 I am not sure what is going on these days, but for several weeks, I have received far more SMS-based phishing (i.e., smishing) attacks than usual.
I am not sure what is going on these days, but for several weeks, I have received far more SMS-based phishing (i.e., smishing) attacks than usual.
Normally, I used to get one or two a month, but lately I have been getting at least one or two a day with no let up. My friends tell me the same. Here are some examples:
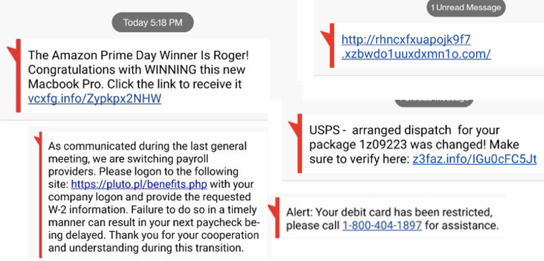
I am not sure if this is a temporary trend or a new normal? I posted this information and question on LinkedIn and was surprised to see some notable industry figures discount my recounting of the attempts and seriousness. I am not sure of all the motivations for discounting smishing attacks, but at least some of it seemed to be discounting them because they were more personal in nature, not as frequently occurring and did not directly target corporate organizations. Or perhaps it is because the typical smishing attempt is not as sophisticated as the typical email phish? So why worry?
But here is what I want you to know – Every organization and person needs to take smishing attempts very seriously.
For one, they are abundant, and work; sophisticated or not. A lot of people lose money. Here is an example from less than two weeks ago. In this case, two Indonesian men were arrested for successfully grifting over $60M using SMS-based phishing scams. It impacted over 30,000 U.S. citizens out of the over 200M citizens targeted. Two guys…200M malicious text messages…$60M in stolen money. And you know we only catch the stupid ones.
The biggest reason to try and prevent smishing attacks from being successful is that every skill that you teach someone how to recognize and correctly react to a smishing attack protects them and your organization. It reduces risk to both.
There are less controls and blocks preventing a malicious SMS message from getting to someone. Cell phones, for the most part, do not block any SMS messages like they might an identified spam call. Cell phone antivirus products do not check or block SMS messages either. There is not a service, that I know of, that looks at the embedded URL links before someone clicks on them. Most email systems have multiple levels of anti-phishing checks (at the gateway, at the email server, at the end user workstation) before the email makes it to an end user’s inbox. But with rare exceptions, every malicious SMS message ends up with an end user looking at it – potentially one click away from a bad experience.
It is harder to tell if a particular SMS message is legit or not. There are less clues. There are no email headers to check. They often arrive from fake phone numbers and what is known as SMS short codes (see example below).
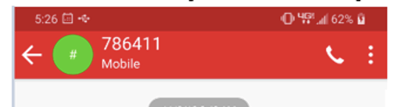
That is not a phone number! What are you supposed to do with that?
Note: Actually, you might be able to confirm a sending vendor by looking up the involved short codes to see if it is registered to the claimed vendor here.
Turns out phones and SMS are very poorly authenticated. And that is why smishing and vishing attacks are rising.
And we can be sure, just like what happened with email phishing, that smishing will increase in frequency and sophistication. Anyone remember email phishing when it was full of typos from people who spoke English as a tenth language? Those days are long gone. And the days of simple smishing attacks are starting to disappear. It is beneficial for you to now educate your employees about smishing attacks, how to spot them and how to treat them (which is to ignore and delete or report).
When you teach an employee or co-worker how to avoid getting phished via SMS, it benefits them, their family and your organization. The skills you teach them will protect your organization from similar attacks, when they do directly target your organization or your employee to get to your organization. Also, any time you help your employee avoid a personal attack, you help your organization. Not only does the employee know that you care about them and their family, but an employee not dealing with the consequences of personal financial and identity theft is a more productive employee better able to concentrate on your business. Plus, helping one another to avoid scams is just the right, human, kind thing to do.
So, I do not get business defenders who do not care as much about scams against people just because it possibly does not target the organization directly. We are all in this together, fighting the same criminals, whether they target an employee or a business. It is all one big human family and human firewall.
Preventing Smishing Attacks
In any case, this is what you need to tell your employees about SMS-based phishing messages. First, explain what SMS-based phishing is and give some popular examples (e.g., FedEx and Amazon messages seem to be very popular). Most people already know about SMS-based phishing, but I guarantee that a few people do not. I still have people come up to me at presentations and ask me what I meant by phishing, social engineering or patching. Do not assume that because you and 99% of the world knows something that everyone knows it.
Second, teach them how to recognize a smishing attack and how to treat it. This is what I tell my friends and co-workers about how to recognize any phishing attack, including an SMS-based phishing attack. If the message is unexpected, is requesting something new for the first time from the sender and if doing what the sender is requesting you to do could potentially harm you or your organization’s interests (i.e., they want you to provide confidential information or download a file), then slow down and investigate more before clicking.
Usually, the URL link is the biggest indicator of a smishing scam. Luckily, what you see in an SMS-based message is what you get. URL links cannot look like something and really be something else completely different when it is clicked, like what happens with larger devices and browsers. So, you do not need to “hover” over SMS URL links to see what they really are. What you see in an SMS message is really what the URL is. But the included URL link usually does not give you a lot of clues to work with. But if it is claiming to be a message from FedEx and does not include a fedex.com domain URL, then it is probably not from FedEx, and so on.
Learning how to tell the difference between a rogue and legitimate URL can help immensely. If you or your co-workers do not know how to reliably tell the difference between a malicious URL and a good one, consider watching my one-hour webinar on the subject here.
Many phishing SMS messages (and legit ones) have “shortened” URLs. A shortened URL is where the original, usually longer URL, is swapped out for a shorter one. And when the shorter one is clicked on, it redirects the clicker to the longer one. Many URL shortening services, like Bit.ly, started showing up around the time that Twitter, with its 140-character limitations on messages, started to get popular. Malicious senders like to shorten URLs so that a user cannot immediately inspect the real, eventual URL before clicking on it. So, any time you see a shortened URL, “expand” it first using a URL expander service.
Here is an example of a shortened URL that led to malware, that I expanded using one a URL expander service.
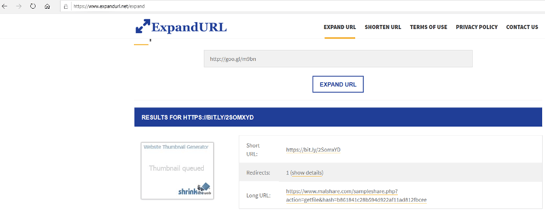
If an SMS message has the slightest chance of being a malicious phishing message, I NEVER click on the URL. Instead, I will open it up on an isolated virtual machine, that can only connect to the Internet and not my corporate network, running a browser. I will copy or re-type the URL (they usually are not long) and see what happens.
Usually, if I suspect a phishing attack, the typed in URL link quickly asks me for login information, other confidential information or tries to get me to download a document. If you are not sure if a URL is malicious or not, submit it to your favorite computer forensics person or antivirus service. Most antivirus services have a URL submission location for submitting suspected URLs for their review.
Simply educating people about the threat of smishing attacks and what they look like is enough to cause a significant decrease in risk, to the potential victim, their families and their organizations. So, do not blow off SMS-based phishing. It is coming on strong and likely to get much worse before it gets better. You can use this blog as a way to start some form of security awareness training about smishing attacks.



 Here's how it works:
Here's how it works:













