 An Eastern European cybercrime gang has started a new TorrentLocker ransomware campaign where whole websites of energy companies, government organizations and large enterprises are being scraped and rebuilt from scratch to spread ransomware using Google Drive and Yandex Disk.
An Eastern European cybercrime gang has started a new TorrentLocker ransomware campaign where whole websites of energy companies, government organizations and large enterprises are being scraped and rebuilt from scratch to spread ransomware using Google Drive and Yandex Disk.
Japanese antivirus company Trend Micro reported that this worldwide, multilingual campaign has focused on the U.S. as well as the U.K. The attack starts with an email which looks like it's from British Gas or DHL. There is no attachment, just a link that goes to a very real-looking website. It's a malicious, full copy of the original website and required the user to enter a captcha, to see their energy bill or a shipping statement.
The captcha is used to prevent automatic analysis of the malicous website by automated analysis tools run by security companies. As soon as the capthca has been entered, a zip file gets downloaded. Earlier these files were hosted at sites like Sendspace, Mediafire and Copy.com but now they are pulled from Google Drive and Yandex Disk.
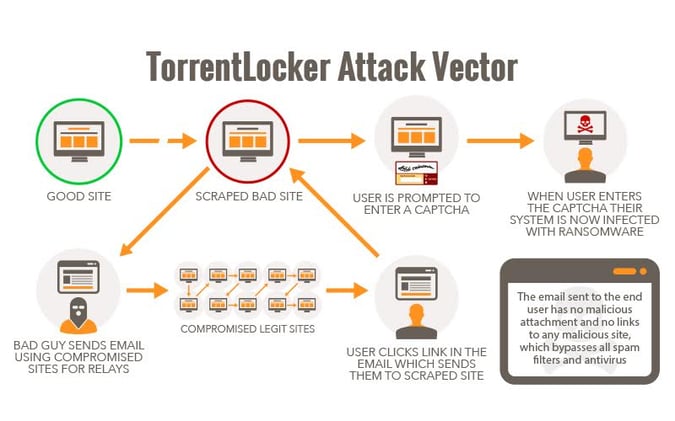
To host the pictures that are being used in the emails, the criminals use a whopping 800 hacked websites which also functioned as redirects for the links in the websites. This is a well-organized, industrial-scale criminal operation.
TorrentLocker is a relatively recent type of ransomware that was discovered as early as February 2014. At a first glance, many unsuspecting victims may mistake TorrentLocker for CryptoLocker. For one, the fact that the ransomware claims to be CryptoLocker, according to the lock screen that victims will see when their computers are attacked, is a little confusing. Criminals gangs regularly rip off each other's brands and code, there is no such thing as copyright in the Internet criminals underground.
Having no malicious attachment, and linking to a legit (but compromised) website makes it very hard for automated spam filters and antivirus to catch emails like this, and they will regularly make it through the filters. That's why it is really important to step end-users through effective security awareness training, and make sure that they do not fall for social engineering tactics like this.
Find out how affordable this is for your organization. You will be pleasantly surprised.





