data in messages (often at the end, where users are less likely to see them, especially if they include deliberate white space to hide from easy view) phishers seek to avoid ready detection.
- Use of link shortening tools to obscure target domain names: sites such as bit.ly, cli.gs, budurl.com, tinyurl.com, goo.gl and so forth, can take any URL and shorten them to strings such as http://goo.gl/m0GwG. Anything other than the target domain name (and only that name) showing up in a link is a big read flag labeled "Phishing at work!"
- Messages with strange subjects (or with strange characters in the subject line, which often include the string "iso"): these often show the handiwork of inexperienced spammers or phishermen who don't completely understand how to use the automated tools they use to broadcast large numbers of messages. These are overt formatting or usage issues related to those tools, and also indicate that something isn't quite right.
We could go on for some time in this vein, but hopefully you've got the idea about how to spot phishing at work. To see more examples, visit any or all of these Web pages:
- About.com: Washington mutual phishing e-mail, SunTrust phishing e-mail, eBay phishing scam, ... keep clicking "Next" to see more




