Doug Olenick at SC Magazine reported on something noteworthy: "The growing threat posed by ransomware and the possibility that cybercriminals will graduate from extorting end users to large corporations topped the worry list of IBM's X-Force threat team in its Q3 threat intelligence report.
The "August 2015 IBM Security IBM X-Force Threat Intelligence Quarterly, 3Q 2015," issued Monday, included a look at an increasing number of attacks coming from the dark web that employ Tor to steal intellectual property.
While ransomware has been a menace for years, John Kuhn, senior threat researcher, IBM Security X-Force, told SCMagazine.com it has progressed from attackers using simplistic scams, such as WinLocker, that simply annoyed people to well-organized attempts to steal money.
“We found ransomware is now so much more sophisticated with CryptoLocker and Cryptowall [software] and we see more people in the Deep Web buying Cryptolocker-type software, which will make it even easier for a beginner to get started,” Kuhn said.
While there have been a few cases of government agencies and companies being targets for ransomware, Kuhn said historically the average computer user has suffered the brunt of the attacks. But this might not remain so.
“My fear is they will move up to the corporate level,” he said, adding that it's only a matter of time before the crypto guys catch up to those already assaulting large firms and begin demanding huge sums of money.
IBM estimated that from 2013 to now CryptoLocker and Cryptowall campaigns have reaped $1 million about $19 million combined.
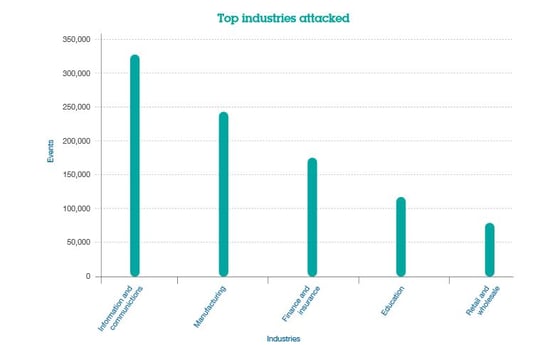
The threat posed by attacks originating in the dark web is something companies need to be concerned about now. Kuhn said the number of web-application attacks tracked during the quarter are steadily increasing compared to previous periods with more than 300,000 attacks targeting information/communications firms and just under 250,000 attacks hitting manufacturers.
Most of these were not an attempt at immediate financial gain, but were searching for intellectual property, he explained. Tracking down the perpetrator is impossible since Tor cloaks attacks in anonymity, the report said. The study noted that the United States, The Netherlands and Romania topped the list of nations where malicious Tor events originated between January and May 2015.
To help ward off and mitigate these attacks Kuhn said it is imperative for companies to block both inbound and outbound traffic to the Tor network and back up data to a storage facility that is not mapped visibly as a drive on the computer.
“Corporate networks really have little choice but to block communications to these stealthy networks. The networks contain significant amounts of illegal and malicious activity,” the report stated.
Kuhn said some companies have a hard time turning off this particular spigot as they want to retain access to those people who use TOR for legitimate purposes, but he said it is not worth the risk.
Hat Tip to SC Magazine
Learn how you can prevent such an attack and protect your organization by downloading KnowBe4's Ransomware Hostage Rescue Manual: The most informative and complete hostage rescue manual on ransomware:

Don't like to click on redirected buttons? Copy and paste this link in your browser:




