Security experts have warned for years that our smartphones are due for a major cyberattack. Like PCs back in the early days -- the 1990s -- mobile phones are largely unprotected by antivirus software, and they're a treasure trove of valuable information. So why hasn't the smartphone Armageddon happened yet?
"The money is in mobile, and that's where they're moving. Malware on mobile phones is going to be as prevalent as on the PC. It's inevitable, unfortunately."
That was my quote in a September 2012 CNN Money article titled Your smartphone will (eventually) be hacked, and boy has it ever come true.

JD Sherry of Trend Micro discussed the latest mobile security trends and threats at the Gartner Security & Risk Management Summit. He touches on the shift of ransomware from PCs to mobile devices. Here is a roundup of the latest mobile threats:
iPhone Ransomware
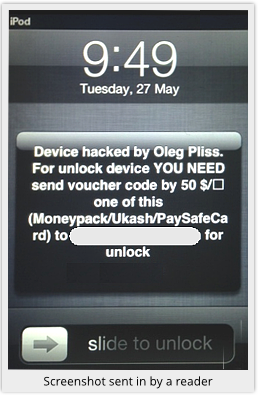 After ransomware hit Windows PCs and Android devices, some miscreant has found a way to pull a similar scam for Apple devices.
After ransomware hit Windows PCs and Android devices, some miscreant has found a way to pull a similar scam for Apple devices.
In May of 2014, a large number of people mostly located in Australia and the UK, are reporting they have come under an unexplained attack that holds their iPhones and iPads hostage and demands they pay a $100 ransom.
One user from Melbourne, said: "I was using my iPad a short while ago when suddenly it locked itself. I went to check my phone and there was a message on the screen (it's still there) saying that my device(s) had been hacked by Oleg Pliss and they demanded $100 USD/EUR (sent by paypal to lock404(at)hotmail.com) to return them to me."
Less than a month after we heard about this attack, John Zorabedian at Sophos reported that two criminals behind the attack were arrested by Russian authorities. Russian police said the two hackers were responsible for scamming users in Russia, but didn’t mention victims in Australia and the UK.
A 23-year-old and a 17-year-old from Moscow confessed to phishing Apple users with an ‘online video service’ that required them to enter their Apple IDs and using the Find My iPhone feature to lock the devices until the victims paid a ransom of up to $100 USD.
If a hacker gets access to your Apple ID they can use it to create an iCloud account which can then be used to lock any associated Apple devices remotely.
The pair was caught on CCTV when they were withdrawing victims’ payments at an ATM. Agents subsequently searched the hackers' apartments and seized PCs, phones, SIM cards and literature on hacking.
Android Ransomware
ScarePakage
900,000 Android phones were hit by this ransomware in a span of just 30 days.
Lookout, a San Francisco-based mobile security firm first discovered the ScarePakage mobile ransomware targeting Android users in the US in late August 2014.
 Users get infected with fake apps appearing to be Adobe Flash and well-known antivirus apps that pretend to scan the device when launched.
Users get infected with fake apps appearing to be Adobe Flash and well-known antivirus apps that pretend to scan the device when launched.
Victims get some variation of the following message: "You are guilty of child porn, child abuse, zoophilia or sending out bulk spam. You are a criminal. The Federal Bureau of Investigation has locked you out of your phone and the only way to regain access to all your data is to pay us.”
You can’t navigate away and even if you try restarting your phone, the message pops back up immediately. The only way to regain control of your device is to pay several hundred dollars in a MoneyPak voucher to the cybercriminals
Lookout’s engineers determined that the authors are likely from Russia or somewhere else is Eastern Europe based on language and slang found in the code.“This is, by far, the biggest U.S. targeted threat of ransomware we’ve seen,” said Jeremy Linden, a senior security product manager at Lookout. “In the past month, a single piece of malware has infected as many devices in the U.S., as a quarter of all families of malware in 2013.”
Android.Locker.38.origin
 Researchers in Russia discovered an Android ransomware strain in September of 2014 which does not lock the device just once but twice. It spreads by using a social engineering trick, disguising itself as a system update, and as soon as the user downloads the app, it asks for admin rights. Once installed, a message is sent to a remote server that the infection is successful.
Researchers in Russia discovered an Android ransomware strain in September of 2014 which does not lock the device just once but twice. It spreads by using a social engineering trick, disguising itself as a system update, and as soon as the user downloads the app, it asks for admin rights. Once installed, a message is sent to a remote server that the infection is successful.
The "extra" feature is a second lock, which kicks in if the user tries to remove the initial ransomware infection. The command to lock the device can be sent trough the command & control server and also via text. First, the device gets put into stand-by (screen lock) mode and then shows a fake warning that all files will be erased.
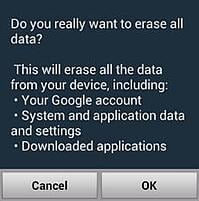 The moment the user makes a choice related to this fake warning, the ransomware brings up the lock screen again and activates a feature that requires the user to enter a password to toggle off the standby mode.
The moment the user makes a choice related to this fake warning, the ransomware brings up the lock screen again and activates a feature that requires the user to enter a password to toggle off the standby mode.
Even if the feature hasn’t been used before, the malicious locker sets its own password: "12345". That way the infected smart phone or tablet is locked until the criminals involved get their ransom. The lock can be removed with the set_unlock command, or the user resets all the device's settings to default.
Worm.Koler
 Android phones have by far the largest market share, and thus are mobile malware target #1. There is now a new variant of the Koler malware that spreads itself via text messages and holds the phone hostage until the ransom is paid.
Android phones have by far the largest market share, and thus are mobile malware target #1. There is now a new variant of the Koler malware that spreads itself via text messages and holds the phone hostage until the ransom is paid.
Worm.Koler displays localized ransomware messages in at least 30 countries, but 75% of this latest Koler variant infections were seen in the U.S.
Researchers from mobile security firm AdaptiveMobile discovered a new variant named Worm.Koler in October of 2014 that spreads via SMS spam and social engineers users into opening a shortened bit.ly URL, turning Koler into an SMS worm. Perhaps this is why Google at the moment simply blocks any and all bit.ly URLs.
When a phone is infected, it will send an SMS message to all contacts in the device's address book stating: "Someone made a profile named -[the contact's name]- and he uploaded some of your photos! is that you?" followed by a Bitly link.
When a victim falls for the trick and taps the link, they are redirected to a Dropbox page with a download link for a 'PhotoViewer' app that, if installed, will cause the ransom screen to pop up, claiming the device has been locked up because of having illicit content and users must pay $300 via MoneyPak to 'waive the accusations.'
What to do about it:
If you see a sudden ransom screen on your phone, do not pay. Koler does not actually encrypt the files, so you can eliminate this pest from your phone by these simple two steps:
- Reboot your phone in "Safe Mode"
- Remove the "PhotoViewer: app using the normal Android uninstall tool.
To protect yourself from similar future threats, have the "Unknown Sources" option turned off in your Android device security settings menu. This will block the user to install app from unknown sources, but only from the official Google Play store.
Adult-themed Android Ransomware
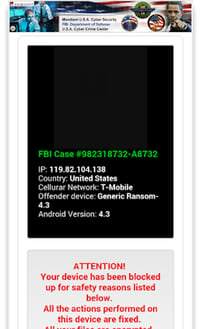 Another adult-themed strain also discovered in September of 2014 uses pictures of the user to manipulate them into paying a $500 fine. The variant presents itself as a porn app. Once the user installs it and grants admin rights, the code makes a stealthy picture and shows this picture with the extortion demand.
Another adult-themed strain also discovered in September of 2014 uses pictures of the user to manipulate them into paying a $500 fine. The variant presents itself as a porn app. Once the user installs it and grants admin rights, the code makes a stealthy picture and shows this picture with the extortion demand.
In the on-screen demand, the country of the user, their IP address, their ISP and details about the device are displayed with the notification a crime has been committed and to get access to the device a fine needs to be paid.
The ransomware stays active, even after a restart of the device until the fine is paid. However, there is a way around this malware. Restart the device in safe mode, remove administrator rights from the app, and uninstall the app.
SimpLocker
 IT Security company Check Point alerted about a Simplocker variant in September of 2015, which locked tens of thousands of Android phones and tablets. Victims are told to pay between 200 and 500 dollars to get access to their files. The infection is relatively easy to prevent, as it's only spread through unofficial download sites (meaning not Google Play) and mis-identify themselves as "Flash Player".
IT Security company Check Point alerted about a Simplocker variant in September of 2015, which locked tens of thousands of Android phones and tablets. Victims are told to pay between 200 and 500 dollars to get access to their files. The infection is relatively easy to prevent, as it's only spread through unofficial download sites (meaning not Google Play) and mis-identify themselves as "Flash Player".
In case the user installs the app, they get a spoofed alert purportedly from the NSA that they need to pay a fine within 48 hours. If not paid, the fine doubles. End-users are not able to remove the app easily, and even then the files are encrypted. Check Point's research showed that around 10% of the users did pay the ransom, which is much higher than other strains.
LockerPin
Security researchers at ESET discovered the first real example of malware that is capable to reset the PIN of your phone to permanently lock you out of your own device. They called it LockerPin, and it changes the infected device's lock screen PIN code and leaves victims with a locked mobile screen, demanding a $500 ransom.
Since the lock screen PIN is reset randomly, paying the ransom amount won't give you back your device access, because even the attackers don't know the randomly changed PIN code of your device. This is a novelty among ransomware, usually they do everything possible to unlock the device, up to and including live tech support.
LockerPin is spread through an adult entertainment app called Porn Droid, and installed from third-party websites, warez forums, and torrents – outside of the official Google Play Store.
Once installed on the victim's smartphone, the app first tricks users into granting it device administrator rights. It does so by disguising itself as an "Update patch installation" window. After gaining admin rights, the malicious app goes on to change the user's lock screen PIN code, using a randomly generated number. Though the majority of infected devices are detected within the United States, the researchers have spotted the infections worldwide.
The only way to unlock the device and get rid of the ransomware app is to perform a factory reset that wipes out all the personal data and apps stored on your device.
Securing Mobile Devices
To avoid falling victim to mobile ransomware, there are precautions you can take:
- Don't install apps outside of the official Apple App Store (Apple devices) or Google Play Store (Android devices)
- Don't grant administrator privileges to apps unless you truly trust them
- Stay away from any and all porn apps and sites, talk about a "honey-trap"!
- Lock your phone with a secure passcode
- Your Apple ID is the key to your iDevices, so make sure you hold onto it tight (don't use your Apple ID for a suspicious media-download website, for example)
- Keep your devices up to date with the latest iOS software version to stay safe from known exploits. For Android users, we also recommend using an anti-virus such as Sophos Antivirus and Security, a free app for smartphones and tablets.
Welcome to the new world of cybercrime. Deploying defense-in-depth and having your own fine-tuned security awareness training program as part of that will help to keep the bad guys out of your network.
Don't be a victim! Get your Ransomware Hostage Rescue Manual.
 Get the most informative and complete hostage rescue manual on Ransomware. This 20-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
Get the most informative and complete hostage rescue manual on Ransomware. This 20-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
- What is Ransomware?
- Am I Infected?
- I’m Infected, Now What?
- Protecting Yourself in the Future
- Resources
Don’t be taken hostage by ransomware. Download your rescue manual now!
Or cut & paste this link in your browser: http://info.knowbe4.com/ransomware-hostage-rescue-manual-0





