 The traditional malicious software detection approach is far from being sufficient, especially in corporate environments. More and more it's found that antivirus products can take months before adding the algorithms to recognize the more complex threats.
The traditional malicious software detection approach is far from being sufficient, especially in corporate environments. More and more it's found that antivirus products can take months before adding the algorithms to recognize the more complex threats.
A recent study from Damballa, a security company offering solutions against advanced cyber threats, revealed that malware could spend as much as six months on a system before it is identified using signature-based detection.
Damballa's CTO Brian Foster said: "For years now the industry has discussed the declining effectiveness of preventative controls like antivirus, firewalls and IPS. These technologies simply do not work against polymorphic malware, which is used by nearly all of today’s advanced attacks. And yet RSA estimates that most organizations still spend about 80% of their security budgets on prevention technologies.
Damballa wanted to demonstrate the limitations of a prevention-centered approach to malicious software. They analyzed a sample set of tens-of-thousands of files sent to them by their customers. The files detected as malicious by their own Failsafe system were also scanned by the four most commonly deployed antivirus products. Here’s what they found:
- Within the first hour, the antivirus products missed nearly 70% of the malware
- After 24 hours, still only 66% of the files were identified as malicious
- At the seven-day mark, the accumulated total was 72%
- After one month, 93% of the files were identified as malicious
- More than six months passed before 100% of the malicious files were identified
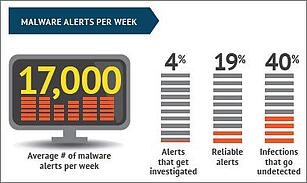
A 2015 Ponemon Institute report shows that the average enterprise gets 17,000 malware alerts weekly, or 2,430 daily, from IT security products. Based on the Damballa study you can do the easy math; antivirus products miss 796 malicious files on Day One.
And now combine the data from Damballa, RSA and Ponemon. You come to the shocking discovery that 80% of the security budget is spent on controls that are missing 796 malicious files a day.
 Many of these infections are caused by end-users who click on a malicious ad, click a bad link or open an infected attachment.
Many of these infections are caused by end-users who click on a malicious ad, click a bad link or open an infected attachment.
We all have limited budget and manpower. Nobody can afford to dedicate the majority their budget to failing controls. You need to defend your networks in depth, and get proactive instead of continuing to run around putting out fires. The Ponemon graph on the left shows the lost time caused by infected devices.
The very first step in getting proactive is deploying effective security awareness training combined with simulated phishing attacks. Prevention that really works is more important than ever, and end-user education gives you the best bang for your budget buck, but you also need to put greater emphasis on deeper defense-in-depth levels with detection and response. If you can reduce the time between the initial infection and its discovery and remediation, you reduce your risk of damage.
The first thing though would be to step your users through security awareness training combined with simulated phishing attacks to keep them on their toes with security top of mind. Find out how affordable this is for your organization today.
Hat Tip to Brian Foster, CTO, Damballa





