
Almost two years ago we took note of two different write-ups on the Adwind (aka AlienSpy) remote access trojan (RAT), one by McAfee and the other by Fidelis Security. Those pieces caught our eye not only because they were published so close together but because one particular Adwind variant, Jsocket, had popped on our own radar following the release of the Phish Alert Button (PAB), which enabled our customers' employees to report suspected phishing emails directly to us (as well as their own IT departments) from within Outlook. Then, as now, ransomware dominated the attention of the security industry, understandably so. But the persistence of Adwind, a cross-platform malware-as-a-service offering that has been around since at least 2012, in the phishing emails reported to us by customers made us sit up and take notice.
As we noted at the time...
Anti-virus coverage of the JSocket variants we've seen ranges from spotty at best (5 or 6 out of 50 plus anti-virus scanners on VirusTotal) to almost non-existent. Because JSocket boasts advanced features that allow it to shut down and defeat anti-malware applications, any anti-virus on a box compromised with JSocket will likely be taken out of action, leaving external, malicious actors with complete control of a machine inside the network.
Although Jsocket and other Adwind variants never really disappeared over the intervening two years, we were nonetheless surprised to see what appeared to be a significant resurgence in Adwind-infested phishing emails starting early to mid-October of this year. Intrigued, we decided to take a closer look. What, if anything, had changed with Adwind? Were endpoint anti-virus applications enjoying any greater success in dealing with Adwind? And, finally, had the bad guys made any changes to social engineering schemes deployed in the phishing emails they used to distribute Adwind to unsuspecting, gullible corporate users?
What we found was disappointing -- but not especially surprising.
A RAT's Second Wind
In early October we noticed an uptick in the number of phishing emails reported by customers that were sporting .JAR (Java) attachments -- a hallmark of Adwind/AlienSpy. Occasional upticks in certain threats are nothing remarkable as various malware gangs experiment with new phishing campaigns, changing up their usual menu to temporarily begin pushing different types of malware. By mid-October it had become apparent that this minor uptick had taken on legs, with an ever increasing number of poisonous emails being forwarded to us by customers.
Based on what we already knew about Adwind its several variants like Jsocket, we knew this resurgence in .JAR file attachments was almost certainly a sign that one or more malicious actors was making a concerted effort to seed corporate endpoints with what is perhaps the most dangerous backdoor trojan in the wild. And given that Adwind and its several variants are distributed to malicious actors through a subscription-based malware-as-a-service model, we didn't discount the possibility that we could be looking at a collection of bad guys all pushing Adwind variants at the same time.
While the Adwind phishing emails we encountered from Phish Alert Button (PAB) users sported a diverse number of Subject: lines and corresponding social engineering hooks, there was an underlying consistency that we observed. All the Adwind phishes in this upsurge used Subject: lines and social engineering schemes centered on everyday business documents and related forms: invoices, purchase orders, payment instructions, contracts, and RFQs (requests for quotations). Such social engineering schemes are designed to look innocuous and fly under the radar of most denizens of corporate offices, luring them into reflexive clicks on malicious emails that look little different from the usual fare that populates their inboxes. Some example Subject: lines...
- Attached revised Price Inquiry
- BALANCE PAYMENT
- BALANCE PAYMENT AND SWIFT COPY
- Confirmation transfer
- Payment advice (21 Oct 2017)
- For your information (A)
- Outgoing SWIFT Message 47C9C13970FF.txt
- Payment advice (21 Oct 2017)
- Payment Advice - Advice Ref:[G41391375839] / ACH credits/Customer Ref:[GIRO PAYMENT-CREDITORS] / Second Party Ref:[H60]
- payment copy 10/23/2017
- Proforma
- Purchase Order
- REQUEST FOR QUOTATION
- Request For Quotation/ Top Urgent
- Request For Quotation/ Urgent Supply SYNERGY BQ155
- RFQ MJEPL/MB-4638/2017
- SALES CONTRACT DOCUMENT
- Swift_MT103576587_PDF
- URGENT ORDER
Note the haphazard, slightly sloppy nature of these Subject: lines, which are designed to mimic the cold, inconsistent appearance of so many business emails.
Also of note is the fact that such social engineering hooks -- focused as they are on finance-related business documents -- are clearly targeted at employees working in finance and accounting departments. This is no accident.
Adwind and its several variants are designed primarily to surreptitiously collect and securely exfiltrate data from compromised boxes, including emails, files, credentials, and virtually anything else that can be vacuumed up via the malware's embedded keystroke logger, remote desktop module, and eavesdropping components that provide access to the PC's camera and microphone. The PCs of employees working in finance and accounting are highly likely to contain sensitive and extremely valuable data that could provide malicious actors access to the most sensitive accounts within an organization, including those that control financial resources, to say nothing of the treasure trove of customer and client data that could be used to bootstrap attacks on still more vulnerable organizations.
The Subject: lines we observed were remarkably similar to those reported by McAfee two years ago:
- Re: Payment/TR COPY-Urgent
- credit note for outstanding payment of Invoice
- Fwd: //Top Urgent// COPY DOCS
- Re:Re: Re:Re:Re TT copy & PIs with Amendments very urgent...
- PO#939423
- Western Union Transaction
Even the nature of the attached file names was remarkably consistent. Some examples from this October:
- 0.58713700 1508714104.jpg.jar
- BALANCE PAYMENT.jar
- Confirmation 0.003.jar
- contract.jar
- IMG_1508605445.jar
- order corfirmation.jar
- PAYMENT AND SWIFT COPY.jar
- payment copy.jar
- PO.jar
- PO_COPY#908790.jar
- Proforma#.84242300.jar
- Qlty request 40012300_png.pdf.jar
- Quote #100-231017.jar
- Revised Price List 738584752985.jar
- Scan_list29017.jar
- Swift_MT103576587_PDF.jar
- SYNERGY BQ155.jar
- Transfer Confirmation.jar
Compare with the file names reported by McAfee two years ago:
- Shipment_copies (2).jar
- FUD FIle.jar
- PO 8324979(1).jar
- Shipping Documents.jar
- Telex Copy.jar
- INSTRUCTIONCZ121.jar
- Order939423.jar
- Payment TT COPY.jar
- SCAN_DRAFT COPY BL,PL,CI.jar
- Enquiries&Sample Catalog CME-Trade.jar
- Transaction reciept for reconfirmation.xslx.jar
- P-ORD-C-10156-124658.jar
- Proforma Invoice...jar
- TT APPLICATION COPY FORM.jar
- Dec..PO.jar
- Credit_Status_0964093_docx.jar
The bad guys may have developed new templates for their phishing emails in the intervening two years, but the basic approach to crafting effective social engineering hooks has remained the same.
As one might expect, the email bodies for these Adwind phishes are short and to the point, giving users little indication that something might be amiss:
1.png?width=640&name=Paymentadvice(21Oct2017)1.png)
One might be encouraged at the fact that Outlook denies access to attachments it deems inherently unsafe (such as .JAR files), but this protection is easily circumvented:
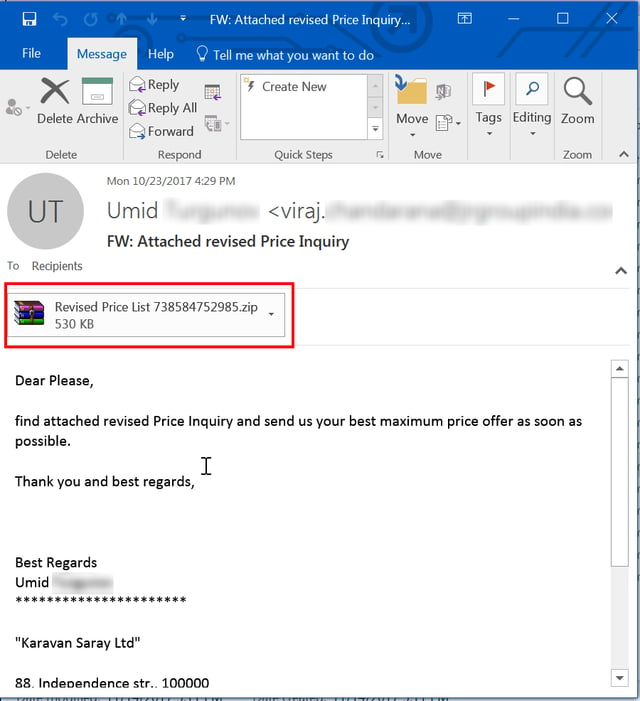
Meet the New RAT, Same as the Old RAT
By all appearances the Adwind remote access trojan remains a potent, dangerous foe, having been continuously developed for commercial offering since at least 2012. The Adwind variants we encountered two years ago ranged from 120 kb to 200 kb in size. The most recent batch of Adwind .JARs ranges from 500-600 kb in size, with most coming in around 550 kb.
Adwind also retains a daunting collection of advanced functionality, including...
- Sandbox detection
- Detection, disabling and killing of various antivirus and security tools
- TLS protected command-and-control
- anti-reverse engineering/debugging protection
..as well as a wide array of data gathering features:
- Collection of System Information (e.g. IP, OS version, memory RAM information, Java version, Computer Name, etc.)
- Upload & Execute additional malware
- Capture Webcam and Microphone without user notification
- Remote Desktop to watch user activity
- File Manager to allow access to files in the context of the current user
- Browser Password theft
- Keylogging to capture passwords otherwise obscured from viewing
Of particular interest to us, however, was how well endpoint anti-virus engines might handle these latest Adwind variants. When we looked at one particular Jsocket variant two years ago, we noted that anti-virus coverage (as measured via VirusTotal) was "spotty" at best, with typically only 5-6 engines detecting the samples we submitted. Although we can say that anti-virus engine detections appear to have improved with time, they are still not at a level that would inspire confidence, with the samples we submitted being picked up by only 16-24 engines (out of 60 total) -- roughly 26%-40% of tested engines -- even weeks after their original appearance in the wild.
It is worth noting that most endpoint anti-virus products now incorporate heuristics-driven behavioral detection capabilities that allow them to provide protection beyond their more traditional, file-focused core engines. Many of these behavioral protection schemes intervene only after malicious files land on the file system and execute, however. And given that Adwind itself sports extremely aggressive tools to detect, thwart, and kill all manner of security tools, the best approach to handling an advanced threat like Adwind is to prevent it from being downloaded and executed in the first place.
Whither Adwind?
As we began writing this blog piece, the Adwind resurgence we first noted in early October showed no signs of letting up. This phishing campaign is particularly alarming inasmuch as it indicates that one or more malicious actors is actively deploying malware designed to support a sustained presence inside corporate networks. And those malicious actors still enjoy a wealth of opportunities to exploit inasmuch as Java remains a popular tool inside business organizations, even two decades after its original release and years of mounting reports of security problems stemming from its continued use.
While most ransomware campaigns can be likened to one-time smash-and-grab operations intended to muscle vulnerable organizations into coughing up money in return for their data, Adwind campaigns are prosecuted by individuals and groups more interested in playing a longer game in which they breach boxes, set up shop, and then exploit those beachheads inside corporate networks over an extended period of time by "living off the land" -- which is to say, leveraging the data they obtain on the box to enable still further mayhem against targeted organizations as well as their clients, partners, and customers. Indeed, the very email templates used in Adwind phishing campaigns give every sign of having been harvested from the inboxes of previous victims.
Although anti-virus endpoints appear to have made some progress in improving detections of Adwind and variants like Jsocket, detections of Adwind by core anti-virus engines remains sub-par. And given that there are already thousands of variants and sub-variants of Adwind being distributed by hundreds of malicious actors who ponied up for subscriptions to this malware-as-a-service, no organization should be relying exclusively on standard endpoint anti-malware protection to prevent these malicious actors from pitching a digital tent on their employees' PCs.
As we noted above, the best approach to handling the threat posed by Adwind is to prevent its malicious .JAR files from be downloaded and executed at all. And one critical tool in that effort should be New-school Security Awareness Training, which teaches your employees how to spot potentially malicious emails and avoid being tricked into clicking through, then tests those employees on a regular basis to keep their security awareness sharp and provide you with a concrete measure of your own organization's human vulnerabilities.




