 As Phishing as a Service (PhaaS) kits continue to evolve, news like recent attacks using the Greatness toolkit demonstrate how easy it is for novice attackers to access accounts despite multi-factor authentication (MFA) being enabled.
As Phishing as a Service (PhaaS) kits continue to evolve, news like recent attacks using the Greatness toolkit demonstrate how easy it is for novice attackers to access accounts despite multi-factor authentication (MFA) being enabled.
We’ve seen plenty of adversary-in-the-middle (AiTM) attacks over the years, where the threat actor inserts themselves (in one form or another) into an existing communication, impersonating one of the parties in the communication. But new PhaaS kits, including one dubbed Greatness, has Microsoft Threat Intelligence sounding the alarm about the improvements these kits make in AiTM attacks.
According to coverage of these attacks over at hackernews.com, these new PhaaS kits allow attackers to conduct “high-volume phishing campaigns” with ease. What makes these kits so dangerous is their use of new techniques in credential harvesting attacks to bypass MFA protections using one of two methods:
- Proxy servers – when the victim user it presented with an impersonated logon page for a platform like Microsoft 365, the credentials presented are proxied over to the legitimate site and, should MFA be required, the MFA screen is proxied back to the user to provide the needed authentication code.
- Synchronous relay servers – In this model, the PhaaS kit is split into two parts; a phishing kit server (that is responsible for presenting the impersonated site to and interact with the user) and a PhaaS synchronous relay server (that does the work of handling the legitimate authentication with the target platform).
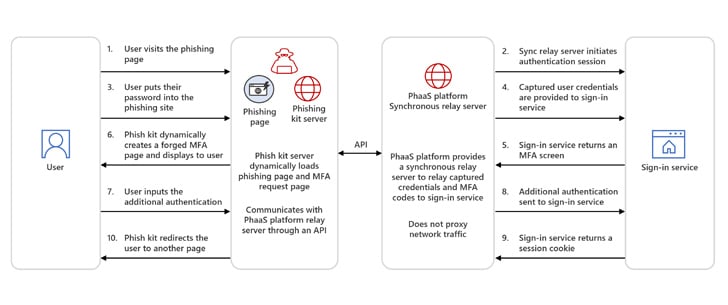
In either case, the end result is victims do all the work, providing the needed credentials and secondary forms of authentication, with the PhaaS kits passing these details to the target system and gaining access to the user’s account.
The key here (as with all phishing attacks) is that the user *must* interact with the attack; if the user is vigilant enough – something established through continual security awareness training – they will see the social engineering used in the initial email for the scam it is and never engage this effective AiTM attack.
 Here's what you'll get:
Here's what you'll get:




