 Offering targeted victim organizations an opportunity to bid on infrastructure projects, this scam seeks to harvest credentials using a new mix of tactics to evade detection.
Offering targeted victim organizations an opportunity to bid on infrastructure projects, this scam seeks to harvest credentials using a new mix of tactics to evade detection.
Security researchers at anti-phishing vendor Inky have spotted a new phishing campaign that impersonates the U.S. Department of Transportation using newly-created domains to trick victims out of their cloud credentials. Using a mix of commonly-used tactics, but executed in a new way that increases their chances of avoiding detection, these scammers have been targeting contractors looking to take advantage of the massive spending bill.
The email content sounds legitimate enough, as does the spoofed DOT website (below) which is actually a copy of the legitimate DOT website. When the victim clicks on the button to bid, they are presented with what appears to be a Microsoft 365 logon dialog box that states “Logon with your email provider.”
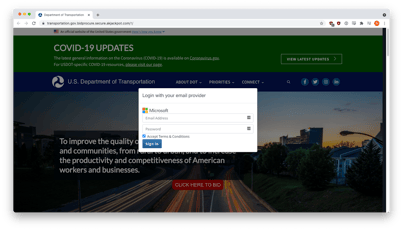
Source: Inky
This is the crux of the scam – with so many web-based sites leveraging trusted authentication partners like Facebook, Gmail, and Office 365. This doesn’t sound out of the ordinary.
This kind of scam preys on the victim’s desire to get some of the $1 Trillion that’s up for grabs. Training users via Security Awareness Training to be mindful of spoofed URLs (transportationgov[.]net, in the case of this scam) is all it takes to keep credentials – and your organization – secure.
 Here's how it works:
Here's how it works:




