 I love that KnowBe4’s customers are among the most knowledgeable and educated people in the world in avoiding phishing scams. KnowBe4’s products help its customers to educate and test which scams a worker will easily recognize and which ones they need more education on. KnowBe4’s product helps administrators figure out exactly who needs more education and on what topics. We know that customers who frequently educate and test their co-workers reduce cybersecurity risk lower than those that do not.
I love that KnowBe4’s customers are among the most knowledgeable and educated people in the world in avoiding phishing scams. KnowBe4’s products help its customers to educate and test which scams a worker will easily recognize and which ones they need more education on. KnowBe4’s product helps administrators figure out exactly who needs more education and on what topics. We know that customers who frequently educate and test their co-workers reduce cybersecurity risk lower than those that do not.
As recently covered here the best security awareness training programs educate people in the most common social engineering attacks first and best. You should make sure your security awareness training program focuses on the most likely attacks.
At the same time, it can’t hurt to sprinkle in the less common types of social engineering attacks so that people get introduced to a wide range of methods and tricks. With that thinking, here are 5 interesting, but more obscure, phishing scams:
-
Browser Notifications
I think everyone has been subjected to an onslaught of browser notifications (see examples below) when they visit new websites for the first time.

Most of today’s browsers and operating systems allow web sites, services, and applications to request the ability to send the user messages even when the user is not on the site, service, or application. The requestors must first ask the user’s permission to send notification messages. Usually, they do so by first sending an “Allow” or “Block” set of options. The “Allow” or “Block” options can be labelled many other ways (e.g., Yes or No, Allow or Deny, etc.), but they are all almost always a “yes” or “no” type of choice.
If the user selects the “no” option, the requester will be prevented from sending future messages and cannot ask even prompt the user again to send messages. This is great. But if the user says “yes”, then the user’s browser or operating system (if they support browser notifications) will be configured to allow that requestor the ability to send the user as many messages as they like. Although the user can prevent future messages being sent at any time by reconfiguring the “yes” option to a “no” option. How you do that varies by operating system and browser.
Most browser notifications are not malicious. But miscreants often abuse the browser notification feature and if the user allows the wrong site, service, or application to get notification permission, then the malicious sender can send malicious requests and content to the user.
Below is an example malicious instance asking for browser notification permission: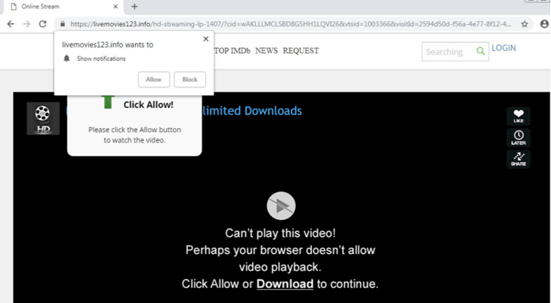
Source: Esputnik
In this example, the user was being prompted to allow notifications so they could see a video. Of course, what happens is the requestor can start sending malicious content and prompts. The notification prompts can contain almost any type of scripting, actions, links, documents, and files. A requestor can even manipulate the user’s email and other applications without the user’s permission or awareness.
A common malicious outcome is the victim is prompted by a fake antivirus warning (see below), which can then be used to trick the user into buying fake (or even real) antivirus software they don’t really need. Other common tricks include installing malware on the victim’s computer or using their email to send malicious messages to the victim’s email lists in their address book.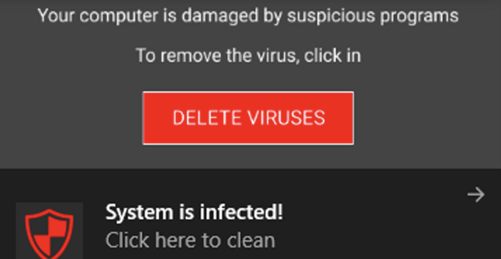
Malicious browser notifications are not super common, but people are tricked and scammed by them. To defend against them, users should be taught about browser notifications, how they work, how they can be abused, and malicious browser notifications. Administrators can also block all browser notifications by default and simply kill this as a potential phishing source. If interested, you can watch my 1-hour webinar on Malicious Browser Notifications. -
NFT Scam
I barely understand NFT (non-fungible tokens) and already they are being used in scams? Yes. An NFT is a blockchain-protected digital right to an underlying physical or digital asset (e.g., art, object, etc.). People buy NFTs to prove ownership of the underlying asset. NFTs have become huge and people are paying hundreds of millions of dollars for them. Most people don’t understand why anyone would pay any, much less hundreds to millions of dollars for NFTs, but people do. Value is in the eye of the beholder.
It turns out wherever there is a lot of easy money to be made, scammers will follow. NFT scams come in many forms. One of the forms are fake NFTs, where someone claiming to be the legitimate owner of the underlying asset, but who really doesn’t have legal ownership, offers it for sale. With these types of scams, the criminal will publish realistic-looking popular NFTs, but for pennies on the dollar. Just like in real life, a “too good to be true” price should always result in high skepticism.
Another NFT scam is a fake NFT store. Most legitimate NFTs are sold on reputable NFT stores with lots of legitimate buyers and sellers. Scammers will create fake NFT stores, using look-alike URLs, which are virtual clones to the real NFT store. They hope visiting users will be tricked into thinking they are on the real site, and buy fake NFTs, giving up their hard-earned money for worthless promises.
In another type of NFT scam, the criminal poses as a legitimate NFT store’s technical support. They will claim there was some glitch in the system and ask the potential victim to share their logon information. Then the scammer will login to the real store as the victim and buy real NFTs, which get sent to the criminal, or buy worthless NFTs from the criminal. Since most NFTs are bought using cryptocurrencies, once the money is stolen it is very hard to get it back. So, if you or a loved one is excited to be involved in the NFT world, make sure you are dealing with legitimate NFTs and NFT stores.
This article discusses NFT-related scams in more detail.
Speaking of scams, I’ll be glad to sell you an NFT of this article…for cheap. -
Spellcaster Scam
I’m not one to believe in non-scientific, esoteric things, like charms, voodoo, astrology, tarot cards, crystals, and magic, but I get that hundreds of millions of very good, smart, people believe in things that I do not. I could be wrong in my disbelief. I’m more of a let live type of person. If it works for you, it works for you. Who am I to get in the way?
Unfortunately, there are outright scammers preying on people who have faith in these things. They’ve always been around, but have multiplied because of the protective anonymity of the Internet. As an example, this woman recounted how she paid to have a spellcaster cast a spell to help her through a tough situation. After paying the spellcaster an initial $100, she balked when the spellcaster tried to get more money from her. And when she refused to pay, the spellcaster threatened negative consequences and hounded her. Although she knew she was more than likely dealing with an outright, non-believing, scammer, she nevertheless feared what this scammer could do to her, both spiritually and financially. She could have avoided the outright scammer by dealing with other service people who were vouched for by people she knew (if that was possible).
Why share this type of scam? They remind me of romance scams that many very good people have fallen for. My mother, rest-in-peace, believed in everything spiritual, including spells, spirits, and tarot cards. If she was still alive today, I’d be warning her to watch out for the outright scam artists who were only trying to take her money without her best interests in their heart.
-
Fake CNN Video
We know social media abounds with fake scams. In this example (see below), someone posts what is supposed to be an urgent plea to watch a CNN video with a follow up request to contribute money to catch the thief.
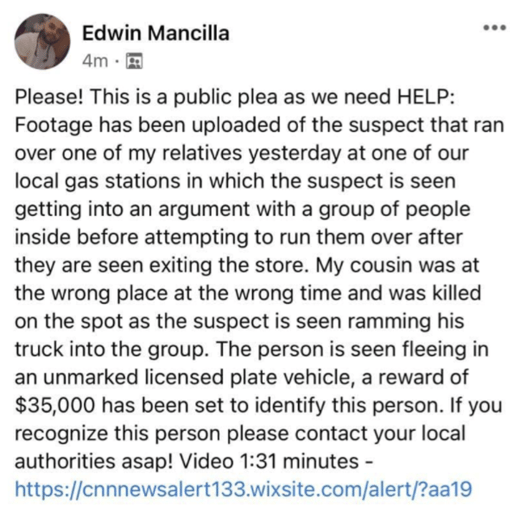
If you click on the link, you’ll be taken to a site that is 100% malicious. They will try to get you to download malicious content or send your credit card information or money to a fake GoFundMe-like web site, but it’s 100% bogus. If click on the contribution link, you’ll be sending your credit card information or money to a foreign location where it will be very hard to recover. The number one clue that this is a bogus scan is that the link contains the letters “cnn”, but does not go to cnn.com. Instead, it goes to Wixsite.com, which is a very popular, public website platform, hosted by legitimate web hoster, Wix. Scammers use Wix because they can create and use free websites for their scams and it’s hard for defenders to automatically block a site hosting tens of thousands of other legitimate web sites.
Any site containing the name or letters of a very well-known brand (e.g., CNN, Microsoft, PayPal, etc.) that doesn’t actually go to the real web site should be skipped. -
PayPal Family and Friends
During the Christmas season, I was out on the hunt for a very hard to find, but very popular item for one of my many hobbies. Every website store was out of this item for months and it seemed to be on perpetual backorder. I had been trying to get this particular item for at least half a year with no success. The best I could do is “check the Internet” for the item to see if I get lucky and hit a vendor who has it during the brief time before everyone else buys up all supplies. And for months, I did my checking without success.
Last week, suddenly two new websites showed up and they had the item in stock ready to ship. Suspiciously, the item was one-third to half the cost of what everyone else, who was selling out was selling the same item for. This sales ploy was not to the scammer’s advantage, because it became my first red flag and made me look for more red flags.
Although the URLs seemed very legitimate-looking…not the overly generic or random-looking URLs used by most scammers, they were not popular websites I had seen before. Still, the URLs looked like URLs that would be used by real stores or resellers. I looked up the domains using a free Whois lookup service and it revealed that both websites in question had only be registered for a few days. Huge red flag.
But I played along and put in some bogus buyer information. Pretty soon I was taken to the payment page. Every option listed was an option that did not protect my purchase. If you buy items using most credit cards and PayPal, for instance, those services will restore your money (most of the time) if you’ve been the victim of a fraudulent purchase. It’s one of the main reasons to use a service like they offer. But on both of these bogus web sites, all the payment options, although legitimate, were not options that protected my money if the transaction involved was bogus. The payment options included Western Union, cryptocurrencies, prepaid money cards, gift cards, Venmo, and PayPal’s Family and Friends feature.
The ones that bothered me the most were Venmo and PayPal’s Family and Friends. Many people today are used to using both online services for making payments to friends, family, and vendor. The key is that Venmo, by default, doesn’t offer fraud protection. You can pay a 3% fee to get that fraud protection, but it doesn’t come by default. Traditional PayPal transactions do have fraud protection, but not when you use the Family and Friends feature. Although like, Venmo, you can change the Friends and Family to a “Goods and Services” transaction, pay a small percentage transaction fee, and get the coverage.
The problem is that the vendors will try to get you to skip any buyer protection plans. They are likely scamming you and are going to take your money. They can’t do that nearly as easily if you get buyer protection.
Note: Many legitimate vendors use these non-fraud protected services as well as a way to avoid paying the normal service fees and some to avoid paying taxes.
Both Venmo and PayPal make it harder for the seller to run off with the money. But with both programs, even though they have fraud protection available, whether or not you get your money refunded due to a fraudulent transaction is up to Venmo and PayPal. They could determine that your transaction isn’t eligible or even decide that maybe you are the scammer.
Do yourself a favor. Never do a financial transaction with a stranger using a payment method without default fraud protection. If the vendor tries to force you to use a method that doesn’t protect you against fraud, just avoid doing business with that vendor or person. It isn’t worth the risk no matter how much you want the good or service or what a great deal it seems to be.
Here’s an article on PayPal Family and Friends payment scams.
How to Avoid All Scams
All scams, no matter whether they are very popular or obscure, share a few common message traits. You should train yourself and your family, friends, and co-workers, on how to recognize these common traits of any scam. Any message, no matter how communicated (e.g., email, web, instant message, voice call, etc.), should be evaluated to see if they contain the four traits below. And if they do, the user should confirm the request using some other alternative, trusted, method before performing. Teaching these signs of a possible scam can save a lot of time, money, and heartache.

An article focusing on these 4 traits of a scam was first covered in a recent blog post.
In conclusion, a good security awareness training program teaches people the most common scams first and best. But it still can’t hurt to be up on the latest obscure scams. They can still hurt people and organizations and some of them may morph into more popular scams. Make sure you and your organization are prepared no matter what the scam and how it arrives.
 Here's how it works:
Here's how it works:




