 During my travels, the topic of security operations comes up often. And nearly every security professional I talk to is either contemplating or already implementing some form of centralized security operations. Generally called a Security Operations Center (SOC), it is sometimes referred to as a Cyber Defense Center (CDC) or Security Incident Response Team (SIRT). Whatever the naming convention, it all boils down to having a designated set of eyes and ears in the organization focused on cybersecurity. It definitely is a hot topic. And not one as simple as most people think.
During my travels, the topic of security operations comes up often. And nearly every security professional I talk to is either contemplating or already implementing some form of centralized security operations. Generally called a Security Operations Center (SOC), it is sometimes referred to as a Cyber Defense Center (CDC) or Security Incident Response Team (SIRT). Whatever the naming convention, it all boils down to having a designated set of eyes and ears in the organization focused on cybersecurity. It definitely is a hot topic. And not one as simple as most people think.
Generally, people understand a SOC to be the combination where all cybersecurity personnel, threat detection, incident response and supporting security technologies come together. It is the place where security related data is collected, interpreted, enriched and made actionable. It is that locked door behind which all those people wearing hoodies watching screens with computer code while combating the forces of evil.
SOCs rely, for a large part, on the data they collect. Without it, they are ‘blind’. Usually this is a combination of internal and external sources. Often, it’s Petabytes of commercial and Open Source data in various forms and formats, all aimed at providing cyber intelligence to the organization in order to better protect it. Now this seems simple enough, but very few actually understand what this implies.
Data Itself is Not Enough
First off, data is not the same as intelligence. Data in itself is just a raw building block which lacks context or meaning. It becomes information when you apply structure and order to it. Information is already useful in a SOC. But the true value comes when you keep adding information together to get intelligence. In the cybersecurity realm, we refer to this as threat intelligence.
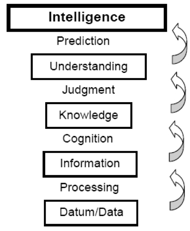 When it comes to threat intelligence, it’s all about adding the context of ‘how’, ‘what’ and ‘why’ to information. How did they attack? What were they after? Why did the attacker employ specific techniques? In the end, an organization needs context to enable its organization to make a decision. Strategically, tactically, operationally and most important of all, quickly. Because dealing with an actual threat is a race against time. Every second counts when an invader has gained access to your infrastructure and is trying to access valuable information that might put your organization at risk.
When it comes to threat intelligence, it’s all about adding the context of ‘how’, ‘what’ and ‘why’ to information. How did they attack? What were they after? Why did the attacker employ specific techniques? In the end, an organization needs context to enable its organization to make a decision. Strategically, tactically, operationally and most important of all, quickly. Because dealing with an actual threat is a race against time. Every second counts when an invader has gained access to your infrastructure and is trying to access valuable information that might put your organization at risk.
The Journey of a SOC
Most SOCs are rooted in a technical background, meaning that they employ analysts that often come from a technical background.
Because of this, most SOCs therefore start out by collecting data from technical preventive measures such as firewalls, network switches, anti-virus/anti-malware and other technical systems. This is reinforced by a lot of the current supporting security products (e.g., SIEM, EDR, etc.) on the market. These products focus on helping SOCs understand technical systems.
Once internal data sources are set up, the next stage for a SOC is often to augment this data with (external) threat intelligence feeds. And if we move even higher in the maturity model for SOCs, we see things like process monitoring, third-party monitoring, and risk assessment. Generally speaking, a SOC will always be on the lookout for more information to enrich its existing view of the threat landscape.
Introducing the Human as Threat Intelligence
My colleague Roger Grimes wrote in his blog post titled I Can Phish Anyone, how social engineering and phishing are responsible for 70% to 90% of all malicious data breaches. And how only unpatched software came in as the closest second -- responsible for 20% to 40% of hacks. Everything else only accounts for 1% of all hacks.
This means that humans are directly leveraged as a credible attack vector by the bad guys!
Knowing this, I’ve never quite understood why most SOCs I’ve seen over the course of nearly two decades in the industry, tend to overlook the human factor as a credible source of threat intel. If 70% to 90% of all malicious data breaches use social engineering, then why don’t we utilize the information on security behavior and culture within our organization? Wouldn’t it present us with new intelligence which would allow a SOC to better protect our organization, including the digital welfare of our employees? Aren’t we all taught that a good security practice focuses on technology, processes AND people combined?
I do understand part of the reason why the human factor can be difficult. Humans are different from technology and processes because they can be very hard to predict. Our actions and reactions don’t always follow reason or logic. At least not in the way machines are programmed to follow a predetermined pattern. Emotions can be tricky like that.
Privacy laws don’t make it easy on us either because they prevent us from gathering data we need for proper forensic analysis because it infringes on the privacy of people. Now don’t get me wrong, I am all for privacy. However, from a forensic perspective, it makes privacy harder. And it becomes even harder when you realize that most of the data about human behavior isn’t registered anywhere at all, since a lot of the things we do happen in the physical domain, outside of the reach of digital monitoring systems.
And many security analysts simply want to give up when they see how utterly frail humans are and how many countless ways there are in which we can be hacked.
But all is not lost! No, it isn’t easy. But sometimes, when all seems against you, even the smallest success can be a victory. There are ways to monitor the human factor. Albeit it means you have to think outside of the metaphorical ‘box’.
Training has proven to be the most effective way to create security awareness for users. It helps the user make smarter security decisions. It helps protect organizations against attacks that evade technical security measures, and boosts security maturity across the board.
Combine this training with effective reporting, and you have you have a formula for positively influencing the security behavior of users. This in itself is already a very powerful weapon for organizations in their battle against the forces of evil.
And it is in the reporting where the added value for a SOC lies. Or to be more exact, it’s the information behind the reports that are of great value to a SOC.
For instance, the data will tell you which users are more prone to phishing. And therefore, if an attack is detected that focuses on a specific user, you can use this information as a risk indicator to determine what actions are appropriate. This way, raw data about attack vector effectiveness for a specific user can be correlated with technical information about an attack and combined with a risk value for the organization. This will tell you ‘when’ you need to pay attention, ‘how’ the attack is most likely to pan out, and ‘what’ attack techniques you need to be extra aware of. And because you’ve added a risk value associated, you can take appropriate mitigation actions.
 Here's how it works:
Here's how it works:




