 Monday night, researchers at Proofpoint sounded the alarm about a critical 0-day threat known as CVE-2017-0199 in Microsoft Word that allowed booby-trapped Dridex phishing attacks be sent to millions of employees claiming to be a PDF sent to them by their company photocopier.
Monday night, researchers at Proofpoint sounded the alarm about a critical 0-day threat known as CVE-2017-0199 in Microsoft Word that allowed booby-trapped Dridex phishing attacks be sent to millions of employees claiming to be a PDF sent to them by their company photocopier.
This one is particularly bad because it bypasses exploit mitigations built into Windows, doesn't require your employee to enable macros, works even against Windows 10 which is Redmond's most secure OS yet, and this exploit works on most or all Windows versions of Word. Ouch!
The Russian Dridex banking trojan mafia is notorious for being the most prominent banking malware, and moved into ransomware last year with the Locky strain.
Campaign Uses Spoofed Email Domains
Dridex used to rely on macro-infected documents attached to emails and use social engineering to trick the user to open the attachment and click the macro button. This time around they were pretty nimble and leveraged a zero-day in Word. Proofpoint's technical analysis said:
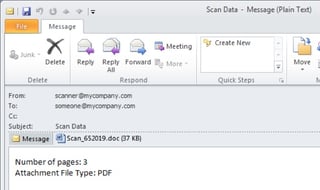
"Emails in this campaign used an attached Microsoft Word RTF (Rich Text Format) document. Messages purported to be from "". [device] may be "copier", "documents", "noreply", "no-reply", or "scanner". The subject line in all cases read "Scan Data" and included attachments named "Scan_123456.doc" or "Scan_123456.pdf", where "123456" was replaced with random digits. Note that while this campaign does not rely on sophisticated social engineering, the spoofed email domains and common practice of emailing digitized versions of documents make the lures fairly convincing.
What To Do About It
1) Fortunately, on Tuesday Microsoft released its regular batch of security patches - including a fix for this nasty Office zero-day vulnerability CVE-2017-0199. Turns out that this wasn't the only thing needed patching. An elevation of privilege vulnerability in Internet Explorer (CVE-2017-0210) that would allow an attacker to convince a user to visit a compromised website was also fixed.
2) In case for some reason you cannot apply the patch (and there are plenty) here is a quick and dirty fix to prevent this exploit from working by adding the following to your Windows registry: Software\Microsoft\Office\15.0\Word\Security\FileBlock\RtfFiles to 2 and OpenInProtectedView to 0.

Also, EVERYONE in the US/Canada will receive a real Kevin Mitnick collectible stainless steel lock-pick business card!
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc





