"The Internet is the crime scene of the 21st Century,"
–Cyrus R. Vance, Jr., District Attorney for New York County
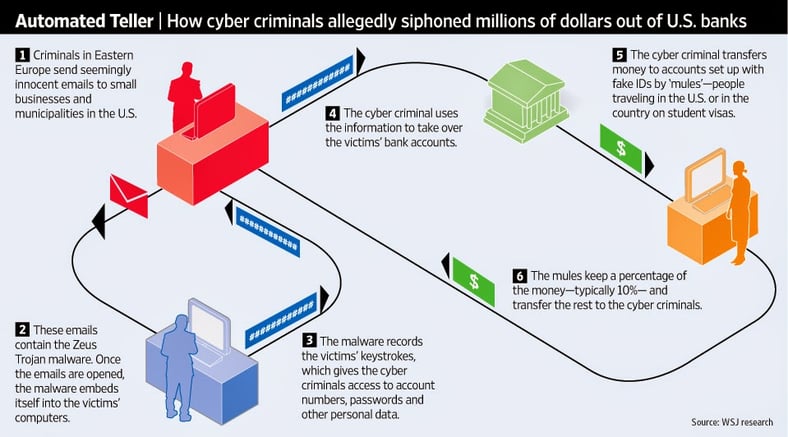
Here is a brief overview of how the bad guys do it:
- Criminals in Eastern Europe send seemingly innocent emails to small businesses and municipalities in the U.S. that are actually phishing emails.
- These emails contain the Zeus Trojan malware. Once an employee clicks on an email and infects their PC with malware.
- The malware records the victim’s keystrokes, giving criminals access to account numbers, passwords, and other personal data. This also allows the entire network to be hacked.
- The cyber criminals use this data to take over the victim’s bank accounts.
- They transfer money to accounts set up by people with fake IDs, called “money mules” - people traveling in the U.S. or in the country on student visas.
- The mules keep a percentage, usually about 10%, and transfer the rest out of the country to the cyber criminals.
Hacking is the new armed bank robbery, and all that's required for criminals to siphon millions of dollars is the internet. Over one hundred individuals have already been arrested in the U.S., U.K. the Netherlands and Ukraine in connection with this most recent cybercrime. According to the FBI, charges against these "Zeus Trojan" defendants include bank fraud, false use of passports and money laundering among others. Earlier estimations put the damage at around $3 million stolen from U.S. accounts and at least £6 million (about $9.5 million) stolen from U.K. accounts. Upon further investigation that figure is closer to $70 Million.
This cyberheist exactly follows the steps in the above illustration:
- Criminals in Ukraine, Latvia, Estonia, Balarus and Georgia sent phishing emails to an untold amount of victims, including individual citizens and banks themselves.
- Once those emails were clicked, Zeus malware is introduced to the entire network.
- The malware allowed criminals to obtain banking usernames and passwords.
- The hackers then took over the victims accounts, either moving the money overseas or taking out cash directly.
- Money mules in the U.S., U.K. and Ukraine transferred those funds back to the hackers. In this case the mulescharged came from Russia, Moldova, Ukraine, Kazakhstan and Belarus. The U.S. investigation centered around these money mules and that's how many of the criminals were caught.
- The mules kept around 8-10%, transferring the rest back to the criminals in Eastern Europe.
The Zeus Trojan used in this bank heist is a more sophisticated version of Zeus malware that has been around for at least the last several years. It used to be that cybercriminals could get ahold of the data and use it or sell it, now it allows these criminals to take funds directly from the banks into mule accounts. They are not going to stop there! There is an entire network of hackers and criminals in the black market with their own developers and tech support, constantly improving their methods to continue criminal activity.
Always making sure you think before you click on that email is of the utmost importance, you can really never be too careful. End-user security awareness training is one of the best defenses against these types of attacks. No amount of antivirus protection could have stopped this event, as soon as that email was clicked the victims were infected.
Learn more about what constitutes effective Security Awareness Training on our free whitepaper:





