 Cybercriminals are quick to exploit seasonal events — and tax season is no exception. It’s a yearly honeypot for cybercriminals, who take advantage of heightened stress, tight deadlines, and sensitive financial data.
Cybercriminals are quick to exploit seasonal events — and tax season is no exception. It’s a yearly honeypot for cybercriminals, who take advantage of heightened stress, tight deadlines, and sensitive financial data.
With deadlines looming across the US and EU, our Threat Labs team observed a 27.9% increase in phishing attacks in March 2025 compared to the previous month — many of which contained financial-themed payloads.
These emails used social engineering tactics, finance-related language and advanced obfuscation techniques in attempts to steal sensitive information or manipulate recipients into sending money.
In particular, KnowBe4 Defend identified a sharp spike in tax-related phishing activity on March 14, 2025, with 16% of all phishing emails processed that day containing the word “tax” in the subject line. Interestingly, only 4.3% of these tax-themed phishing emails were sent from free email services.
Nearly half of all identified attacks (48.8%) originated from compromised business email accounts, while 7.8% leveraged the legitimate QuickBooks service, as observed in previous incidents. Additionally, the majority of these attacks were sent from aged domains (100 days or older), employing tactics specifically designed to enhance legitimacy and bypass traditional security filters, such as secure email gateways (SEGs).
All attacks analyzed from this campaign were identified and neutralized by KnowBe4 Defend and analyzed by our Threat Labs team.
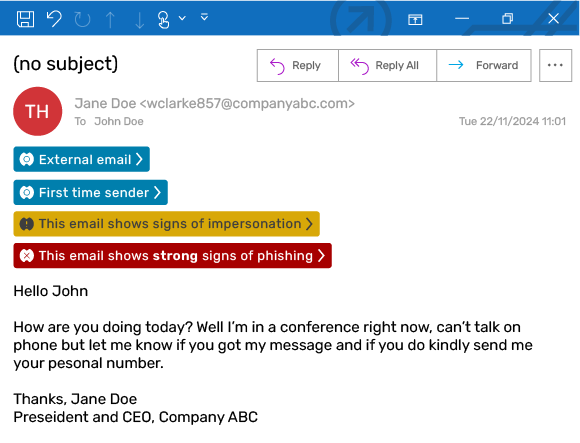
Tax-Related Phishing Attack Example:
In this example, the cybercriminal has impersonated a lawyer from a reputable law firm to deliver a fake tax return. The phishing attack is designed to harvest Personally Identifiable Information (PII), specifically targeting sensitive data such as addresses and Social Security Numbers. A link embedded within a QR code directs victims to a fraudulent form crafted to capture this information and facilitate identity theft. To enhance the email’s legitimacy and deliverability, attackers employ a variety of tactics, including QR code obfuscation, polymorphic elements, and lookalike domains.
Screenshot of tax-related phishing email sent from a lookalike domain, with KnowBe4 Defend anti-phishing banners applied
Screenshot of QR code payload found within the email attachment
Tactic One: Embedding a QR Code in an Attachment
Above is an example of a financial-themed phishing attack leveraging the word “tax” in the subject line. In this case, the email delivers a fake tax return embedded within a DOCX file containing a QR code that conceals the malicious payload — an obfuscation technique designed to bypass traditional security tools. Detecting the malicious payload requires advanced technologies that can scan attachments and analyze both hidden content and social engineering cues within the email body.
If the recipient were to open the attachment and scan the payload, this would also move the attack away from a secure work device and onto a mobile device that likely lacks proper security protocols.
Tactic Two: Polymorphic Subject Lines and Attachment Names
These attacks also featured a variety of polymorphic elements across the email’s subject line, display name, body, and attachment, which could be tailored to the recipient. For example, the attachment name may adjust to reflect the recipient’s company, while its content could vary based on the recipient’s location or email preferences.
In the example above, the cybercriminal has included randomized characters in the subject line, display name and reference number, making mass remediation much more difficult for IT and security teams. This customization is easily automated using scripts or phishing toolkits, allowing attackers to tailor each email for better credibility. In some cases, attackers may even leverage AI to generate these polymorphic elements, allowing them to churn out personalized attacks at scale.
Tactic Three: Lookalike Email Domains
The attacker sent the phishing email from a lookalike domain mimicking a legitimate US legal service, with only minor character changes. Because this was a lookalike — not a direct spoof — the domain could be easily registered and was able to bypass traditional SEG controls that rely heavily on domain reputation. This particular domain was also over 1000 days, helping the attack bypass authentication checks.
How Should Organizations Respond?
Cybercriminals will continue to exploit seasonal events to launch increasingly sophisticated phishing attacks. To counter these threats, organizations should utilize advanced security technologies capable of conducting a holistic analysis of all email elements — like language, tone, subject lines, and attachments analysis in this case — to identify subtle indicators of malicious intent. In parallel, organizations need to implement targeted and relevant training programs that equip employees with the knowledge to pre-empt these attacks and respond accordingly.
When it comes to tax-related phishing, attackers are banking on the chaos of the season — but a well-prepared organization that leverages appropriate technology, training and policies should leave them empty-handed.
 With KnowBe4 Defend you can:
With KnowBe4 Defend you can:
