 New data shows users aren’t scrutinizing emails used in business email compromise (BEC) attacks, allowing critical changes in banking details that would impact the victim's organization financially.
New data shows users aren’t scrutinizing emails used in business email compromise (BEC) attacks, allowing critical changes in banking details that would impact the victim's organization financially.
Someone sends an email to your Accounts Payable specialist stating they want to know the status of an invoice and – oh, by the way, please start paying us using these new banking details. The first part seems legitimate, but the second half should be raising all kinds of red flags!
According to new data found in Abnormal Security’s H1 2023 Email Threat Report, these are exactly the kind of emails that are being sent with a median open rate of 28%. That means over one-quarter are reaching the Inbox and being opened, and according to the report 15% of these are getting responses by users.
Here’s an example email from the report:
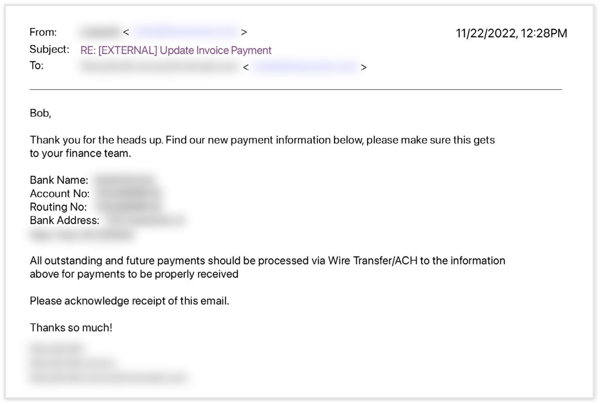
What’s also alarming is that only a meager 2.1% of attacks are reported by employees – this is either a case of they don’t know the difference, are indifferent themselves, or are too embarrassed to let the security team know they opened the email.
This is a prime case for the need of Security Awareness Training. By putting users through this kind of training, they begin to not only see the clear telltale signs of a malicious email, but also the need for them to play a role in the organization’s security (read: they need to remain vigilant against cyberattacks while they do their job!).
Abnormal also noted that BEC attacks have risen 178% over the last two years, demonstrating that this kind of attack is profitable and isn’t likely to die off anytime soon.
 Here's how it works:
Here's how it works:




