 With an estimated take of over $80 million a month, this scam uses new evasive tactics designed to make detection and investigation of these attacks difficult at best.
With an estimated take of over $80 million a month, this scam uses new evasive tactics designed to make detection and investigation of these attacks difficult at best.
Who doesn’t want to win a prize from a legitimate company for doing little more than filling out a survey? Seems easy enough and not dodgy at all, so why not? And when the prize is an expensive Samsung or Apple mobile phone, it’s even more of interest, right?
This is exactly the premise of a new scam outlined by security researchers at Group IB. In this survey scam, victims are made to think the survey is from a well-known business.
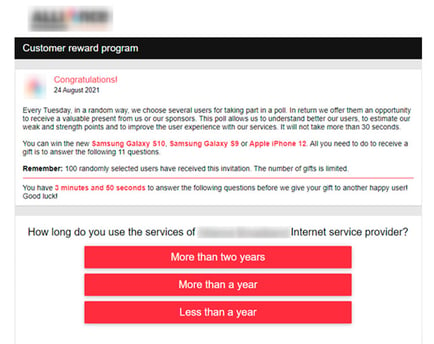
Source: Group IB
What makes this scam interesting is some of the work done behind the scenes. Using a technique Group IB calls “traffic cloaking”, the scammers use a series of multiple redirects to first gather information about the victim, their session, time zone, country, IP address, etc. This information is used to create a landing page tailored for the victim. In the example above, notice how the question is about a specific Internet provider – no doubt, the scammers have used the victim’s IP address to identify their ISP and are using it as part of the survey to make the victim feel like it is legitimate.
The scam comes in when victims are wanting their chance for that amazing prize. The scammers collect the victim’s full name, email, mailing address, phone number, and complete bank card data.
The simple truth of “when something sounds too good to be true, it usually is” just doesn’t seem to resonate with Internet users – and that includes employees of your organization. It’s one of the reasons continual Security Awareness Training is so important; by ensuring users are trained at regular intervals (rather than, say, a quarterly breakroom training), users begin to change their mindset towards vigilance when interacting with email and the web, making it difficult for scams like the one above to be effective.
 Here's how it works:
Here's how it works:




