|
CyberheistNews Vol 4, 37
Editor's Corner

Symantec: Crypto Ransomware Phishing Up 700 Percent in 2014
Very interesting data from Symantec. This is fresh from the press and shows Phishing, Spam and Malware trends. As reported in their annual 2013 threat report, that year saw a 500 percent increase in ransomware in the latter part. Overall ransomware levels remained high through March 2014, and then slowly started to decline, in part due to the disruption of the GameOver Zeus botnet back in late May.
In contrast, during 2014, crypto-style ransomware has seen a 700 percent-plus increase. These file-encrypting versions of ransomware began the year comprising 1.2 percent of all ransomware detections, but now make up 31 percent at the end of August. One variant known as CryptoDefense began to appear in large numbers in early June. By the end of July, it made up 77 percent of all crypto-style ransomware for the year to date.
This is a pretty staggering uptrend, which only points out that you really, really need to step end-users through effective security awareness training. For graphs and links to the Symantec August 2014 report, see our blog:
http://blog.knowbe4.com/bid/396484/Symantec-Crypto-Ransomware-Phishing-Up-700-Percent
Home Depot Hit by Same Russian Hackers as Target
Right after the Target Hack, C-level execs at Home Depot Inc. put together a task force to prevent being the victim of a similar attack. The task force recommended to fully encrypt payment card data at the chain's 2,200 stores, but it wasn't until many months later that they started the work.
You could ask yourself how could this happen, with the Target hack fresh in mind?
The reason is that they thought they could defend against a hack like this, and apparently gave the wrong priority to the possibility they had already been breached. Instead of prevention, they should have focused on detection of the existing breach and getting the hackers out of their network. OK, hindsight is 20-20, but in this case it should have been obvious.
The data breach is very similar to the breach at Target. The malware used to steal card data from Home Depot had the same code base as the tool used against Target, people who analyzed the code said. (The data is generally vulnerable in the brief moment it passes into the system's memory after the card is swiped.) After analyzing the malware, it was found that in both "malwares', the code had Russian words in it.
Russian President Vladimir Putin allows cybercrime to continue, because he considers it a resource and now and then tells them to attack a country that is bothering Russia in some way. Imagine, cyber mafia as shock troops for the Russian government. Draw your own conclusions.
It would not surprise me if they got in the same way they got into Target, spear-phishing one of the Home Depot vendors. Another reason to step your users through effective security awareness training.
Want News Like This Much Faster?
We have two ways to do that. Follow me on Twitter @stuallard and you get tweets the moment I hear some hot IT security news. You can also check www.hackbusters.com once or twice a day, there is Trending, Most Popular and Recent news, purely about IT security and it's updated real-time.
Quotes of the Week
"One of the most beautiful qualities of true friendship is to understand and to be understood." - Lucius Annaeus Seneca, Philosopher (5 BC - 65 AD)
"The key is to keep company only with people who uplift you, whose presence calls forth your best." - Epictetus, Philosopher, AD 55 – AD 135)
Thanks for reading CyberheistNews! Please forward to your friends. But if you want to unsubscribe,
you can do that right here
|

SC MAG POLL SHOCKER: 40% Do Not Train Users ?!
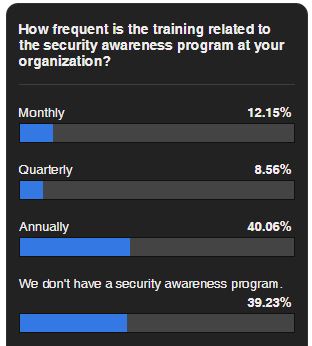
SC Magazine ran a poll this week, and asked: "How frequent is the training related to the security awareness program at your organization?" A whopping 40% answered "We don't have a security awareness program"
And then the other shoe dropped: Another 40% only trains users annually. I almost had a heart attack when I saw those numbers. Really???
And then organizations are surprised that end-users click on phishing emails and get their files encrypted by ransomware?
Find out how affordable security awareness training is for your organization now. Get a quote and demand budget for effective Kevin Mitnick Security Awareness Traing right away. This is the best bang you get for your IT security budget. And you get a crypto-ransom guarantee: we pay your crypto-ransom if you get hit. GET A QUOTE NOW:
http://info.knowbe4.com/ransomware-cryptolocker-guarantee_primary_14-08-26-0

NEW - Vishing Security Tests (VST) Now Available
We are excited to announce that you are now able to test your users with our brand new automated interactive voice response phishing module. Very much like our PST's, the VST module trains your employees against social engineering attacks but now via the phone on their desk.
Cyber criminals have moved into fully automating these types of attacks, utilizing open source tools that allow thousands of dials per hour, attempting to trick end-users into giving out confidential information like their voice mail pin number, (company) bank account and credit card information, and/or healthcare related data.
The new VST feature includes five Kevin Mitnick VST Scenarios™ which you can use to test your users and keep them on their toes with security top of mind. As a KnowBe4 customer you are able to upload a CSV file with employee phone numbers, choose a VST template, and start the campaign, very similar to the existing phishing security test campaigns that you already run.
If an end-user enters data via the telephone keypad in response to the VST, that means a "fail" which can be used as a reason for a short remedial training. KnowBe4 added this module to the platinum pricing level and existing customers are invited to do a free VST to try this powerful new option to further strengthen the human firewall you need to protect your network and corporate data.
Talk to your sales rep or reseller for more information about the new VST module!

We Are at War in the Digital World
I just read an opinion editorial in the Wall Street Journal that really did clarify the new threat we are faced with the last decade. "Ten years ago, the 9/11 Commission Report triggered the most significant reorganization of the U.S. intelligence community since 1947. Two months ago, the former members of the commission—we are among them—issued a new report assessing where national security stands, 13 years after the most devastating attacks on America's homeland.
Most of the new report's observations focused on counterterrorism, the central focus of the 9/11 Commission. But in speaking with many of the nation's most senior national-security leaders, we were struck that every one of these experts expressed concern about another issue: daily cyberattacks against the country's most sensitive public and private computer networks.
A growing chorus of national-security experts describes the cyber realm as the battlefield of the future. We are at war in the digital world. And yet, because this war lacks attention-grabbing explosions and body bags, the American people remain largely unaware of the danger. That needs to change."
Could not have said it better myself, and am thrilled to see this in the WSJ, because it needs to penetrate into the C-level suite. Messrs. Kean and Hamilton served as chairman and vice chairman of the 9/11 Commission and make the case for a National Cyber Commission, and a National Cyber Center, which would bring together government and private experts to ensure unity, similar to the National Counterterrorism Center, created 10 years ago in response to a 9/11 Commission recommendation, which is working well.
"In recent months, we have heard time and again from leading experts that the cyber threat is serious—and that the government is not doing enough. One lesson of the 9/11 story is that, as a nation, we didn't awaken to the gravity of the terrorist threat until it was too late. We must not repeat that mistake in the cyber realm." Article in WSJ (paywall):
http://online.wsj.com/articles/tom-kean-and-lee-hamilton-a-new-threat-grows-amid-shades-of-9-11-1410390195

Social Engineering Audits on the Rise
A social engineering audit looks for internal data or security breaches. The uptick in these audits is a reminder to C-level execs that security is an inside as well as an outside responsibility. The Target data breach and a new data breach at Home Depot are reminders to CIOs and CSOs about the dangers of security problems on a massive scale, though the smart executives are giving equal time to the potential of internal data breaches. Article at TechRepublic:
http://www.techrepublic.com/article/social-engineering-audits-on-the-rise-what-this-means-for-cios-and-csos/

Cyber Criminals Use AEA-256 Crypto to Obfuscate Phishing Sites
The Register said: "Well, at least someone listened to Snowden about privacy... Phishing fraudsters have begun using industry-standard AES-256 encryption to disguise the content of fraudulent sites.
Obfuscated phishing sites are nothing new. Various techniques such as JavaScript encryption tools are commonly used but Symantec recently caught what it reckons is the first use of AES-256 encryption in dodgy sites designed to hoodwink consumers into handing over their login credentials.
"The site used AES to hide the phishing page content", Paul Wood, manager of cyber security intelligence at Symantec, told El Reg. The tactic is designed to make the analysis of phishing sites more difficult for security researchers without interfering with how sites are presented to victims, as a blog post by Symantec explains. More:
http://www.theregister.co.uk/2014/09/09/phishing_scam_uses_aes_crypto_to_hide/

Cyberheist 'FAVE' LINKS:
* This Week's Links We Like. Tips, Hints And Fun Stuff.
SUPER FAVE: Galactic Gear Reviews The Origin M50. I want one!!! (Top Gear Parody)
http://www.flixxy.com/galactic-gear-reviews-the-origin-m50-top-gear-parody.htm?utm_source=4
Now...THIS is an airplane safety message I could see over and over:
http://youtu.be/DtyfiPIHsIg
Comic: Movie Hacking and Real Hacking:
http://www.smbc-comics.com/index.php?id=2526
Famous DJ Deadmau5 Does Uber In His McLaren 650S Spider:
http://www.motorauthority.com/news/1094415_deadmau5-does-uber-in-his-mclaren-650s-spider-video
Cardstone teamed up with ad agency Mullen to create a fake job description for a "Director of Operations" - aka "Mom." Priceless:
http://youtu.be/HB3xM93rXbY
Since chewing gum is a simple, no-frills product, Beldent wanted to highlight its social benefits. Great ad!
http://youtu.be/sk7A56KVNBY
The magician duo David and Leeman predict the winning combination of lottery numbers at America's Got Talent 2014:
http://www.flixxy.com/magician-duo-david-and-leeman-predict-winning-lottery-numbers-americas-got-talent-2014.htm?utm_source=4
Serial entrepreneur Mark Cuban explains a very common social media error - and what his company Cyber Dust is doing about it:
http://www.flixxy.com/the-biggest-mistake-people-make-on-social-media-mark-cuban.htm?utm_source=4
9 nightmare sci-fi virtual realities that are closer than you think:
http://www.infoworld.com/slideshow/163531/9-nightmare-sci-fi-virtual-realities-are-closer-you-think-250160
This dancer's body moves to the music almost too well. Really amazing:
http://digg.com/video/this-dancers-body-moves-to-the-music-almost-too-well
|

