 Motherboard reported: "A quickly-spreading, world-wide ransomware outbreak has reportedly hit targets in Spain, France, Ukraine, Russia, and other countries. This strain is deadlier than WannaCry and has infected large banks, law firms, shipping companies, and even nuclear facility Chernobyl. This post is continually updated at the bottom when more news becomes available.
Motherboard reported: "A quickly-spreading, world-wide ransomware outbreak has reportedly hit targets in Spain, France, Ukraine, Russia, and other countries. This strain is deadlier than WannaCry and has infected large banks, law firms, shipping companies, and even nuclear facility Chernobyl. This post is continually updated at the bottom when more news becomes available.
"We are seeing several thousands of infection attempts at the moment, comparable in size to Wannacry's first hours," Costin Raiu, a security researcher at Kaspersky Lab, told Motherboard in an online chat.
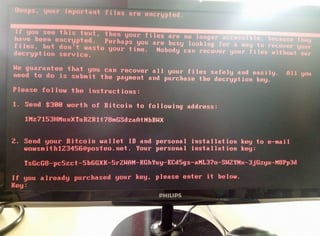
Judging by photos posted to Twitter and images provided by sources, many of the alleged attacks involved a piece of ransomware that displays red text on a black background, and demands $300 worth of bitcoin.
"If you see this text, then your files are no longer accessible, because they are encrypted," the text reads, according to one of the photos. "Perhaps you are busy looking for a way to recover your files, but don't waste your time. Nobody can recover your files without our decryption service."
Raiu believes the ransomware strain is known as Petya or Petrwrap, a highly sophisticated Russian strain, without all the errors that WannaCry contained, and no kill-switch. According to a tweet from anti-virus company Avira, the Petya attacks were taking advantage of the EternalBlue exploit previously leaked by the group known as The Shadow Brokers
EternalBlue is the same exploit used in the WannaCry attacks; it takes advantage of a vulnerability in the SMB data-transfer protocol, and Microsoft has since patched the issue. However, whether customers apply that patch is another matter.
Security researchers from Kaspersky Lab reported that the ransomware hit Russia, Ukraine, Spain, France, among others. Several people on Twitter reported witnessing or hearing reports of the outbreak in their respective countries, and across a wide range of industries. Companies around the world also reported computer outages.
If You Have Not Done So Yet, Apply This Patch Immediately.
From what we have been able to learn, this new worm spreads through SMB just like WannaCry so when we're talking about machines behind firewalls being impacted, it implies port 445 being open and at-risk hosts listening to inbound connections. It'd only take one machine behind the firewall to become infected to then put all other workstations and servers at risk due to it being a true worm.
In the meantime, harden yourselves against this Windows Network Share vulnerability and ensure that all systems are fully patched with the "MS17-010" security update (link below) and remind all staff to Think Before They Click when they receive any out of the ordinary emails. https://technet.microsoft.com/
Note, the patch is included in the Monthly Quality rollups. Also, block inbound connections on TCP Port 445
[UPDATE 6/27/2017] 1:40pm
"It is definitely using EternalBlue to spread," says Fabian Wosar, a security researcher at the defense firm Emsisoft, which specializes in malware and ransomware. "I confirm, this is a WannaCry situation," Matthieu Suiche, the founder of security firm Comae Technologies, wrote on Twitter.
Group-IB believes the attacks on Ukraine and Rosneft were simultaneous and coordinated. Kaspersky and Flashpoint think they're observing signs of the Petya (a.k.a. Petrwrap) strain of ransomware in the attacks.
Other major infestations are reported by the Danish shipping concern A.P. Moller-Maersk, pharmaceutical company Merck (this in the US), Deutsche Post (its operations in Ukraine), and British ad agency WPP. More are sure to come.
The ransom note's text has appeared in English, but Ukrainian authorities blame Russian hackers, especially since the attack coincides with tomorrow's observance in Ukraine of Constitution Day. On this interpretation the attack's spread is due either to the inherently difficult-to-control nature of malware, deliberate misdirection, or willingness to take such targets of opportunity as present themselves.
[UPDATE 6/27/2017] 2:13pm
Delivery/Exploitation
We have not yet confirmed the initial infection vector for this new Petya variant. Previous variants were spread through e-mail, but we have not identified this latest sample carried in any e-mail related attacks.
Installation
This variant of Petya is spread as a DLL file, which must be executed by another process before it takes action on the system. Once executed, it overwrites the Master Boot Record and creates a scheduled task to reboot the system. Once the system reboots, the malware displays a ransom note which demands a payment of $300 in bitcoin.
Command and Control
Petya contains no Command and Control mechanisms that we know of. After a host is infected, there is no communication from the malware back to the attacker.
Lateral Movement
Petya may spread to other hosts directly using SMB or through the ETERNALBLUE exploitation tool.
[UPDATE 6/27/2017] 3:38PM
Though widely reported to be a variant of the Petya ransomware, there is disagreement among researchers as to whether it is actually Petya or something with a similar design.
The ransomware appears to be spreading quickly. Dave Kennedy of security consulting firm TrustedSec wrote on Twitter that he observed more than 5,000 infections in a 10-minute period.
The antivirus firm BitDefender, claims that it is "almost identical" to a recent offshoot of Petya named GoldenEye that built of of Petya and other sources. Other researchers have backed that claim. The ransomware, reports Bitdefender, encrypts both files and Master File Table.
Both BitDefender and Kaspersky agree that the ransomware uses multiple infection mechanisms, including the same one that fueled the WannaCry outbreak, known as EternalBlue.
Ryan Naraine, a researcher with Kaspersky Lab identified three different vectors the malware uses to attack. EternalBlue, a vulnerability in accounting software mandated throughout Ukraine, and a second vulnerability in the Windows file-sharing process exploited by EternalBlue. Let's hope it is not using DoublePulsar, which is another NSA Cyberweapon which compriomises the windows kernel.
On Twitter, Mikko Hypponen, the chief research officer of the antivirus firm F-Secure, identified more than 60 file types that Petya ransomware directly encrypts, including Microsoft office files, PDFs, compressed files and source code. The SANS InternetStorm Center posted a preliminary summary.
[UPDATE 6/27/2017] 5:21PM
To capture credentials for spreading, the strain uses custom tools like Mimikatz. These extract credentials from the lsass.exe process. After they have been extracted, the creds are passed on to PSExec tools (which is meant to carry out limited actions on other systems, but in this case its spreading the infection by executing malicious code on other computers) or WMIC for distribution inside your network. The email account associated with the bitcoin ransom demand ($300) has since been disabled so decryption keys are pretty much out of the question now.
ESET researcher Robert Lipovsky said. "It only takes one unpatched computer to get inside the network, and the malware can get administrator rights and spread to other computers." Perhaps most crucially, thanks to all these added features, the new strain will infect even patched Windows PCs, including those with Windows 10, as one IT professional noted in a blog,
[UPDATE 6/27/2017] 7:09PM
Uh Oh. “Petya is different [than WannaCry] and could be much worse,” said Morey Haber, vice president of technology at BeyondTrust.”The main takeaway is that WannaCry only had one method to propagate. If a resource was patched, SMB was not exposed to the internet, or the user was running a modern OS (like) Windows 10, the ransomware threat was mitigated. Petya builds on top of this by initially deploying in mass via email and it only takes one system to begin the infection.”
Nicholas Weaver, a security researcher at the International Computer Science Institute and a lecturer at UC Berkeley, said Petya appears to have been well engineered to be destructive while masquerading as a ransomware strain. “I’m willing to say with at least moderate confidence that this was a deliberate, malicious, destructive attack or perhaps a test disguised as ransomware,” Weaver said. “The best way to put it is that Petya’s payment infrastructure is a fecal theater.”
Russian security firm Group-IB reports that Petya bundles a tool called “LSADump,” which can gather passwords and credential data from Windows computers and domain controllers on the network.
[UPDATE 6/27/2017] 8:38PM
A troubling aspect is how Petya got into the computers in the first place. According to research by Talos Intelligence, the ransomware may have spread through a falsified update to a Ukranian accounting system called MeDoc. MeDoc has denied the allegations, but a number of other groups have concurred with Talos’s finding, pointing to what appears to be a forged digital signature in the payload. If that signature was effective, it would have given attackers a clean way into almost any system running the software.
[UPDATE 6/28/2017] 6:15AM
The source looks to be a software update to Ukranian accounting company Intellekt Servis' product. Their June 22 update was pusged out and looks to have contained sleeper code that kicked in one day before Ukraine's Constitution Day. The WSJ said:"
The cyber security department of Ukraine’s national police warned on its Facebook page that preliminary analysis suggested the accounting software was “only one of the vectors of the attack.” The Russian security firm Group-IB agreed, saying it saw companies infected via malicious email attachments.
Many victims of the ransomware were told to pay a $300 ransom demand in the digital currency bitcoin. Still, others saw not only financial but political motivations behind the attack, which struck the day before Constitution Day, a Ukrainian national holiday.
“I think not only is it out there trying to make a profit, but it’s also making a very clear political statement: it’s intentionally trying to damage businesses that interact with the Ukrainian tax system, “ Mr. Williams said.
This morning the WSJ wrote: " The cyber security department of Ukraine’s national police warned on its Facebook page that preliminary analysis suggested the accounting software was “only one of the vectors of the attack.” The Russian security firm Group-IB agreed, saying it saw companies infected via malicious email attachments.
Many victims of the ransomware were told to pay a $300 ransom demand in the digital currency bitcoin. Still, others saw not only financial but political motivations behind the attack, which struck the day before Constitution Day, a Ukrainian national holiday.
Craig Williams, security outreach manager with Cisco Systems Inc said: “I think not only is it out there trying to make a profit, but it’s also making a very clear political statement: it’s intentionally trying to damage businesses that interact with the Ukrainian tax system.“
[UPDATE 6/28/2017] 6:30AM - I am calling it, this was done by the GRU.
 We are dealing with cyber warfare here.
We are dealing with cyber warfare here.
The Ukraine is locked in a bitter proxy fight with Russia since the annex of the Crimean peninsula and the separatist war in eastern Ukraine. Russia's GRU, the foreign military intelligence agency of the General Staff of the Armed Forces of the Russian Federation is likely behind this. The official full name is Main Intelligence Agency of the General Staff of the Russian Armed Forces. The GRU is Russia's largest foreign intelligence agency. In 1997 it deployed six times as many agents in foreign countries as the SVR, the successor of the KGB's foreign operations directorate. It also commanded 25,000 Spetsnaz troops in 1997. Source: WikiPedia
The GRU has its own cyber armies and works together with sophisticated hacker groups like APT28 which also goes by Fancy Bear. These are typically the guys behind attacks like this, however, this particular infection is a new low, because it's main goal is destructive, masked as a ransomware attack.
[UPDATE 6/28/2017] 11:460AM - Here is a possible decryptor
Got hit with this? Trying to pay is futile. This is a Petya decryptor and password generator that worked for the original Patya infection. Hopefully it will still work for this new one...
[UPDATE 6/28/2017] 17:06PM - Nope, it's destructive
That’s the idea advanced by several experts as more facts about the software come to light. Comae’s Matt Suiche and others compared the code in this week’s Petya attack with a similar attack from last year. 2017 Petya appears to have been modified specifically to make the encoding of user data irreversible by overwriting the master boot record. The attackers’ email address also appears to have been taken offline, preventing ransoms from being paid. This is not ransomware, this is a WIPER like Shamoon.
[UPDATE 6/28/2017] 7:44PM - Here is a vaccine
Vaccine, not Killswitch, Found for Petya (NotPetya) Ransomware Outbreak. Cybereason security researcher Amit Serper has found a way to prevent the Petya (NotPetya/SortaPetya/Petna) ransomware from infecting computers.
Free Ransomware Simulator Tool
How vulnerable is your network against a ransomware attack?
Bad guys are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 infection scenarios and show you if a workstation is vulnerable to infection.





