According to MeriTalk, an editorial and events organization that focuses on Federal IT and government computing technologies, governments are moving some, or all of their IT to the Cloud, because of its attractive pricing models in addition to other value added services.
MeriTalk noted that “both Federal and state governments use Office 365 for reasons such as cost savings, security, privacy, and accessibility. The State of New York saved $3 million a year when it adopted Office 365 and the city of Chicago experienced an 80 percent decrease in cost per employee.
Microsoft also restricts content so it’s only shared with intended users, and contains tools to make its technology accessible to people who are visually impaired, deaf, or hard of hearing. These added enhancements and accessibility features are costly for organizations to build and maintain internally.
The Office 365 Account Compromise
But according to a new Barracuda blog post, on August 30, Office 365 is becoming a popular place to get Phished.
“Cybercriminals have a long history of designing attacks to reach the largest number of eyeballs possible. From the early days of traditional spam, to search or trending topics on social platforms, criminals follow the users—and Office 365 has become a breeding ground for highly personalized, compelling attacks.”
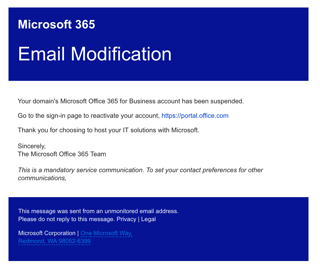
The new threat is called the Office 365 Account Compromise The red flag is an email purportedly coming from Microsoft notifying you that your account has been suspended and imploring you to take action by clicking on the link in the graphic. Microsoft does not typically send such suspension notices.
The attack methodology is the typical “credential grab”
Click on the graphic link. Provide the crooks with your login credentials and bam. Your account is compromised. Your contacts are compromised. Your organization is now susceptible to lateral penetration from trusted emails.
Spear Phishing is an email targeted at a specific individual or department within an organization that appears to be from a trusted source. It's actually cyber criminals attempting to steal confidential information. (The Knowbe4 blog currently has over 469 blog entries covering phishing exploits, methods and tips to mitigate them.)
The bad guys are no longer sending amateur emails with the usual big red flags like poor spelling, sloppy graphics, and grammatical errors. The current crop of phishers uses carefully constructed, next generation, socially engineered templates which are often hard to recognize without special security training.
There are usually several common themes involved in launching a phishing attack. Some are designed to install ransomware, others steal your credentials, while others may try to target a few key people in positions of power (CEO Fraud) to wire money to a cyber crook.
Microsoft is trying to build phishing detection into Office 365 but it only offers Advanced Threat Protection as a part of its Office 365 Enterprise E5 plan which is much more costly and uses a method called URL detonation and Dynamic delivery.
At the end of the day, machine-based detection while good but expensive is likely not yet a replacement for individual security awareness training against the potential for human error.
Commonly used phishing methods are to get you to open a PDF, ZIP file, or even a graphic which has an embedded stealth executable that executes scripts that present you with a phony but carefully designed simulated login page all designed to steal your credentials.
According to a recent Barracuda survey:
- Of respondents using the cloud today, 40 percent of their infrastructure is already in the public cloud, and they expect to increase this to almost 70 percent within five years.
- 99 percent said that their organizations have seen benefits as a result of moving to the public cloud.
- 91 percent reported they had concerns over their use of public cloud, with 54 percent stating that cyber attacks are their chief concern.
- 71 percent felt the cloud provider was responsible for customer data in the public cloud, and 66 percent felt the cloud provider was responsible for their applications in the public cloud.
- Nine out of 10 (91% ) of organizations reported they had concerns over their use of public cloud, with cyber attacks being the chief concern at 54%. Over half (56%) had experienced at least one cyber attack, and 30% expect this to continue in the future.
Sources:
https://www.meritalk.com/articles/office-365-protects-itself-as-prime-target-for-spear-phishing/




