 700 Million LinkedIn user’s personal details were posted for sale earlier this month, putting 92% of their userbase at risk of social engineering and spear phishing attacks.
700 Million LinkedIn user’s personal details were posted for sale earlier this month, putting 92% of their userbase at risk of social engineering and spear phishing attacks.
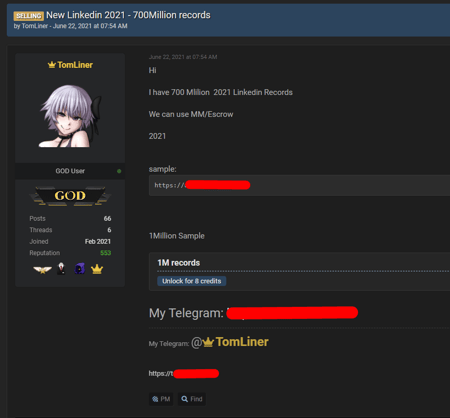
Hacker TomLiner put up a post last week on the dark web offering 700 Million LinkedIn records. Listed as a “GOD User”, no doubt TomLiner is active and well-known in that online community.
Source: LinkedIn
The data includes a number of details about each user, including:
- Email addresses
- Full names
- Phone numbers
- Physical addresses
- Geolocation records
- LinkedIn username and profile URL
- Personal and professional experience/background
- Genders
- Other social media account usernames
What makes this so dangerous is that this aids the spear phishing diligence the cybercriminals already do as part of Business Email Compromise attacks. In many ways, these details make the job easier. The more legitimate a BEC phishing email can be made to look legitimate using actual details, the more likely the scam will be successful.
According to LinkedIn, this isn’t technically a breach, since no private information was stolen. Instead, they claim it’s an aggregate of the 500 Million records stolen in April and other sites.
Even so, just knowing that cyber criminals can arm themselves with some impactful details familiar to the potential victim, you should be looking for ways to empower users to know when they’re being targeted. Security Awareness Training is one of the most effective ways, as it opens the user’s eyes to how the bad guys try to trick them, teaching them to be vigilant – even when emails appear legitimate.
 Here's how the Social Media Phishing Test works:
Here's how the Social Media Phishing Test works:




