We reviewed thousands of domains that have been through our domain spoof test and analyzed more than 10,000 email servers. We found that 82% of these are misconfigured.
What do we mean by misconfigured?
One of the most common security issues – spoofing – is frequently set up incorrectly, allowing a cybercriminal to impersonate an employee, or worse, a key executive. We've worked with thousands of IT managers to determine whether their servers allow spoofed emails to enter an organization disguised as coming from a company’s own domain. Those that are set up incorrectly allow phishing attacks in, making the companies an easy target.
Here's how cybercriminals exploit the issue:
A typical scenario is a spoofed email that looks like it comes from the IT administrator or “IT” asking an employee to update their email account credentials. The uneducated employee fills out their username and password credentials thinking they are complying with a request, missing the telltale signs of a phishing attack with a spoofed email address. This can lead to any number of nefarious scenarios, including a ransomware attack where all computers on the company network are hijacked.
 Why does this matter?
Why does this matter?
Ransomware nearly doubled in the first half of 2016, and phishing emails are the top vehicle used to spread the rapidly evolving threat. Many IT managers and executives are realizing that outdated security techniques will not combat today’s more sophisticated cybercriminal. It is vital that businesses deploy a defense-in-depth strategy with effective security awareness training for all employees from the mail room to the board room included as part of the outer layer, along with policies and procedures.
What can be done to stop this?
Adding security awareness training as part of a defense-in-depth program creates a ‘human firewall’ that is a highly effective part of defending against social engineering attacks. When spoofed phishing attacks make it through the filters, your users are a critical part of your defense. Training employees to make better security decisions helps mitigate the risk of social engineering.
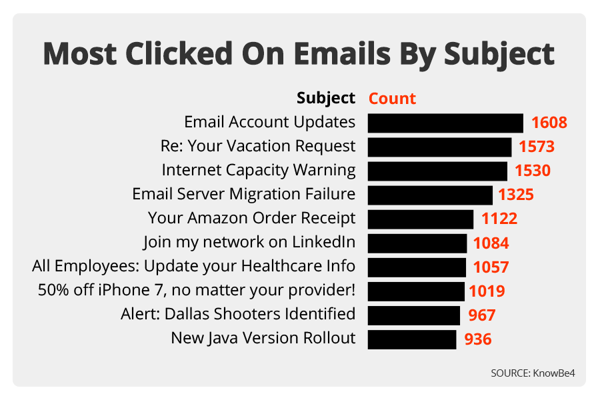
We use a number of customizable email templates for simulated phishing attacks on users. Out of more than three million simulated phishing attacks sent out in Q3 2016, here are the top ten phishing subject lines that employees are most likely to click on:
 Are you aware that one of the
Are you aware that one of the




