 Just when you thought everyone forgot about participation on the ill-famed cheaters website, a new phishing scam looks to use the breached data as the basis for extorting the site’s users.
Just when you thought everyone forgot about participation on the ill-famed cheaters website, a new phishing scam looks to use the breached data as the basis for extorting the site’s users.
Data breaches yield phishing scams. It’s a given at this point. And with the 32 million Ashley Madison accounts from 2015’s sensationalized breach including all kinds of personal details – from banking, to date of birth, to personal interests on the site, and more – it remains a pretty good basis on which to launch a full-scale attack on the site’s (hopefully) former customers.
One of the keys to a good phishing scam is context. The more contextually accurate the email message aligns with the recipient, the better the chances of success. In this case, because the details being leveraged are at very least former details, the scammers are hoping they are enough to capture the attention of their potential victims.
The emails ask for 0.1188 BTC or a little more than $1,000. If not paid, the email threatens to send the personal details provided in the email “and more” to “everyone who knows you”, providing a deadline of six days from now by which to pay the extortion fee.
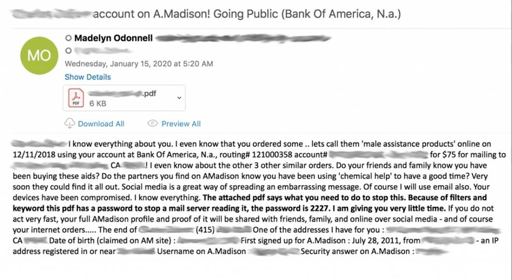
The email also includes a PDF attachment containing a QR code to help point the victim to an acceptable payment method.
While this email scam is simply after the recipient’s money, it could just as easily be a scam intent on installing malware, holding an organization for ransom, etc. Your organization should educate its users on scams like these (and the appropriate response of simply ignoring it) through continual Security Awareness Training. The reality of this scam is that it’s pretty benign if simply left alone; the same can be said for most phishing attacks that rely on the user engaging with the email, becoming emotionally connected with its message, and performing a desired action – be it clicking a link, opening an attachment, or replying. Educating users to identify and ignore these emails is not only best practice, but will help improve the organization’s security stance.
 Here's how it works:
Here's how it works:




