 Nicknamed AVGater by Austria-based security consultant Florian Bogner, he discovered an exploit within Antivirus software that takes advantage of the “restore from quarantine” function and allows a user to move a piece of malware from the quarantined folder to somewhere else on the victim’s computer, allowing the malware to be executed.
Nicknamed AVGater by Austria-based security consultant Florian Bogner, he discovered an exploit within Antivirus software that takes advantage of the “restore from quarantine” function and allows a user to move a piece of malware from the quarantined folder to somewhere else on the victim’s computer, allowing the malware to be executed.
Bogner, who works for Kapsch, says he has notified the vendors of all the antivirus programs that contained the flaw. Some of the companies have released updates that address the issue, including Emisoft, Ikarus, Kaspersky, Malwarebytes, Trend Micro, and ZoneAlarm.
While penetration testing, Bognor infected clients’ PCs using a traditional phishing e-mail technique. The malware would then get quarantined by the AV program, and he would exploit vulnerabilities in the software that allowed unprivileged users to restore the quarantined files. Abusing a windows feature called NTFS file junction point allowed him to relay the file to a privileged directory of his choosing, such as a folder within C:\Program Files or C:\Windows. The method also abuses the Dynamic Link Library search order feature. The malware could then run with full privileges.
Bogner says the best way to prevent being affected by AVGater is to keep your antivirus programs up to date, which is always good advice. For enterprises users, he suggests removing the ability to restore files from quarantine.
Does *your* antivirus protect you against Ransomware?
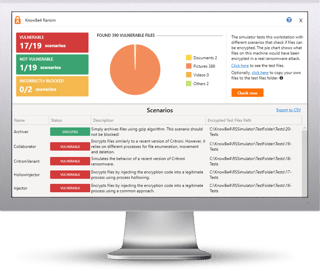 We’ve added three new test scenarios to our Ransomware Simulator "RanSim" making the total 13, giving you a quick look at the effectiveness of your existing endpoint protection against these additional nasty ransomware strains that are in the wild:
We’ve added three new test scenarios to our Ransomware Simulator "RanSim" making the total 13, giving you a quick look at the effectiveness of your existing endpoint protection against these additional nasty ransomware strains that are in the wild:- CitroniVariant - A specific scenario designed to simulate the distinct file encryption activity of Critroni/CBT ransomware.
- Collaborator - An advanced scenario that spawns multiple processes to carry out encryption routines.
- VirlockVariant - One of the more complex scenarios, designed to simulate a variant Virlock that uses watchdog processes to keep encryption processes restarted.
- 100% harmless simulation of a real ransomware infection
- Does not use any of your own files
- Tests 13 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
source: TechSpot





