 The bad guys will try to take over accounts all the time. Logging onto someone's account with their credentials is usually a whole lot easier than trying to compromise the website directly.
The bad guys will try to take over accounts all the time. Logging onto someone's account with their credentials is usually a whole lot easier than trying to compromise the website directly.
Here's a short video I made on the topic.
Ultimately, when we're talking about account takeover, the underlying problem is actually all about password management.
Here’s a quick visual of some of the account takeover techniques covered is in this pyramid. It's in a pyramid as opposed to putting it in a list because when you put lists into a shape, it gives the impression that there is far deeper meaning to the work.
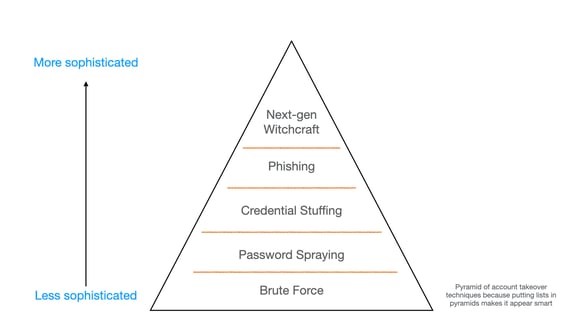
Source: Javvad Malik
Brute Force
Brute Force attacks are the least refined of attacks, and most websites should be able to detect where someone is trying to brute force accounts and stop them in their tracks. If your website can't do that, check the URL. If it says geocities.com, then you need to move elsewhere... or share details of your time machine.
Password Spraying
Password spraying comes up next as the more refined criminals approach. Rather than the caveman tactics of a brute force attack, it tries the most commonly-used passwords to try and break into accounts.
Both brute force and password spray attempts can usually be easily detected and stopped by website owners. From a user perspective, having a strong password is usually enough to deter those two attacks. However, having a strong password is not enough if it is reused across different sites.
Credential Stuffing
Credential Stuffing is the technique whereby criminals will harvest credentials from previous breaches and then use them to try to access other accounts.
For example, if the email ErichKron@Kron.com was breached on a small website, e.g., Boots4Kittens.Biz and the password used there was Javvads#1Fan, criminals will try that email and password combination on every other website they can think of.
It's why just having a strong password is not enough, rather it's important to have unique passwords across different websites.
Of course, advocating strong, unique passwords is easier said than done. With many people having more online accounts than they can recall, memorising individual passwords can be tough. That’s why a password manager can be a good investment. From a service provider perspective, it also makes sense to ban certain passwords to prevent users from selecting them. Many offerings like Microsoft Azure AD have comprehensive password protection features built in, which include global and custom banned password lists.
Now, if we reach a point where you are not choosing weak passwords, and you're using unique passwords for each site, and the website owner is taking precautions to prevent brute force or other attacks, the bad guys will dig in deeper.
Phishing
Phishing is probably one of the most popular routes taken in these circumstances. This occurs when bad guys impersonate a brand and send an email to its unsuspecting victims asking them to click a link and/or sign onto their account. This is what is happening whenever you receive an email claiming to be from Amazon / Apple / Insert brand here claiming there is an urgent issue with your account.
Once credentials have been phished, the bad guys don't need to worry about guessing, they have the exact password to the account they need.
Reducing Risk
Being a recovering consultant, it would be negligent of me to not point out the obvious that nothing is 100% and we're all about taking steps to reduce risk. But it's important to understand that this is a joint effort and that there are steps that both the users and service provider need to be taking.
I call this the anti-account takeover shared accountability model, which is depicted in the venn diagram below. Much like the pyramid above, it is only in diagram format for vanity purposes.
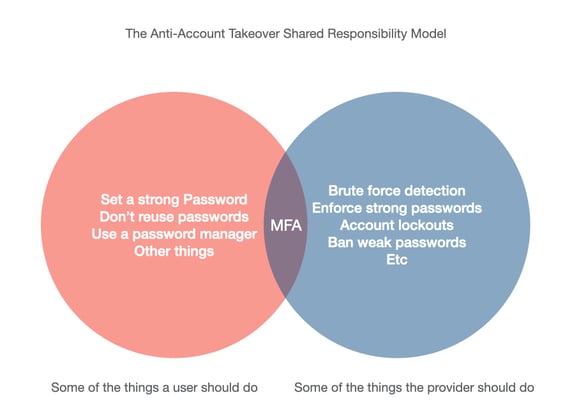
Source: Javvad Malik
Multi-Factor Authentication to the Rescue...
Eagle-eyed observers will note that multi-factor authentication (MFA) sits in the middle of the venn diagram. This is for two reasons. First, I needed something to overlap the two or it would have been just two circles, which defeats the object of a venn diagram. Second, because most providers will offer MFA, but not enforce it. Therefore, it's the user’s responsibility to find which MFA options are available and ensure they are taking advantage of it.
Of course, that doesn't apply to the corporate world where employers can enforce MFA on their staff, but that would break my venn diagram.
Personally, I'm a big fan of MFA. It's one of the best methods to greatly reduce overall risk. It reduces the need for the user to choose unique passwords, or even necessarily strong ones. That’s because if an attacker had the ID and password, they don't have the second (or third) factors needed to get into the account.
But is MFA enough? And this is where we get into the "your threat model is not my threat model" type of scenario, which is a technical way of saying, "let's agree to disagree.”
MFA isn't a panacea. There are many ways to bypass MFA. My colleague Roger Grimes has written extensively on the various different ways MFA can be bypassed. (Friendly plug, his book "Hacking Multifactor Authentication" is out later this year.)
Any security expert will tell you that nothing is perfect, which is why even with everything in place, you still need to monitor for intrusion attempts, or look for anomalous activity.
Having said that, for most organisations, educating your users along with implementing some basic protections will usually bring the risk of account takeover to an acceptable limit, as illustrated in the diagram below.
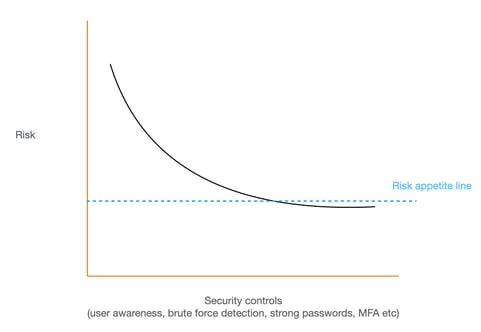
Source: Javvad Malik
You'll see the risk starts off high, and as you add more security controls, the risk becomes lower. The objective for most businesses isn't to bring the risk down to zero, rather it is to bring it within an acceptable risk limit, or risk appetite. Anything beyond that usually isn't financially smart (for the most part).
Burn Passwords!
Passwords are ultimately the biggest pain point. So, maybe removing passwords altogether is the answer. The FIDO Alliance has been working for a number of years to make the shift to a passwordless world easier. They’re doing this by having the user only authenticate to the local device they are on while the device stores a private key and the server holds the public key.
It's a good direction for the industry to move in, but it's worth bearing in mind that there are many instances where this is impractical (today) and full adoption will take time. Given that there are still so many organisations that rely on Windows XP, it may be a longer wait for complete adoption than we'd ideally want.
In closing, I realise that anytime a security professional mentions defence in depth, or layered security controls, people interpret that as expense in depth. In fact, it's the reason that passwords have remained in the mainstream for so long. They're comparatively cheap to use and maintain -- if they're forgotten, they can be easily reset. There's no learning curve for the majority of the population who may not be familiar with MFA offerings, and for developers who aren't up to speed with the FIDO standards.
Like I mentioned earlier, a lot of what your organisation chooses to do will be dependent upon your risk appetite and what controls will bring the level of risk down. The other way of looking at it is what the cost or effort of the control is versus the impact that it will have.
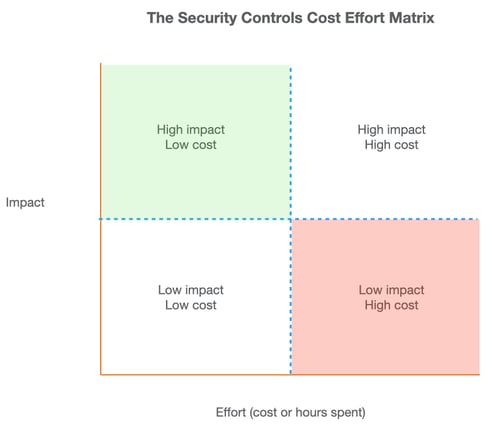
Source: Javvad Malik
The Security Controls Cost Effort Matrix is one of my favourite ways to visualise it. You want to avoid controls that are in the red quadrant in the bottom right, which have little impact in terms of lowering risk, and have a high cost. The top left is the ideal situation to be in, where you have high impact for low cost. The other two quadrants really do depend on your objectives. High cost and high impact in the top right usually makes sense for strategic projects, while the low impact, low cost in the bottom left can be reserved for quick wins, tactical improvements, and to satisfy an overly enthusiastic auditor.
Finally, remember to factor in all types of security controls, be they technical, procedural, or human related. Many offerings provide a robust set of technical controls. Make sure you're using those to the full extent of their ability before searching out another technical product. Similarly, bring your employees and customers on your side with new-school security awareness training. Work with them to help build a great user experience and empower them to make better security decisions. Working together, we stand a better chance to defend against security threats.
 Here's how it works:
Here's how it works:




