 As the COVID-19 health crisis rages on and millions of workers and students move to working from home (WFH) and online distance education, no one should make the error of thinking that working and learning from the comfortable and familiar surroundings of home somehow makes these employees and students safe. They are not safe. If anything, they're sitting ducks.
As the COVID-19 health crisis rages on and millions of workers and students move to working from home (WFH) and online distance education, no one should make the error of thinking that working and learning from the comfortable and familiar surroundings of home somehow makes these employees and students safe. They are not safe. If anything, they're sitting ducks.
Hitting 'Em Where They Live
Many users who find themselves sheltering in place will be struggling with technology and services that they have little experience with. Moreover, their home computer environments may not be nearly as secure and protected as those they enjoy at the office or school.
Inexperienced and emotionally rattled students and employees represent potentially severe security problems for organizations of all shapes and sizes -- and huge opportunities for malicious actors looking to worm their way into the networks of companies, governmental organizations, and schools across the country. And they know it.
Just this morning we spotted a straightforward attempt to target remote workers at one particular company with a phishing email spoofing the company's IT department and demanding recipients click a malicious link to "securely connect to our network from home."
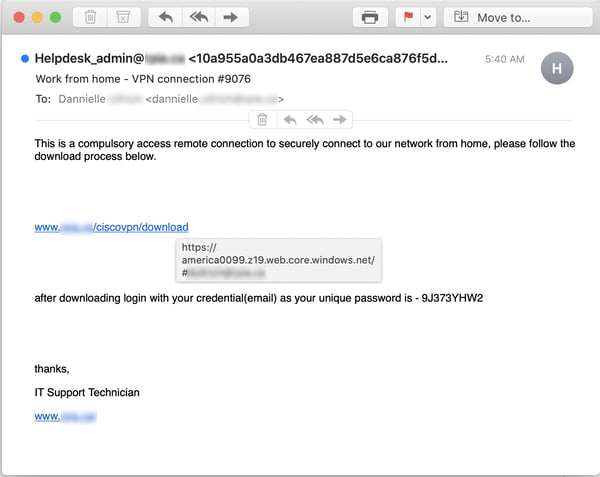
This particular phish is a bit crude. But don't be fooled. There will be more of these, and they will get better as malicious actors do their research and learn more about how employees and students are actually connecting to their schools and places of employment.
The malicious link in that email takes users to -- where else? -- a credentials phish.
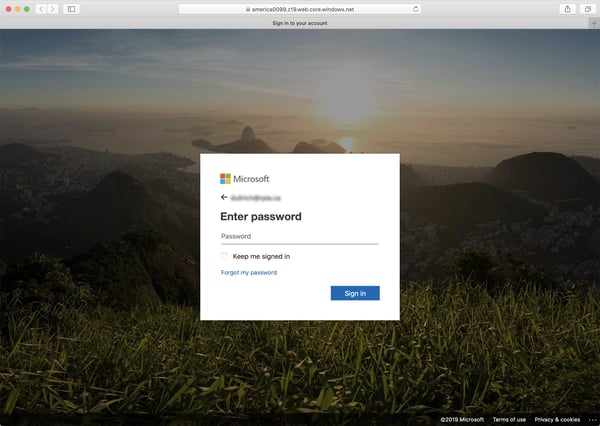
Note that this slick spoof of Microsoft's familiar login page is actually hosted on a Microsoft domain -- windows.net, which is used for Microsoft Azure. It's an attractive hosting option for malicious actors as the domain seems to carry the imprimatur of Microsoft itself.
As such, many users could be easily fooled into believing this page to be a legitimate Microsoft login page and not a malicious spoof -- esp. those who are new to the process of working and learning from home and who have little familiarity with the software and services that make it happen.
Protect Your Users & Networks -- Now
The COVID-19 health crisis has confronted organizations with a myriad of new challenges. This is one of them, and it's a big one. New-school Security Awareness Training is the solution.
Now is the time to be training your users to spot and correctly handle malicious attacks landing in their inboxes, voice mail, and messaging apps. Those who wait for the crisis to pass may well find their networks overrun with malicious actors, backdoor trojans, and ransomware -- just as they're trying to get back on their feet and back in business.
 Here's how it works:
Here's how it works:




