 Lead Analysts: Jeewan Singh Jalal, Prabhakaran Ravichandhiran and Anand Bodke
Lead Analysts: Jeewan Singh Jalal, Prabhakaran Ravichandhiran and Anand Bodke
KnowBe4 Threat Labs recently examined a sophisticated dual-vector campaign that demonstrates the real-world exploitation chain following credential compromise. This is not a traditional virus attack. Instead of deploying custom viruses, attackers are bypassing security perimeters by weaponizing the necessary IT tools that administrators trust. By stealing a “skeleton key” to the system, they turn legitimate Remote Monitoring and Management (RMM) software into a persistent backdoor.
Phishing Attack Summary
- Vector and Type: Email Phishing / Dual-vector attack that moves from credential harvesting to full system takeover
- Techniques: brand impersonation, credential harvesting, RMM deployment
- Bypassed SEG detection: Yes
- Targets: Organizations globally
The Two-Wave Attack Strategy
This campaign operates in two distinct waves: first by harvesting credentials through fake invitation notifications, then weaponizing those credentials to deploy legitimate RMM software that establishes persistent backdoor access to victim systems.
Wave 1: Credential Harvesting
The attack begins with a phishing email disguised as a Greenvelope invitation. Because Greenvelope is a legitimate service used for corporate events and weddings, the “Social Engineering Indicators” are subtle. Victims who click the invitation are directed to a highly convincing spoofed login page designed to capture their credentials.
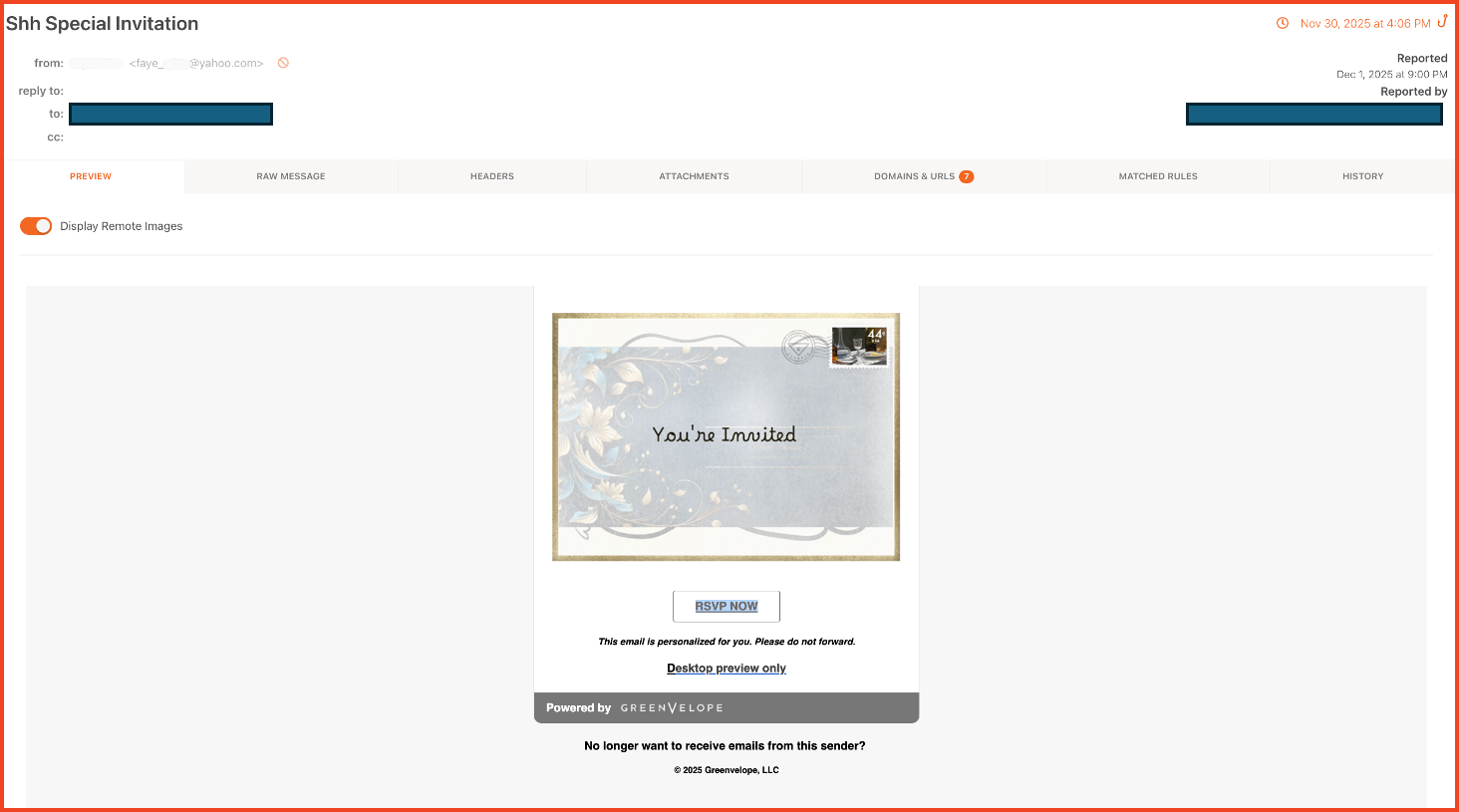
Example of a fake GreenVelope invitation phishing email used to harvest victim credentials in Wave 1 of the attack.
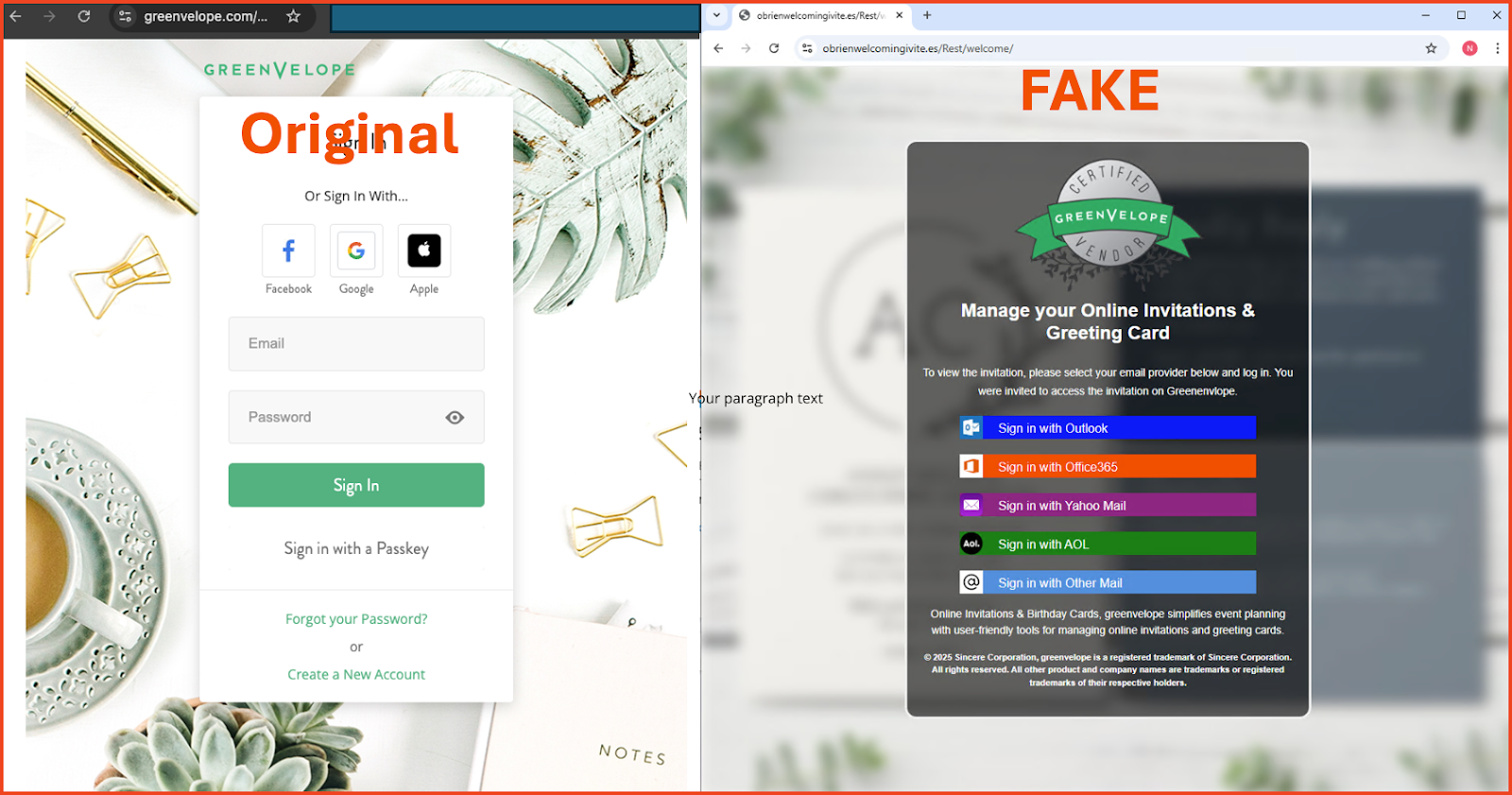
Example of an original GreenVelope login page compared to the spoofed login page.
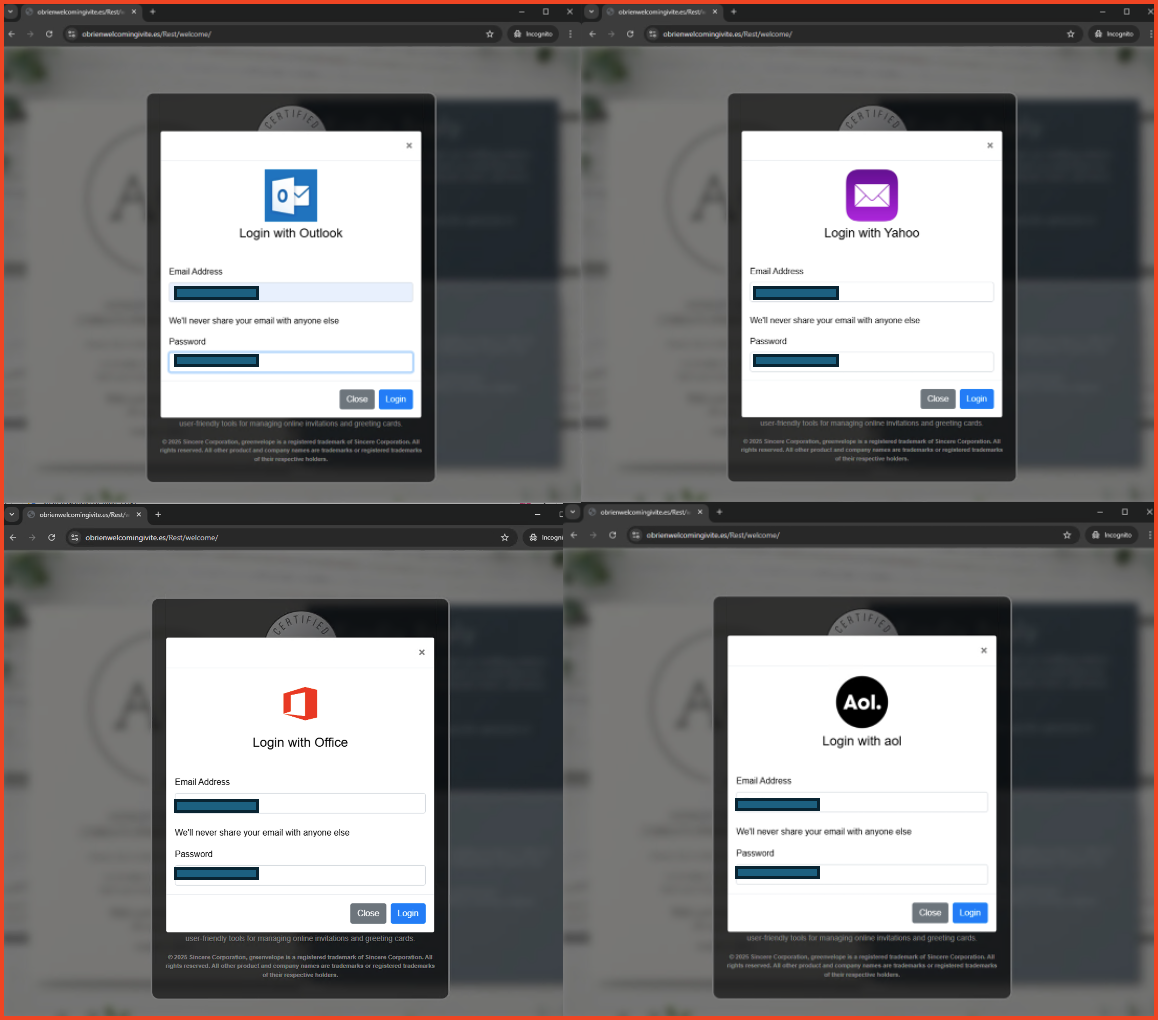
Grid of four phishing landing pages, each designed to harvest user credentials by impersonating well-known email and technology service providers.
The success of Wave 1, the theft of valid credentials, is not the ultimate end goal; it is the enabling step for the highly-advanced Wave 2 of this attack strategy.
Wave 2: RMM Deployment
For the attacker, a valid password is not the end goal—it is the delivery mechanism. Once credentials are secured, the threat actors generate legitimate RMM access tokens. These tokens are then deployed in follow-on attacks through a file called “GreenVelopeCard.exe” to establish persistent remote access to victim systems.
How the Attack Works
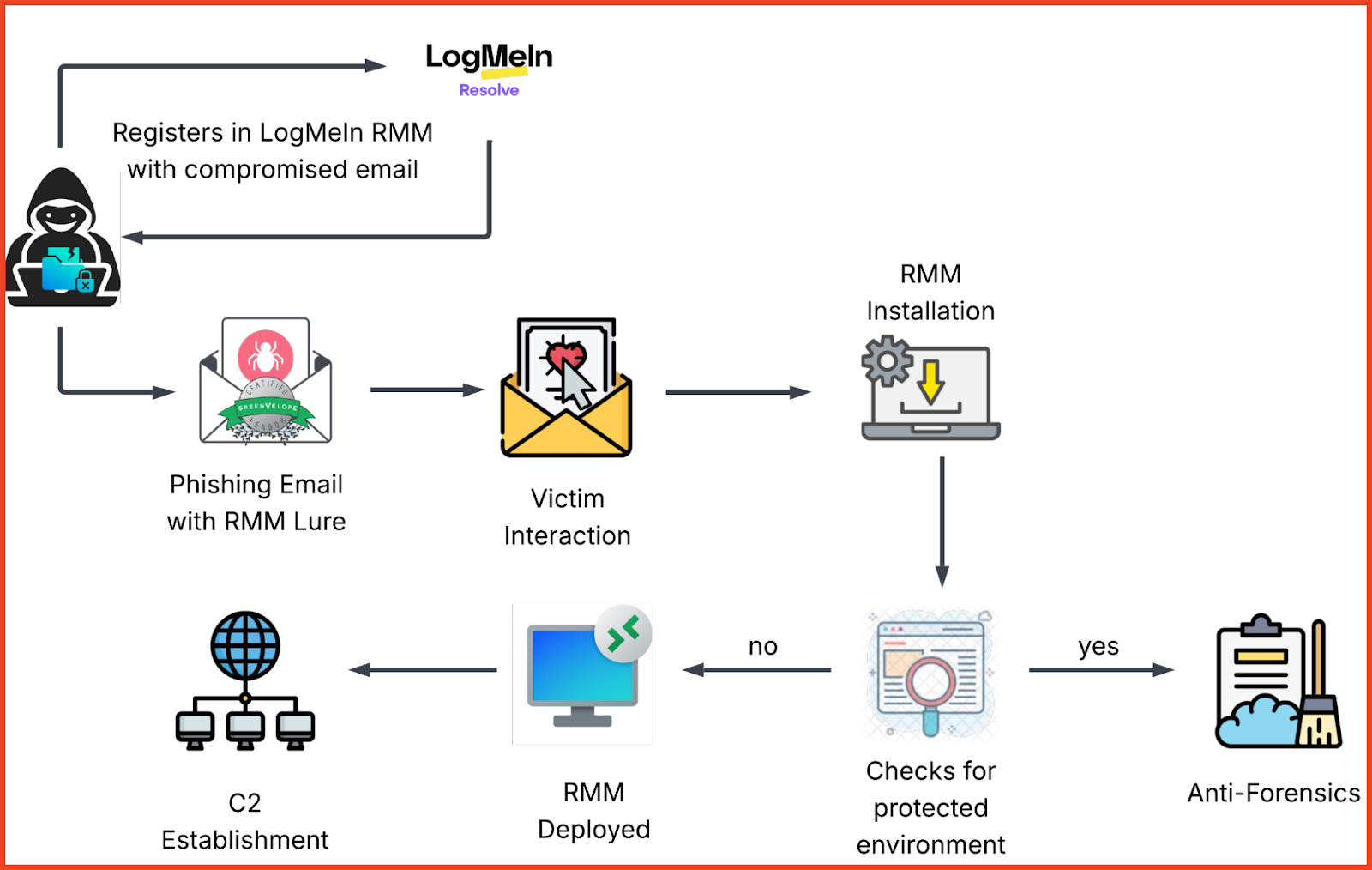
Complete attack flow showing the two-wave progression from credential theft to RMM deployment and persistent access.
Delivery Method: Fake GreenVelope Invitation Emails
Initial Payload: GreenVelopeCard.exe
Legitimate Signer: GoTo Technologies USA, LLC
RMM Tools Deployed: GoTo Resolve, LogMeIn
Threat Level: CRITICAL - Persistent remote access with credential dumping capabilities
The use of legitimately signed software from a trusted vendor allows the malware to bypass many security solutions that rely on signature-based detection.
Technical Analysis
The GreenVelopeCard.exe file serves as the primary orchestrator. Analysis has revealed that it contains a JSON configuration file with seven critical command line arguments that configure the RMM installation:
- Company ID: Links to an attacker-controlled GoTo Resolve company account
- Installation ID: Registered with the attacker’s GoTo Resolve account
- WorkFolder: Uses the Company ID as a folder name for organization
- Environment: Connects to production servers:
- console[.]gotoresolve[.]com,
- Devices-iot[.]console[.]gotoresolve[.]com
- Application Type: Enables unattended operation with full capabilities (it runs without user interaction, operates silently in the background, and provides remote control)
- Language: Logs written in English
- Website URL: Primary Command and Control (C2) endpoint for the RMM installation
- Main Domain: console[.]gotoresolve[.]com (official GoTo Resolve infrastructure)
- Subdomain: devices-iot (IoT/device management console)
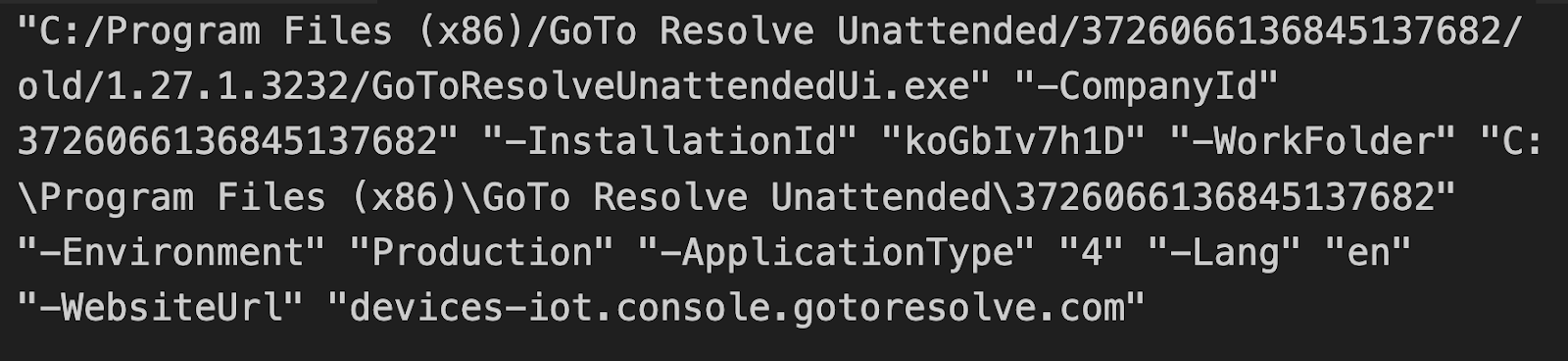
Seven command line arguments extracted from GreenVelopeCard.exe showing attacker-controlled configuration parameters.
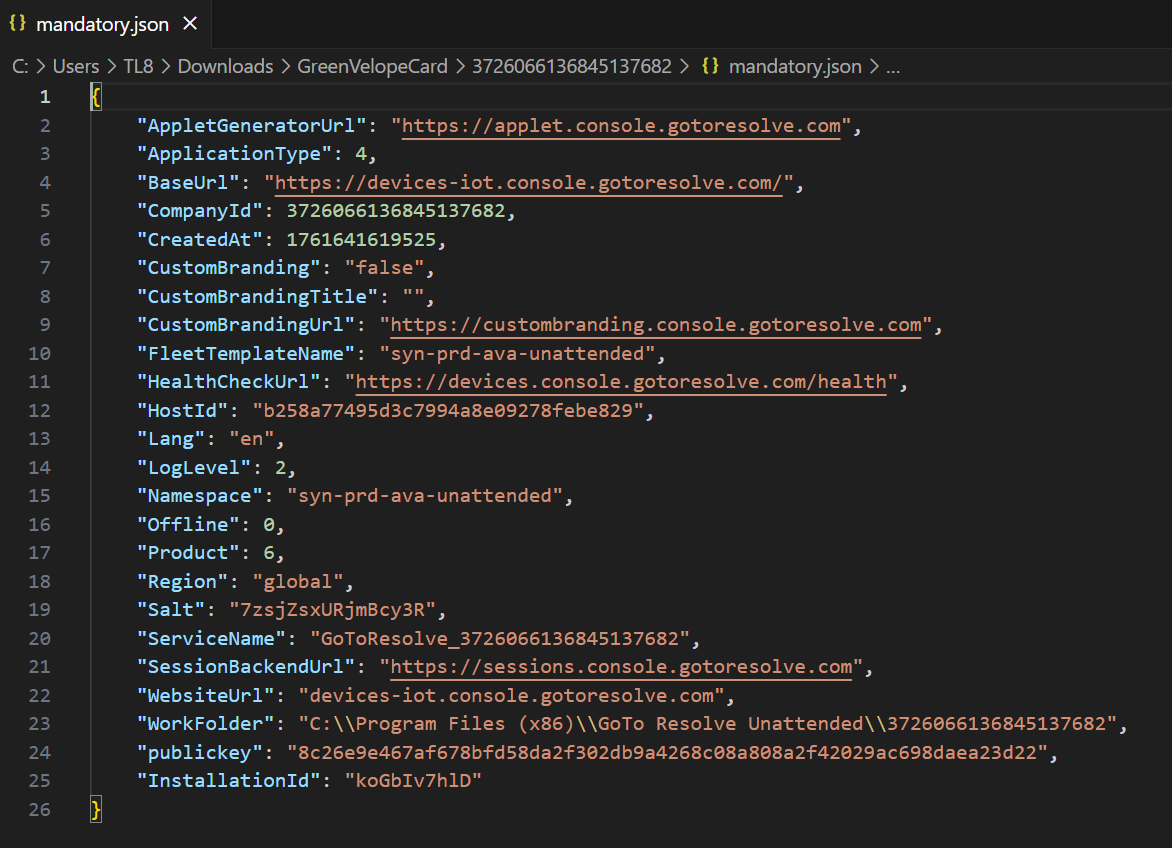
JSON configuration file embedded within the GreenVelopeCard.exe file dropper.
In essence, this JSON file acts as the attacker’s pre-programmed deployment script. It can tell the legitimate GoTo Resolve application to install itself silently, connect to the attacker’s private network, and run with full, remote control capabilities. This all happens without the victim or most security systems ever realizing a legitimate tool is being criminally weaponized.
Privilege Escalation: Gaining the “Master Key”
Once the RMM tool is on the system, the attackers move to secure SYSTEM-level privileges. This is the difference between having a key to a single room and having the master key to the entire building.
- Registry Manipulation: The attackers alter Windows service settings for GoTo Resolve, forcing it to run with unrestricted access to system resources.
- COM API Backdoors: The campaign establishes hidden scheduled tasks via the Windows COM API. These tasks ensure the RMM tool restarts even if a user manually kills the process.
- Service Abuse: By using the Windows Service Control Manager (services.exe) to launch components, the malware inherits the trust of the operating system.
Network Communication: Hiding in Plain Sight
The most effective part of this campaign is its “Command and Control” (C2) strategy. By using official production infrastructure, the malicious traffic is nearly indistinguishable from everyday business operations.
|
Endpoint |
Evasion Strategy |
|
dumpster.console.gotoresolve.com |
Uses encrypted HTTPS on GoTo’s official production servers. |
|
dumpster.dev01-console.gotoresolve.com |
A secondary "development" channel used for redundancy. |
|
settings.cc |
A fallback domain used to deliver updated configuration scripts. |
Turning Intelligence into Action
In the face of rapidly evolving tactics, security teams can no longer afford a “wait and see” approach to user education. Organizations must move quickly to counter these sophisticated threats. Human Risk Management (HRM) provides the framework to do this by dismantling the traditional silos between threat research and user awareness.
A HRM platform continuously synthesizes behavioral data, product telemetry, and real-time threat intelligence to generate highly accurate risk scores for each individual user. This data-driven approach allows for the platform to automate technical controls and hyper-personalized training to intervene and coach users when they need it most.
The most effective way to build this defense is by transforming real phishing attacks—like the “Greenvelope” attack—into de-fanged phishing simulations. This will provide highly accurate training that will equip users to identify and report sophisticated threats in real-time.
Defensive Measures: Strengthening Your Perimeter
To mitigate the risk of RMM-based attacks, security teams should prioritize the following immediate actions:
- Hunt for provided Indicators of Compromise (IOCs) in your environment
- Block identified C2 domains at the network perimeter
- Monitor for unauthorized RMM installations and usage patterns
Indicators of Compromise (IOCs)
The threat landscape evolves rapidly. For the most current list of domains, hashes, and behavioral signatures related to this campaign, please refer to the latest intelligence update from KnowBe4 Threat Labs.
View the full IOC list on X:
https://x.com/Kb4Threatlabs/status/1996210706258313663?s=20
For real-time updates and ongoing threat intelligence, follow the KnowBe4 Threat Lab analysts on X: @Kb4Threatlabs

