By Eric Howes, KnowBe4 Principal Lab Researcher.
Anyone who works a job in the computer security industry inevitably develops a kind of dark appreciation for the mad skills so often demonstrated by the bad guys. They consistently deliver eye-popping innovation -- even if it's the kind of innovation that regularly causes massive headaches for all the rest of us.
But the bad guys have their off days, too. And when a bad guy operation goes off the rails, you can't help but smile. It's the purest form of schadenfreude.
The Email Account Credentials Phish
The credentials phish is the most common form of phishing email that we encounter. It's simple, straightforward, and it's been around since the very term phishing was itself coined. It's also remarkably successful, fooling inattentive and clueless users time and again.
One particular variant of this most basic phishing attack that we've been seeing a lot over the past six months is what we'll call the "email account credentials phish." In this phish potential marks are told that there is some problem or change with their email account that requires them to take action. Sometimes that action involves opening an attachment. Most often it involves clicking a link.
The beautiful thing about this particular credentials phish is that it allows the bad guys to spoof the target's own IT department or Help Desk. Senior executives might naively assume that company employees would be able to distinguish between emails originating from their own organization's Help Desk and those coming from malicious parties outside the organization. But we all know such an assumption would be foolish -- indeed, it would be downright dangerous.
The "email account credentials phish" is so common that we have several phishing templates available for our customers to use that are based on real bad guy emails that we've seen in the wild. Here are two of them:
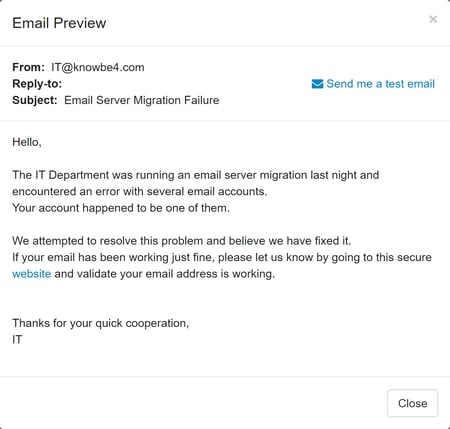
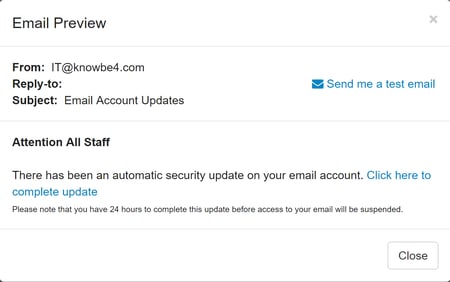
"Email Account Termination Final Warning!"
Earlier today we received the following "email account credentials phish" via the Phish Alert Button (PAB):
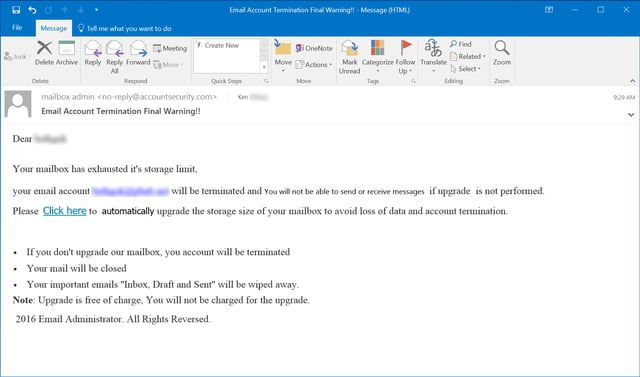
Yes, this phish has its share of problems -- glitches that should alert users that something is amiss. But the landing page that clueless clickers arrive at once they hit the "Click here" link is actually quite well done:
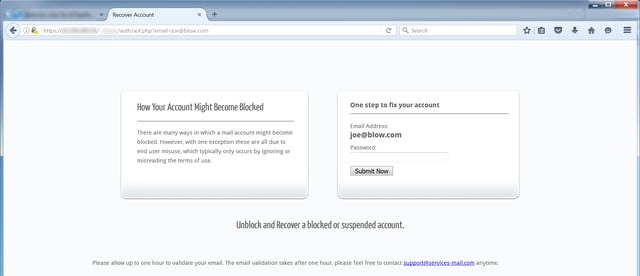
Someone obviously put some thought into this landing page. A helpful explanation of the situation is provided. The user's email address is automatically picked up from a URL parameter, meaning that users need only enter their passwords to complete this phish and deliver their email accounts into the hands of the bad guys. The bad guys even went to trouble of hosting this credentials phish on a secure host (note the https:// in the URL) to enhance its credibility in eyes of the rare user who might pay attention to such details.
And that's where things went wrong here. Because the vast majority of users will never see that thoughtfully crafted landing page. What they will see instead is something like the following:
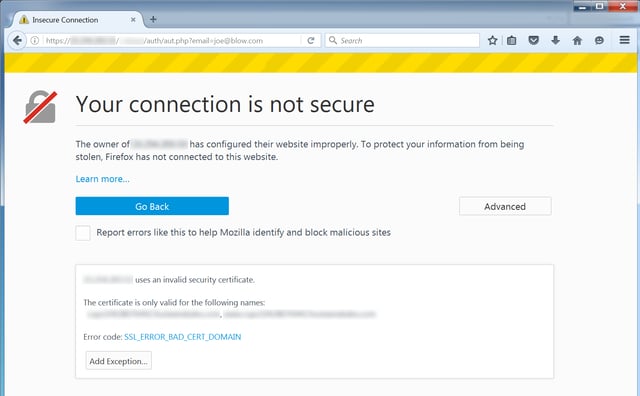
Whoops! All that care put into the landing screen, yet someone made a basic error in setting up the server with an SSL certificate. Although this particular warning screen is from Firefox, all the other major browsers throw similar warnings under these circumstances.
In our experience most users who encounter this kind of of SSL certificate warning screen will be stymied at this point, likely unable to proceed and unsure whether they should even try. That's a big fat FAIL for the bad guys (and a WIN for all the rest of us).
Who Gets the Last Laugh?
Unfortunately, we can't count on the bad guys making these kinds of errors on a regular basis. Although we do enounter the occasional bad guy fail with phishing emails (missing email attachments, incorrect file extensions, botched links, etc.), the odds are still heavily stacked against ordinary users when they enounter a phishing attack and get thrown into a cage match with the bad guys. In such a match-up, we all know who's most likely to end up face-first on the mat.
And that's why every organization needs to invest in new school security awareness training. Because the last thing any IT organization wants to do is to give the bad guys a good laugh -- especially when they're enjoying it on the way to the bank.
Free Phish Alert Button
When new spear phishing campaigns hit your organization, it is vital that IT staff be alerted immediately. One of the easiest ways to convert your employees from potential targets and victims into allies and partners in the fight against cybercrime is to roll out KnowBe4's free Phish Alert Button to your employees' desktops. Once installed, the Phish Alert Button allows your users on the front lines to sound the alarm when suspicious and potentially dangerous phishing emails slip past the other layers of protection your organization relies on to keep the bad guys at bay.

Don't like to click on redirected links? Cut & Paste this link in your browser:




