 Amazon is an obvious target for malicious actors looking to leverage the trust and authority enjoyed by a widely known online service or brand in malicious emails and social engineering schemes. And, unsurprisingly, customers using the Phish Alert Button (PAB) do indeed regularly report Amazon-themed phishing emails to us.
Amazon is an obvious target for malicious actors looking to leverage the trust and authority enjoyed by a widely known online service or brand in malicious emails and social engineering schemes. And, unsurprisingly, customers using the Phish Alert Button (PAB) do indeed regularly report Amazon-themed phishing emails to us.
The vast majority of these phishing emails spoof Amazon in order to target individual users and those users' own personal Amazon accounts. From fake password reset notifications to bogus emails regarding failed payments, spoofed Amazon phishes run the usual gamut of social engineering schemes designed to trick users into coughing up login credentials and credit cards.
There is, however, another lesser-known variety of Amazon-themed phishing emails that are occasionally reported to us. This sub-genre (for lack of a better term) of Amazon-themed phishing targets the Amazon AWS accounts of organizations (as opposed to the personal Amazon accounts of individual users).
AWS accounts are potentially attractive targets for bad actors as they could contain a wealth of exploitable data. Compromised AWS accounts could also be exploited by criminals who would have their own need for a robust, reliable cloud computing services platform. That such a platform might come free of charge only sweetens the pot.
Though we certainly aren't the first to have reported AWS-themed phishing attacks in the wild, we thought it would be useful to take a closer look at the range of social engineering schemes we've seen malicious actors using to worm their way into the AWS accounts of targeted organizations.
The Attack
This particular phishing attack is fairly basic. In fact, it's just a straight-up credentials phish -- a bread-and-butter attack for your average malicious actor. Nothing too complicated or exotic.
Take for example, one of the more recent AWS-themed phishes reported to us by customers using the Phish Alert Button (PAB).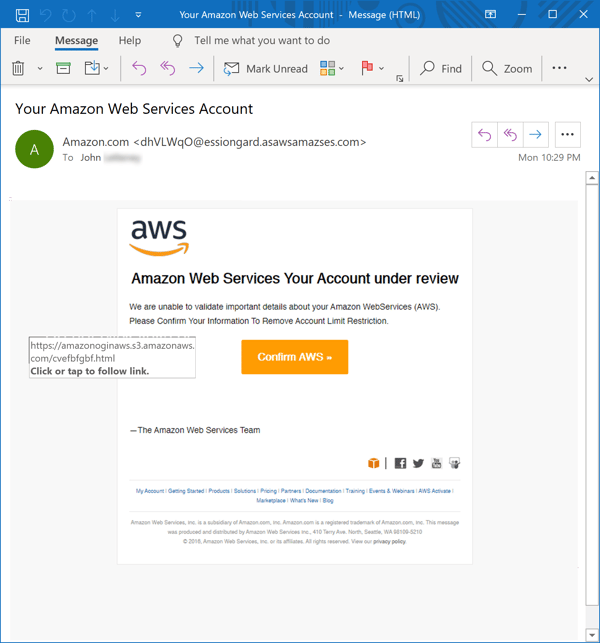
This is an exceptionally polished phishing email. The design is clean, simple, and spare -- just like actual email notifications users will be used to receiving from large online brands like Amazon, Microsoft, Netflix, or Paypal.
Moreover, the malicious actors behind this have also taken care to get the small details right -- the email footer for example, includes precisely the kind of data one would expect to find there. Even the domain used in the From: email address (asawsamazses.com) uses a cleverly convincing mish-mash of random letters, acronyms, and abbreviations to create a kind of "look-alike" domain or "domain doppelgänger."
The true genius, though, lies in using Amazon AWS itself for the "money link," which seamlessly redirects users through a file hosted on Amazon AWS to a landing page on the same domain used in the From: email address: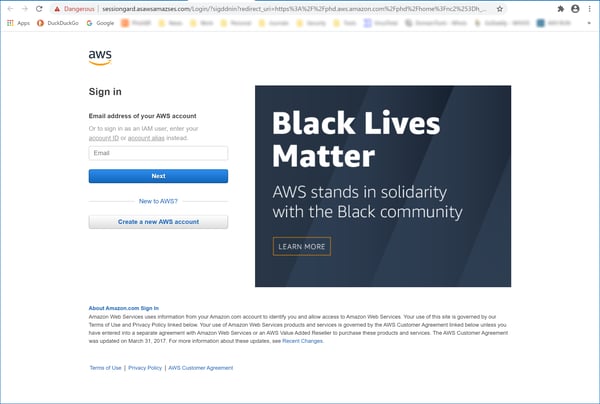
This spoofed AWS login page compares quite favorably with this actual Amazon AWS login page: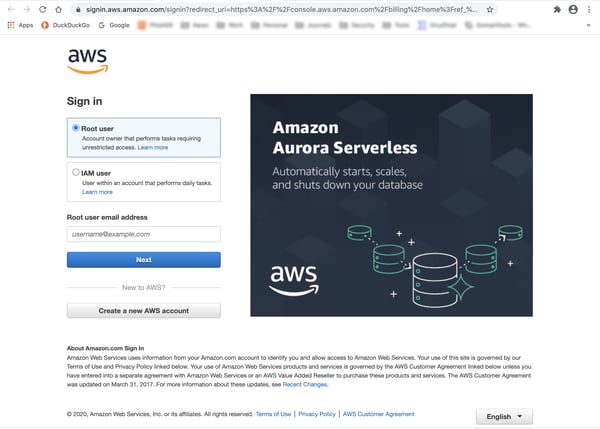
Somewhat cleverly, the bad guys have also taken care to preserve the ruse once they get the goods from hoodwinked users. Close inspection of the URL reveals that users will be redirected to Amazon itself once they finished coughing up their AWS login credentials -- all the better to ensure that victims remain none-the-wiser to the hack that was just perpetrated on them.
And, in a final stroke of irony, it appears that the bogus AWS domain was registered through Amazon's very own domain registrar the very day this phish was pushed out to users.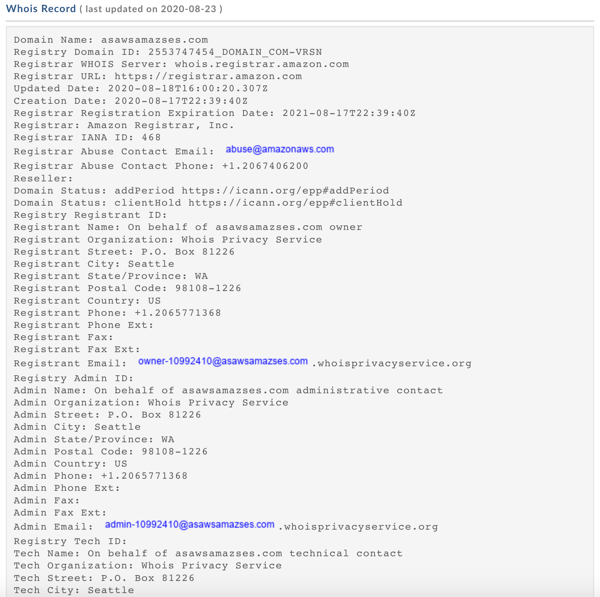
As one might expect, this particular phish lasted but a few days before the malicious files and bogus AWS domain were shut down on Amazon's servers.
Social Engineering 101
The social engineering hook used in the above email is one of the oldest and most basic schemes one typically finds in phishing emails. Users are informed -- often in the vaguest of terms -- there is a problem with one of their online accounts and are invited to log in to the account to address the issue. This is, in fact, the very same social engineering scheme used against potential marks over a decade ago (circa 2004-2005) in the earliest phishing attacks that spoofed large banks.
This fairly basic, no-frills social engineering scheme is perfectly suited to the task at hand. Indeed, the malicious actors behind these AWS-themed phishing attacks tend to stick to the familiar range of social engineering schemes widely used to spoof other online brands and services.
A billing issue with the targeted organization's AWS account is a popular ruse: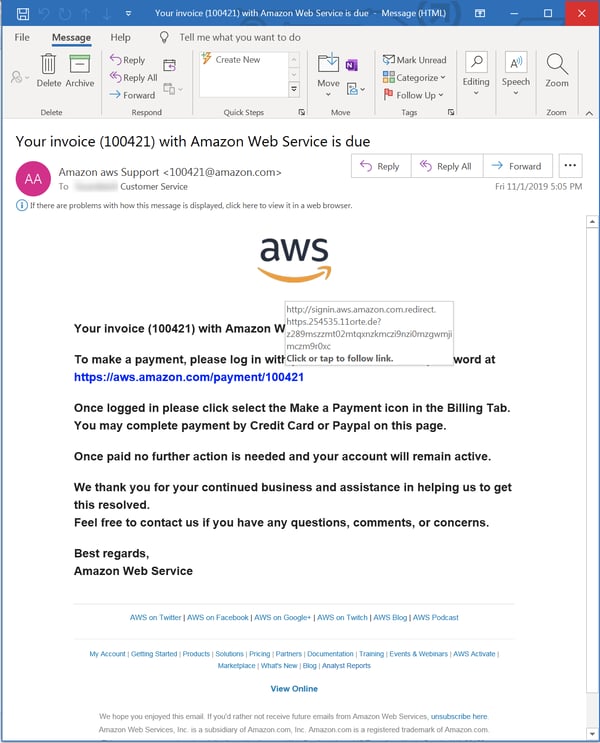
Fake messages and notifications from AWS are yet another go-to option for malicious actors on the hunt for AWS credentials: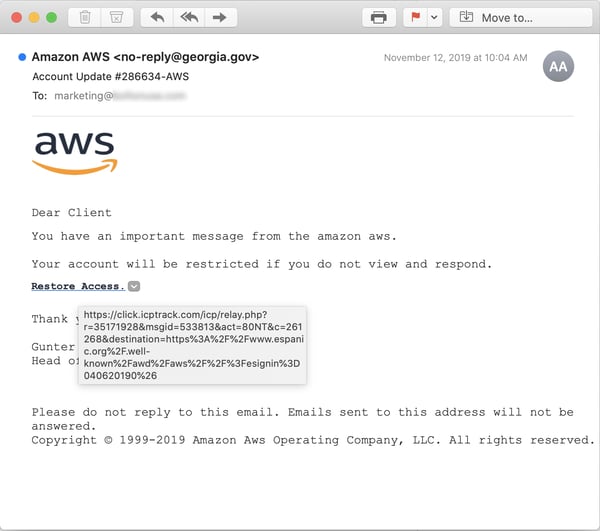
Also popular are fake security notices...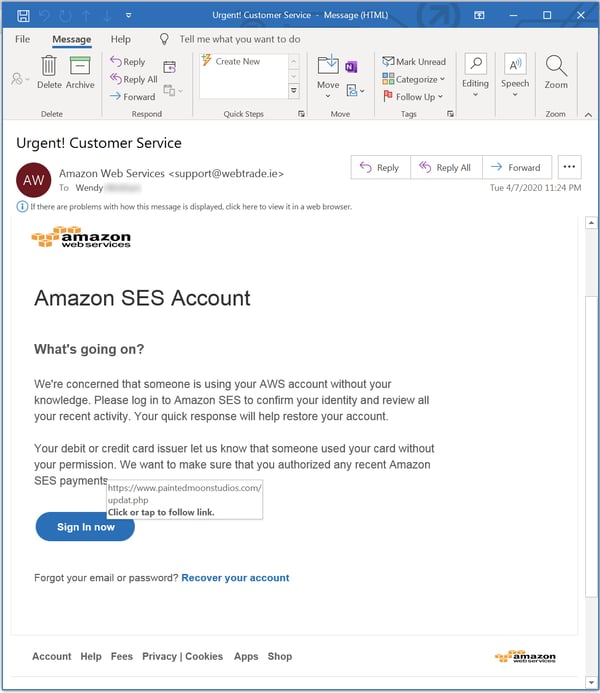
...fake AWS Support tickets...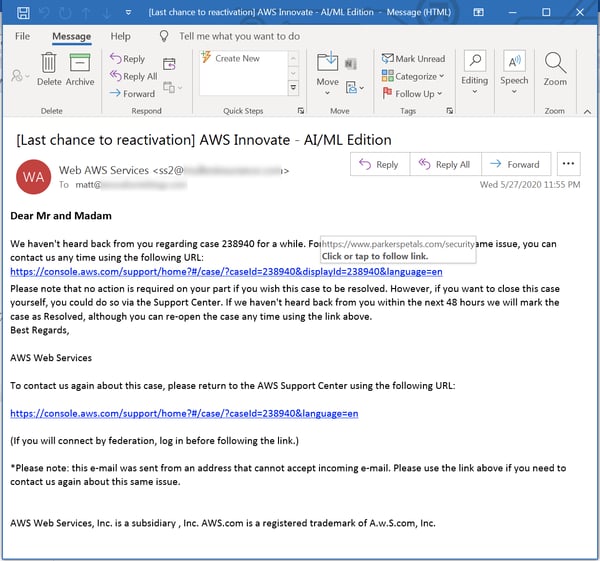
..and bogus business documents of one sort or another: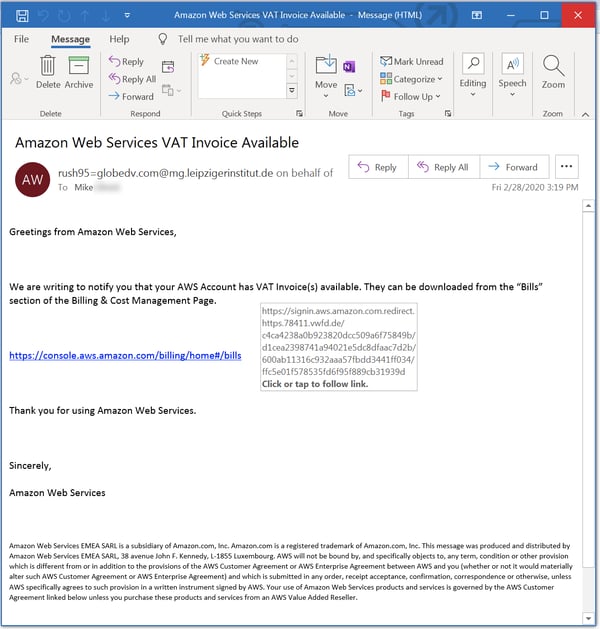
What we have here is almost a full menu of bread-and-butter social engineering schemes. If you were looking to explain to your employees what a typical phishing email might look like, you could do worse than to start with this batch of malicious emails.
While few are as carefully and cleverly constructed as the first example we looked at here, any one of these could work with users who are distracted, feeling rushed, or just not in the habit of handling external emails in a secure fashion.
The Bad News
Although the emails used to perpetrate this particular variety of phishing attack tend to be fairly basic, the potential impacts on a targeted organization are anything but simple and straightforward. Indeed, a compromised AWS account could prove uniquely devastating for an organization.
A compromised AWS account offers attackers a rich range of options for perpetrating fraud. Attackers in control of an organization's AWS account could potentially...
- harvest sensitive data from the account to be exploited in still further attacks against customers, partners, or clients
- demand ransom for the organization's data after it is exfiltrated from the account or after an organization is locked out of the account
- sabotage the organization's business by destroying or corrupting data stored in its AWS account (perhaps in connection with a ransom demand)
- skim money and financial data from accounts being used to support an online store or financial service
- use an organization's AWS account as a phishing platform, which could involve exploiting the account to distribute malware as well as host credentials phishing pages or other files used in phishing attacks
Of course, just what could be done with a compromised AWS account would be dependent on just what those accounts are being used for in the first place -- what data happens to be stored in the account, how the account is configured, and whether or not the account is being used for any public-or-customer-facing function.
AWS-themed phishing attacks are to be taken seriously -- at least as seriously as a standard credentials phish designed to give attackers carte blanche access to an organization's own network.
The Good News
Fortunately, based on the emails we've seen, the bad guys don't seem do a particularly good job hitting the individuals in an organization who might be in a place to manage an organization's AWS account as that account's root user.
The IT department would be the logical first choice for attackers, but there is no guarantee that the root user couldn't be some other employee in a completely different department within the organization -- again, depending on how a targeted organization is using the account.
Senior executives within an organization would also be logical targets for AWS-themed phishing emails -- if one were operating on the assumption that those individuals might forward AWS-related emails to the person who did have root user access. Then again, there are no guarantees that would happen.
In short, the bad guys seem to be having problems figuring out who the key individuals within organizations might be. As a result, the malicious actors behind these attacks appear to be shooting in the dark -- at least for now.
Given the real difficulties in targeting the right individual, this kind of phishing attack would probably be best pursued as a second stage operation -- that is, after an organization had already been breached and malicious actors had enjoyed some time to reconnoiter the network and get the lay of the land within an organization.
Conclusion
AWS-themed phishing emails are not nearly as common as many other varieties of phishing attacks designed to obtain login credentials from unwitting users. As we've seen in other instances, however, malicious actors have proven very adept at developing new attacks and learning from their failures. Bad actors are like Godzilla -- they just keep coming. We will, in short, see more of these AWS-themed phishing attacks. And they will get more sophisticated and more dangerous.
Your best defense at this point is get your users up-to-speed on all the latest social engineering schemes. That means stepping your users through New-school Security Awareness Training and testing them regularly with high-quality simulated phishes -- particularly those employees who control key resources in your organization like an AWS account. Now is the time to do that -- not after your organization's AWS account has fallen into the hands of malicious actors.
 Here's how it works:
Here's how it works:
