 The latest attack from the Russian GRU involves both traditional spear phishing and close access attacks in an attempt to thwart an investigation of the nerve agent attack in the UK.
The latest attack from the Russian GRU involves both traditional spear phishing and close access attacks in an attempt to thwart an investigation of the nerve agent attack in the UK.
The nerve agent attack purportedly involved Russia’s military intelligence agency GRU wanting to dispose of a UK-based Russian spy and his daughter. The organization responsible for investigating the attack – the Organization for the Prohibition of Chemical Weapons (OPCW) – came under two attacks.
Officials say that four Russian GRU officers tried a Close Attack – where they attempted to hack into the OPCW network through its Wi-Fi network by parking a car close to the organization’s headquarters looking for unsecured devices on the network that could be compromised to gain access. This attack technique allows attackers to obfuscate who they are by originating the attack on the organization’s own network.
When that failed, the GRU reportedly followed up with a spear phishing attack impersonating Swiss federal authorities to target OPCW employees directly in order to access OPCW computer systems.
It’s easy to dismiss stories like this, as the criminals in this case were government-sponsored attackers. You don’t think of your organization as a target for these kinds of attacks. But, it’s important to keep in mind that cybercriminals use these very same tactics. The Close Access attack is less likely, as cybercriminals tend to want to remain in hiding, attacking from afar – but the intent to access your network to gain control over systems, applications, and data is relatively consistent across attacks.
Stopping Close Access attacks require shoring up Wi-Fi security that includes requiring authentication. Protecting against Spear phishing attacks involves a layered security approach that includes email scanning, endpoint-based protection, and Security Awareness Training to educate users on common social engineering tactics and scam methods used.
Do your users know what to do when they receive a suspicious email on their mobile device?
Should they call the help desk, or forward it? Should they forward to IT including all headers? Delete and not report it, forfeiting a possible early warning?
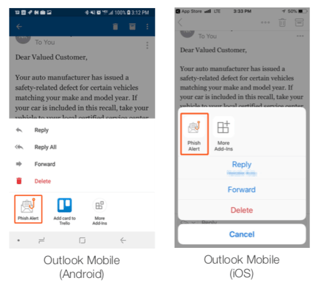
KnowBe4’s FREE Phish Alert button now also works with Outlook Mobile for iOS and Android. This enables your users to report suspicious emails from not only their computer but from their mobile inbox as well.
The Phish Alert Button gives your users a safe way to forward email threats to the security team for analysis and deletes the email from the user's inbox to prevent future exposure. All with just one click!
Best of all, there is no charge!
- Reinforces your organization's security culture
- Incident Response gets early phishing alerts from users, creating a network of “sensors”
- Email is deleted from the user's inbox to prevent future exposure
- Easy deployment via MSI file for Outlook, G Suite deployment for Gmail (Chrome)
This is a great way to better manage the problem of social engineering. Compliments of KnowBe4!
If you do not like to click on buttons with redirects, here is a link you can cut and paste into your browser: https://info.knowbe4.





