 It's all over the press. Here is a quote from Reuters: "Yahoo Inc said on Thursday information associated with at least 500 million user accounts was stolen from its network in 2014 by what it believed was a "state-sponsored actor."
It's all over the press. Here is a quote from Reuters: "Yahoo Inc said on Thursday information associated with at least 500 million user accounts was stolen from its network in 2014 by what it believed was a "state-sponsored actor."
The data stolen may have included names, email addresses, telephone numbers, dates of birth and hashed passwords (the vast majority with the relatively strong bcrypt algorithm) but may not have included unprotected passwords, payment card data or bank account information, the company said.
Right, that is how it usually goes. This whole disclosure smells like a professional crisis-handling exercise. Later, after more breach-investigation, they disclose that more credentials were stolen and that more data (credit cards) was exfiltrated than was known at the time of the discovery. It is disappointing that Yahoo doesn't share more details about the hack, when it first discovered that it had been attacked.
And it's easy to blame Russia (likely) or China (unlikely) If I had to break the bad news that my company had been hacked, I would feel much happier saying that the attackers were "state-sponsored" than a bunch of 15-year-old script kiddies in their parents' basement.
"The investigation has found no evidence that the state-sponsored actor is currently in Yahoo's network," the company said. "Yahoo said it was working with law enforcement on the matter. It was not clear how this disclosure might affect Yahoo's plan to sell its email service and other core internet properties to Verizon Communications Inc.
Yahoo launched an investigation into a possible breach in early August after a Russian hacker named "Peace" offered to sell a data dump of over 200 million Yahoo accounts on the darknet for just $1,800 including usernames, easy-to-crack password hashes, dates of birth and backup email addresses.
This is a phishing paradise with significant fallout
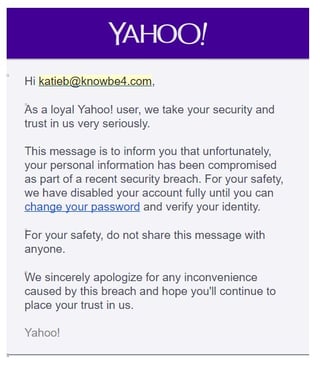
Yahoo put a security announcement on their website and has started to send users notices that they need to change their password. Here is an example and they make the classic mistake to use direct links in the email. Bad guys are just going to say Thank You and rip it off:
Subject: Your Yahoo accountThe security of your Yahoo account, [Name], is important to us. Out of an abundance of caution, we are asking you to change your password. We are committed to protecting the security of our user's information, and we take measures like this when appropriate in light of reported security issues or suspicious activity on an account.We encourage you to take the following steps:1. Sign into your account and change your password:2. Visit our Help Page for information on safeguarding your account:OrStart using Yahoo Account Key and never get locked out from forgetting or losing your password. Yahoo Account Key is a convenient way to control access to your account, and it's more secure than a traditional password because once you activate Account Key - even if someone gets access to your account info - they can't sign in.Yahoo
The bad guys are going to have field day with this, warn your users
Warn your users, friends and family. They will be confronted with a raft of Yahoo-related scams in their inbox. The bad guys are going to leverage this in a variety of ways, starting with the template above but with masked links so that if you click on it you wind up on a compromised site which could steal personal information and/or infect the computer. The variations are infinite, but the defense against it is relatively simple.
I suggest you send them something like the following and feel free to copy/paste/edit:
"Yahoo announced that 500 million of their accounts were hacked and are sold by internet criminals. Bad guys are going to use this information in a variety of ways. For instance, they will send phishing emails claiming you need to change your Yahoo account, looking just like the real ones. Here is what I suggest you do right away:
- Open your browser and go to Yahoo. Do not use a link in any email. Reset your password and make it a strong, complex password or rather a pass-phrase.
- If you were using that same password on multiple websites, you need to stop that right now. Using the same password all over the place is an invitation to get hacked. If you did use your Yahoo passwords on other sites, go to those sites and change the password there too. Also change the security questions and make the answer something non-obvious.
- Use a free password manager that can generate hard-to-hack passwords, keep and remember them for you.
- Watch out for any phishing emails that relate to Yahoo in any way and ask for information.
- Now would also be a good time to use Yahoo Account Key, a simple authentication tool that eliminates the need to use a password altogether.
 If you are a KnowBe4 customer, we have a new template in the Current Events Campaign which I suggest you send to all your users immediately.
If you are a KnowBe4 customer, we have a new template in the Current Events Campaign which I suggest you send to all your users immediately.
The timing could not be worse for Yahoo, which is trying to sell itself to Verizon. Stephen S. Wu, a technology lawyer at the Silicon Valley Law Group, said the language assuring that no security breaches had occurred might give Verizon leverage to renegotiate the deal, or even to walk away.
This "bad timing" might not be a coincidence and would again point to Russia who release strategic hacking information regularly. The last 12 months Russia has basically taken over China’s position as culprit #1 that attacks U.S. systems. Two hacking groups—linked by security researchers and U.S. government officials to Russia—have published email messages belonging to public figures and the Yahoo database data could very well be used to get the personal email of public figures.
“For a government, the real value would be to look for people with real value,” said Matthew Green, a computer science professor at Johns Hopkins University. “Maybe you don’t get classified information, but some of those Colin Powell emails were very interesting.”
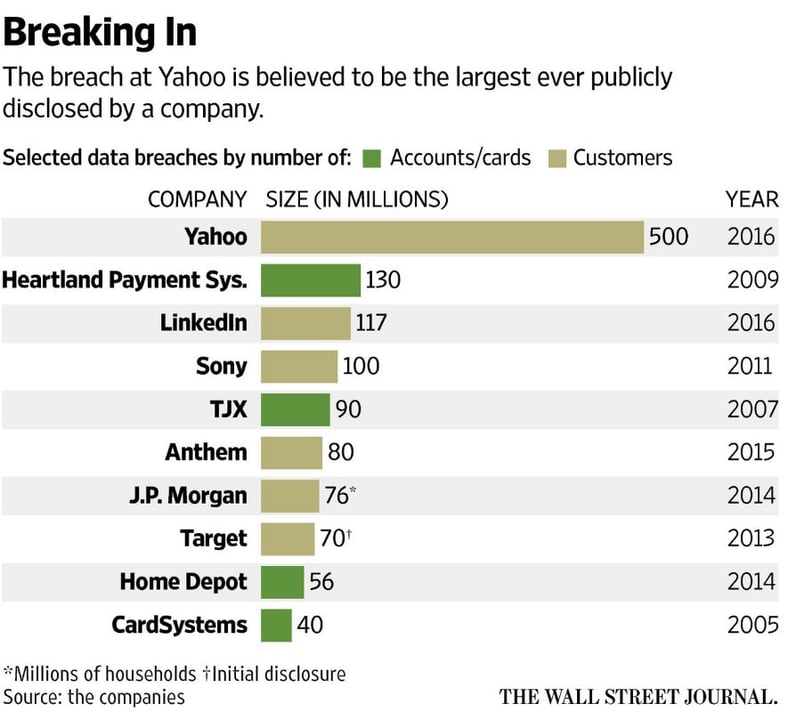
This is the largest hack ever, here is a graph fresh from an article in the Wall Street Journal that puts it in perspective. I suggest you send the link to your management. This is exactly the kind of thing that they want to prevent from happening and security awareness training is the number one thing that makes you much more hack-resistant since your users are your weakest IT security link.
Yahoo reported that they believe the user data was stolen in late 2014, yet they just disclosed the breach this morning. The amount of time a breach remains undetected is known as "Dwell Time". FireEye's Mandiant has reported average dwell times of 146 days. In the case of this Yahoo breach, it appears the hackers remained undetected for over 650 days. This high "dwell time" achieved by the hackers is remarkable since Yahoo has one of the most sophisticated security infrastructures in the world. As such, this breach should be an eye-opener to all other enterprises regarding the need for increased spending on security.
Yahoo gave no details of how the nation-state hackers infiltrated the company's network, but experts say the most likely vector was the old reliable spoofed spear phishing attack fooling a Yahoo employee with either a malicious attachment or link that then downloaded malware that got the attackers a foothold into its network.
Free Domain Spoof Test
Can hackers spoof an email address of your own domain?
Are you aware that one of the first things hackers try is to see if they can spoof the email address of your CEO? If they are able to commit "CEO Fraud", penetrating your network is like taking candy from a baby.
Would you like to know if hackers can spoof your domain? KnowBe4 can help you find out if this is the case with our free Domain Spoof Test. It's quick, easy and often a shocking discovery. Find out now if your email server is configured correctly, many are not!
Don't like to click on redirected buttons? Cut & Paste this in your browser:





