 Most social engineering scams search out their potential victims, often sending emails to known email addresses, sending chat messages to them or calling known phone numbers. The attackers take an active role in seeking out and making contact with their victims. For that reason, we often say that everyone needs to be initially suspicious of any unrequested contact, no matter how it arrives, that is requesting an action that if performed by the receiver, could harm their or their organization’s interests. We graphically represent that process and decision tree as the following:
Most social engineering scams search out their potential victims, often sending emails to known email addresses, sending chat messages to them or calling known phone numbers. The attackers take an active role in seeking out and making contact with their victims. For that reason, we often say that everyone needs to be initially suspicious of any unrequested contact, no matter how it arrives, that is requesting an action that if performed by the receiver, could harm their or their organization’s interests. We graphically represent that process and decision tree as the following:
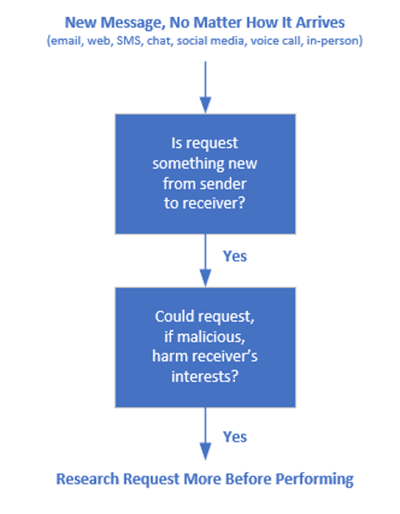
This logic works well in the vast majority of social engineering scams.
SEO Attacks
But a smaller minority of social engineering attacks get their power by waiting for victims to contact them. It can happen a variety of ways, with the most popular being poisoned Search Engine Optimization (SEO) attacks, where the attacker “seeds” websites with popular search terms, which leads potential victims using search engines to malicious sites, documents, and links.
For example, a common scam is fake tech support websites. The scammer first searches for and learns about popular technical troubleshooting issues, such as common Microsoft Windows errors. Then they will create dozens to hundreds of websites that contain the search terms that someone who is having difficulty with the error would type in a search engine to help find a solution to the error. Then, potential victims searching for help with that particular error have a good chance of being directed to the scammer’s malicious website, which attempts to get the user to download a malicious program or document.
Another recent example was fake, malicious websites set up with what looked like legal contract document templates. Victims, trusting that they have found free legal document templates, open the poisoned documents, launching further maliciousness. In this example, the involved terms involved many dozens of commonly searched legal documents and were rendered in six different languages. It was created by a malware-as-a-service known as GootLoader. It involved otherwise innocently compromised WordPress websites (which shared common vulnerabilities) with the ultimate objective to install other malicious malware programs.
Waterhole Attacks
The first time I remember reading about waterhole attacks was a decade ago when popular programming websites had been compromised and “free” code snippets and programs available on the sites were poisoned with malicious commands and links. Programmers who were going to these well trusted, legitimate websites were tricked into downloading these exploited programs and code snippets, then using them in their own environments and programs. The world’s biggest companies with the most mature programming teams had been tricked, including Apple, Facebook, and Microsoft. Today, GitHub is often used in the same way.
Programmers are not the only possible waterhole attack victims. Anyone can be a waterhole victim.
It is important that every user in your environment be educated on SEO and waterhole attacks. They need to understand that although most social engineering scams come into their inbox or phone, some attackers wait for potential victims to come to them. Users need to be made aware of such attacks, given examples, and told how to fight them, which is mostly teaching them not to download and execute untrusted documents and code. Users need to understand that any opening or execution of untrusted code could lead to their compromise. So, when in doubt, chicken out, and do not download the code or open the document. It is just too much risk to take.
 The ModStore Preview includes:
The ModStore Preview includes:




