 Lead analysts: Cameron Sweeney, Lucy Gee, Louis Tiley, James Dyer
Lead analysts: Cameron Sweeney, Lucy Gee, Louis Tiley, James Dyer
“Super-app” WeChat offers a wealth of functionality—from instant messaging, text and voice messaging, and video calls to mobile payments, ride booking, ordering food deliveries, paying bills and even accessing government services.
Provided by Chinese technology conglomerate Tencent, WeChat has become deeply integrated into daily life in China and usage has been spreading globally. The app now boasts over 1.4 billion active users (24.8% of total internet users).
As well as appealing to legitimate users, the breadth of functionality—particularly WeChat’s mobile payment capability—also makes it attractive to cybercriminals. An initial phishing email is used to move victims into WeChat where social engineering attacks and payment fraud can occur in an environment that it’s more difficult to monitor and secure.
Much like WeChat usage, these attacks are on the rise outside of China.
In 2024, only 0.04% of phishing emails detected by KnowBe4 Defend in the US and EMEA (including the UK) contained WeChat “Add Contact” QR codes. Since the start of 2025, this has risen to 1.43%, spiking in November at 5.1%.
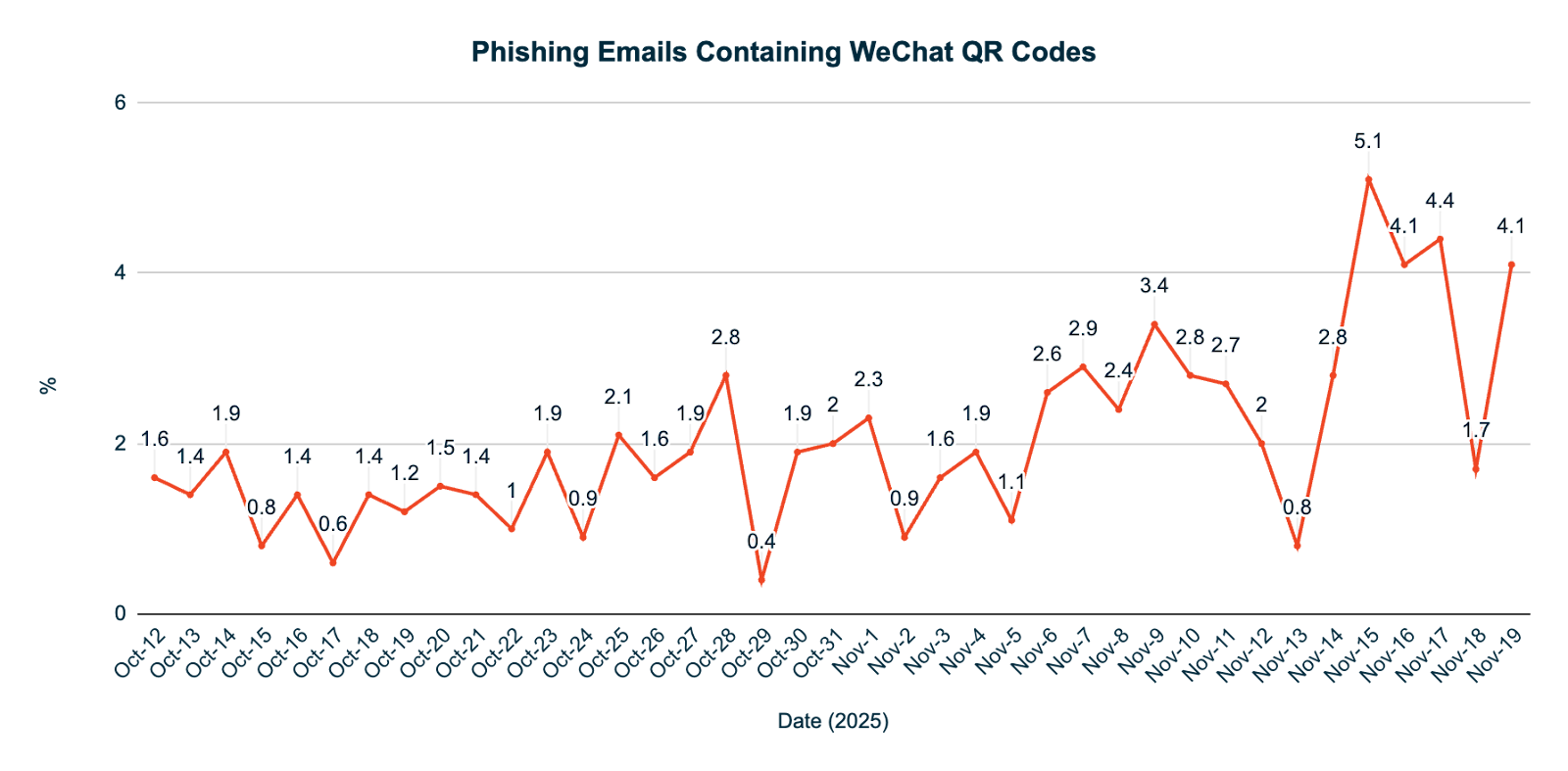
While the overall volume remains relatively low, this represents a 3,475% increase across these regions.
Additionally, 61.7% of these phishing emails were written in English and a further 6.5% were in languages other than Chinese or English, indicating a growing and targeted diversification.
This move reflects law enforcement crackdowns on domestic and near-border fraud networks in China, pushing scam operators to branch out. GenAI has been a key accelerator of this shift, removing the need for language proficiency to send a convincing phishing email or instant message. Both global systems and domestic Chinese LLMs (such as Baidu’s ERNIE Bot) make it easy for cybercriminals to create natural, high-quality phishing emails in non-Chinese languages.
WeChat Phishing Attack Summary
Vector and type: Email Phishing
Techniques: Impersonation, Quishing, Payment Fraud
Bypassed SEG detection: Yes
Targets: Organizations globally
The attacks typically begin with a high-volume phishing campaign generated by a bulk-sending phishing toolkit with a legitimate WeChat “Add Contact” embedded within the template. The emails use social engineering to lure the recipient in with an interesting offer, such as business opportunities, purchase orders, investment tips, procurement requests, job offers or partnership invitations.
The phishing email below was detected by KnowBe4 Defend targeting one of our US customers. The email is written in fluent English, asking the recipient to progress an application for a “Remote Administrative Assistant” role offering key perks to entice the recipient.
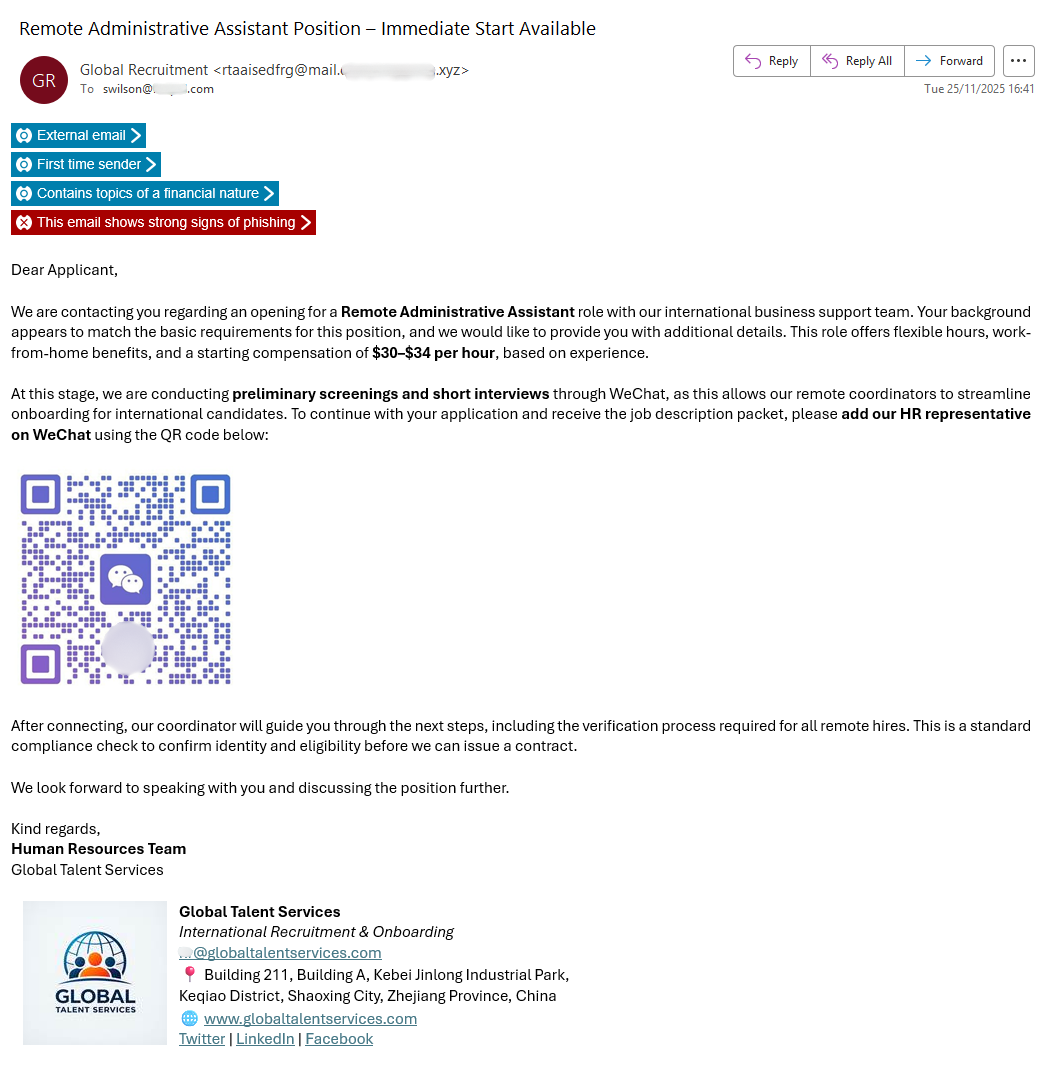
Initial templated email attack sent using a phishing toolkit, with KnowBe4 Defend anti-phishing banners visible.
Once the cybercriminal is added on WeChat, they conduct a personalized conversation designed to socially engineer the target, gradually building trust before moving onto their ultimate aim: financial fraud, such as advance-fee fraud, fake procurement deposits, investment scams, romance-style social manipulation, or requests for “urgent” cross-border payments.
These monetary transfers take place via WeChat Pay, which offers a fast payment service that’s difficult to trace and reverse. The platform also provides a largely closed ecosystem. Identity details and conversation histories exist inside Tencent’s environment, which can make cross-border investigation and recovery slow. As a result, shifting victims from email into WeChat is now a core tactic in many China-linked fraud operations.
How Cybercrimals Use WeChat to Defraud Their Victims
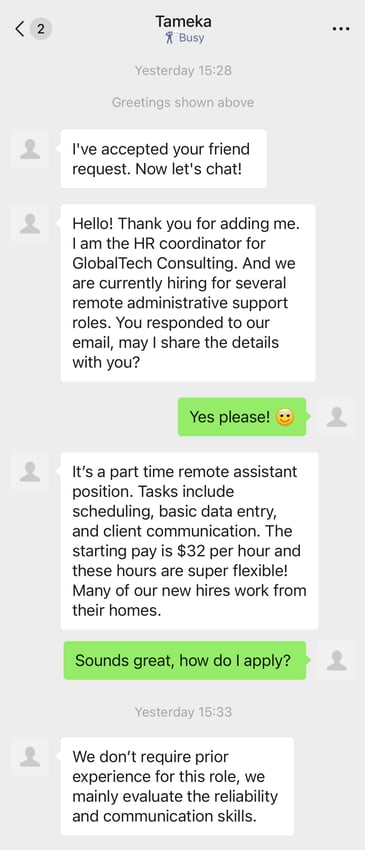
KnowBe4 Threat Labs engaged directly with the attacker to better understand the nature of the social-engineering payload.
The following screenshots capture this interaction and reveal that the campaign was an attempt to defraud victims through a fake job-recruitment scheme.
 |
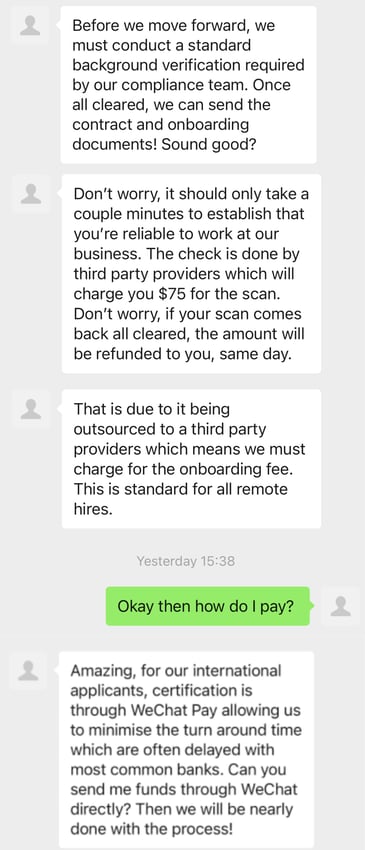 |
Example of a WeChat social engineering attack.
After moving the victim into WeChat, the attacker attempted to extract money under the guise of a “refundable background check” required for employment. The small amount requested ($75) is intended to appear routine and avoid raising the target’s suspicions. Additionally, if a victim pays, the cybercriminal knows they may be susceptible to future extortion.
Like the above email, the attack is written in fluent English, with the cybercriminal creating a detailed pretext about why the funds are required and need to be transferred using WeChat Pay. The same day moneyback guarantee for a clean background check can further incentivize the target, especially if they believe the check won’t disclose anything.
Phishing Toolkit That Simplifies WeChat Attacks
This attack leveraged an SMTP bulk-sending phishing toolkit commonly referred to as a 邮件群发器 (“mass-mailer” or “bulk send tool”). This kit is designed to send extremely high volumes of templated phishing emails while automatically rotating sender identities, spoofed domains and message formats to evade traditional email security filters.
The emails our Threat Lab team analyzed showed several strong fingerprint indicators.
|
Fingerprint Observed |
Description |
Indicated Toolkit Behavior |
Confidence |
|
Polymorphic From-address |
Randomized sender names + disposable domains (e.g., short. site domains) |
Automated sender rotation feature in Chinese “群发器” mass-mailing kits |
High |
|
Synthetic Domain (no SPF/DKIM/DMARC) |
Domain appears machine-generated and not configured for authentication |
Bulk SMTP kits using auto-registered or throwaway domains; no authentication setup |
High |
|
Base64-encoded HTML body |
Entire message body encoded in Base64 with simple HTML template |
Matches Python SMTP群发器 script output that wraps templates in Base64 |
High |
|
MIME boundary format (===============__...) |
Boundary string has double underscores and specific structure |
Matches Python email.mime.multipart default format used in Chinese bulk-mailer variants |
High |
|
Header ordering irregularities |
Message-ID, boundaries, and content headers appear in non-standard sequence |
Characteristic of “DIY” Chinese spam kits using Python libraries rather than commercial mailers |
Medium |
|
Message-ID not tied to sending domain |
Random ID not associated with the spoofed domain |
Indicates use of Python’s email.utils.make_msgid() in SMTP spam scripts |
High |
|
Chinese-language encoded subject fields |
UTF-8 Base64-encoded subject, typical of Chinese spam templates |
Common in Chinese mass-spam kits designed for international campaigns |
High |
|
Template-style email body with QR placeholder |
HTML layout designed for swapping in images (e.g., WeChat QR) |
Indicates prebuilt template system found in Chinese funnelling kits (“引流套件”) |
High |
|
No phishing link only QR to WeChat |
Email designed to migrate victim into WeChat, not to a website |
Matches “WeChat lead funnel” kits used in job, romance, and investment fraud |
High |
Beyond these technical artefacts this campaign contained characteristics closely aligned with Python-based SMTP “群发器” tools and tutorials widely shared on Chinese-language developer platforms (commonly sold on Chinese Telegram and QQ channels).
A widely referenced tutorial on Tencent Cloud Developer demonstrates these exact techniques, including constructing MIMEMultipart messages, embedding HTML templates, and authenticating to SMTP servers using simple username/password credentials—mirroring the structure of the phishing emails observed in this campaign.
GitHub also hosts openly accessible projects that support bulk or spam-style SMTP sending, including “A Simple SMTP Server to send email (spam?)”, “Python Script for Email Bombing which supports Gmail, Yahoo, Hotmail/Outlook”, “python-smtp-mass-mailer”, and several Chinese-language repositories labelled as “邮件群发工具”.
These scripts routinely incorporate the same primitives Python-generated MIME boundaries, rudimentary header construction, disposable SMTP account support and high-volume looping that appear in the phishing samples. While the specific script used in this attack cannot be identified, the overlap in methodology strongly suggests that the operator relied on a commonly circulated Python SMTP 群发 script sourced from this environment of tutorials and mass-sending examples.
Defending Your Employees and Organization From WeChat Phishing (Quishing) Attacks
Much like other third-party platforms, it’s difficult for organizations to monitor and secure WeChat. As the app’s global presence continues to grow, then, it’s becoming increasingly important that organizations can detect an initial WeChat-themed phishing email before the attack moves platforms.
Our Threat Lab team has analyzed multiple WeChat phishing toolkits (alongside the one outlined here) and all contained techniques, such as automatically rotating sender identities and spoofed domains, designed to evade traditional secure email gateways and native defenses.
Consequently, organizations need to ensure they also use advanced email security, such as KnowBe4 Defend, to detect inbound attacks. These products utilize AI-driven detection technologies like natural language processing (NLP) and natural language understanding (NLU) to identify linguistic markers of phishing, including atypical requests and manipulation, such as urging a target to connect on a third-party platform to discuss a job offer. Additionally, it’s crucial that the product takes a zero-trust approach to detect attacks regardless of the domain they’re sent from.
Finally, it’s important to consistently raise awareness of WeChat as a potential channel for cybercrime. This can be done through traditional awareness campaigns and training but real-time nudges and coaching, such as context-aware phishing banners, provide a powerful tool in building vigilance.
By combining tools and training, organizations can combat the growing threat presented by cybercriminals exploiting WeChat.
 With KnowBe4 Defend you can:
With KnowBe4 Defend you can:

