 I was alerted by a customer about a really difficult scenario that’s becoming all the more frequent. While there’s probably little that can be done in terms of tuning your spam filters and endpoint security tools, new-school security awareness training can make a difference. Here is the story:
I was alerted by a customer about a really difficult scenario that’s becoming all the more frequent. While there’s probably little that can be done in terms of tuning your spam filters and endpoint security tools, new-school security awareness training can make a difference. Here is the story:
"Over the past few months, we have been hit with increasing frequency with an attack that follows this 5-step pattern;
- A known vendor or customer falls victim to a phishing attack. Their email credentials are compromised, and the “bad guy” gets access to their email account.
- They start by changing the password, so that the victim no longer has control.
- They then comb through past email correspondence, and using the victim’s account, signature, and logo, send out targeted emails crafted to closely resemble legit correspondence they have had with our company in the past.
- Depending on the “bad guy’s” dedication to his craft, these could be fairly generic, or extremely specific. We’ve received one with an inquiry that referenced a specific real invoice # for that individual.
- The email always includes a spreadsheet or PDF. The name can be generic, or can be really specific. We’ve received one titled with a specific real invoice # for that individual.
Because these emails are coming from a real email account for a real business partner, they are really hard to detect, and in some cases they are literally impossible to detect, as they are carefully crafted copies of past legitimate emails. Naturally, there are a few that cast a wide net, so they are more generic and often contain corrupted grammar or spelling, but others are indistinguishable from real emails."
What To Do About This Threat
Granted, this is a a frustrating and dangerous situation, as the majority of the red flags users have been trained to watch for simply aren’t present if the scammer uses a highly targeted approach like this.
However, there is one cardinal rule that you need to stress with your users to protect against a scenario like this: DID THEY ASK FOR THE ATTACHMENT?
If they did not, it's a very good idea to double check using an out-of-band channel like the phone to call and ask if they sent this and why it was sent before the attachment is opened. There is little else that can be done. Yes, that is a little more work. But also, better safe than sorry.

We've got something really cool for you: the new Phishing Security Test v3.0!
Sending simulated phishing emails is a fun and an effective cybersecurity best practice to patch your last line of defense… your users.
Find out the Phish-prone percentage™ of your organization with our free updated Phishing Security Test that now includes our New Industry Benchmarking. See where you stack up! Industry Benchmarking enables you to compare your organization’s Phish-prone percentage with others in your industry.
Find out how you are doing compared to your peers and see the difference 12 months can make after using the integrated KnowBe4 Simulated Phishing and Security Awareness Training platform!
With Our Updated Phishing Security Test: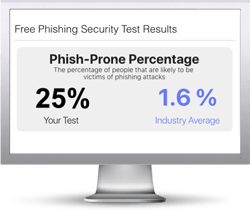
- You can customize the phishing test based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Start phishing your users now. Fill out the form, and get started immediately. There is no cost.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





